Securing identities for all levels of government
Secure access for identities on any device, anywhere at the right time. Protect sensitive data and critical infrastructure, across all levels of government with Zero Trust.
Identity security. The foundation to Zero Trust.
‘Never trust, always verify’ is imperative when examining the vulnerabilities created by the many entry points and pathways traversed by multiple identities. CyberArk provides the foundation to Zero Trust by offering governments the industry’s most complete Identity Security Platform. Your journey to Zero Trust starts here.
Contain attacks
Prevent attacks from progressing through a layered Identity Security strategy, centered on privilege controls
Ensure compliance
Address key regulations including NIST, NERC and FIPS standards
Addressing Zero Trust for federal agencies
Secure access for all identities across any device and protect sensitive government data and infrastructure for federal agencies.
Align to regulations and compliance standards with CyberArk
CyberArk is the global leader in Identity Security, trusted by more than 8,000 customers worldwide, a NIAP certified provider, part of the DoD UC APL and holder of a Networthiness certificate (CoN) provided by the U.S. Army. Follow the CyberArk Blueprint framework to design an effective Identity Security roadmap and address key regulations.

ISO 27018
This internationally recognized standard focuses on safeguarding personally identifiable information (PII) in cloud computing environments and demonstrates CyberArk’s priority to data privacy and maintaining transparency and accountability.

DORA
The Digital Operational Resilience Act (DORA) is intended to help EU financial sector organizations improve their resilience against cyberattacks. Overall, DORA places a key focus on securing information and communication technology (ICT). The act applies not only to financial firms, but also to third parties that provide the firms with ICT systems and services.

DoDIN APL
CyberArk Privileged Access Manager Self-Hosted has been officially listed as a trusted solution for Department of Defense (DoD) customers. CyberArk PAM Self-Hosted can be found on the DoD Information Network Approved Product List (DoDIN APL), meeting specifications for the DoD.
Securing Australian critical infrastructure then, now and what’s next
Learn more about manage national security risks of sabotage, espionage and coercion of Australia’s critical infrastructure.
Implement a layered identity security strategy
Strengthen your security posture and reduce exposure to dynamic threats.
Protect privileged access
Move away from long-standing high levels of privileged access to a more dynamic, just-in-time method for administrator access. Access to staff and contractors should be granted with minimal permissions to reduce the attack surface and blast radius, should a privileged account be targeted by malicious actors.

Secure endpoints
Compromised endpoints can be used by attackers to bypass strong authentication. As such, it’s essential to put controls in place that ensure only approved processes can access credential stores. This relies on the basic hygiene of implementing least privilege and removal of local admin rights at the endpoint.
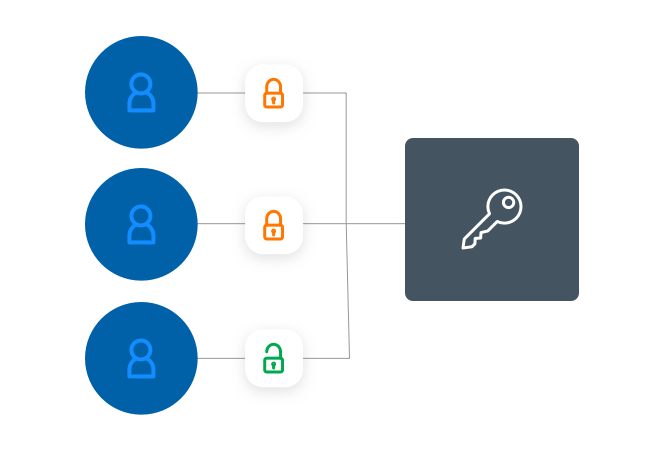
Secure application access
Strong, adaptive authentication and continuous approval and authorization provide the basis for securing staff access to applications. This shift from network controls to identity controls creates a better user experience and boosts productivity. Empower members of staff while keeping malicious actors out.

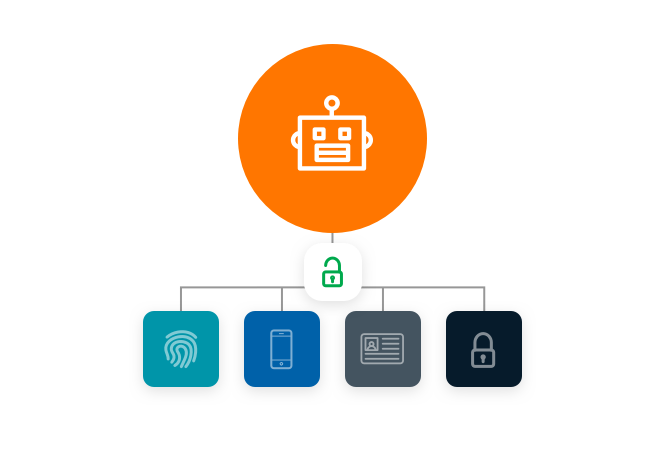
Secure non-human access requests
The ‘never trust, always verify’ mantra of Zero Trust must also encompass non-human identities (Non-Person Entities). All calls from these machine identities seeking access to network resources should be protected and secrets across the DevOps pipeline managed appropriately.
Customer stories
Hear from leading businesses and government agencies on their Identity Security success with CyberArk.
Identity security centered on
intelligent privilege controls

CyberArk named a Leader in the Gartner® Magic Quadrant™ for Privileged Access Management – again.
Explore
related
resources
Start your journey to Zero Trust
Enforce Zero Trust and least privilege, and seamlessly secure access for humans and machines across devices and environments.
Apply intelligent privilege controls to every form of identity to help isolate and stop attacks, protect critical assets and grant access for just the right amount of time.
Automate management of the identity lifecycle through seamless, no-code app integrations and workflows, taking control of excessive permissions.
Continually monitor for threats through real-time Identity Security intelligence, adjust controls based on risk, and leverage real-time remediation options.