
When 921 password attacks occur per second, it’s time to treat everyday employees’ credentials like the true operational risk they are.
Today’s attackers assign a level of value to employees’ passwords they once reserved for privileged users’ credentials. Why? Workers now have a shocking amount of access to sensitive resources. I’ll elaborate… but through the perspective of a chief information officer kept up at night by risks.
Here’s an example of what crosses a CIO’s mind at 2:30 a.m.
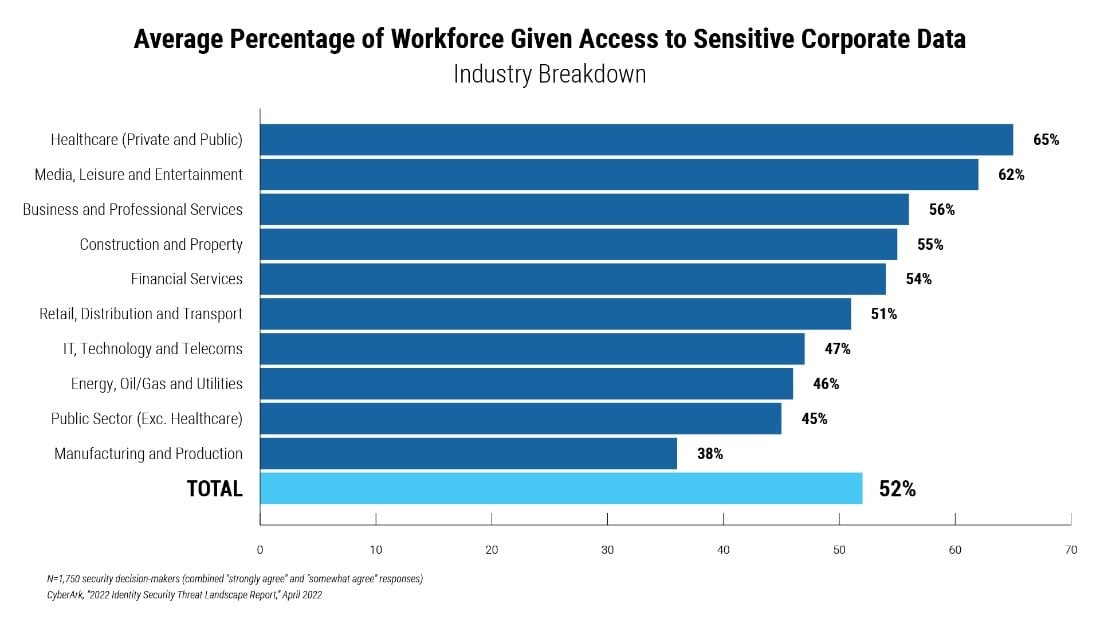
Fifty-two percent of employees have access to sensitive corporate data, according to a CyberArk survey of 1,750 security decision-makers from ten industries. In some sectors, that percentage is even higher:
- Six out of 10 (62%) employees in the media, leisure and entertainment industry, where the data may include millions of subscribers’ personal information
- Nearly two-thirds (65%) of employees in the healthcare sector, where the data may — again — include subscriber information, but this time for health insurance policies or patient records
What could happen if a single app is compromised in either industry? Lost trust, which can equal lost subscribers, revenue, market share and credibility among regulators.
As I calculate all of this (while I should be sleeping), what alarms me the most is what’s standing in between these sensitive resources and attackers who constantly target them:
- Passwords, which are a key contributor to the 82% of attacks stemming from “the human element” which includes the many unsafe ways employees create, store and share credentials.
- Tools for managing passwords that are designed for personal use, but often end up being used by entire enterprises — even though they typically lack basic security controls.
If attackers are treating employees’ credentials like they’re privileged, then so should we … right down to the specific ways enterprises secure how passwords are stored, shared, created and managed. In this post, I’d like to share my thoughts on strategic steps you can take to mitigate your organization’s password risks.
Understand Your Password Vulnerabilities with a Risk Assessment
My 25 years of experience in the Israel Defense Forces taught me how important a strategic risk assessment can be, including:
- The risks you face.
- The probability and likelihood of attacks.
- The gaps that make your organization vulnerable.
Why start with such an essential assessment? I recall a major cyber exercise from years ago — this approach helped me make a calculated decision that would affect the organization’s operational continuity.
Focusing on passwords, let’s start with what we know.
Many widely used applications are incompatible with — and therefore not protected by — your single sign-on (SSO) tool. They also don’t use modern identity protocols. This includes popular apps for virtual collaboration, banking and shipping.
We also know that employees often access these unprotected apps through one of two methods:
- Passwords created with little attention to complexity or uniqueness, often stored in places like Excel docs saved on endpoints — and often shared via unsecured methods like email.
- Passwords stored in — and retrieved from — the consumer-grade tools I mentioned earlier, which might allow a simple UX, but typically cannot:
– Provide control and visibility into who has access to what apps.
– Offer detailed logging and reporting functionality, which limits auditing capabilities.
– Prevent employees from saving passwords in their browsers, a key entryway for attackers targeting endpoints.
Now, let’s ask questions whose answers you may not know yet – but will ultimately give you data that informs strategic decisions.
- In your organization, which apps live outside of SSO and how many are there? What kinds of data do these apps contain? Which apps are approved by IT and which bypassed your policies?
- Who in your workforce is using these apps: small, concentrated segments of employees, entire business units or the full organization?
- For each of these high-risk apps, what controls and tools — if any — do you have in place for not merely managing them, but protecting them?
With a data-informed assessment of your enterprise’s password vulnerabilities, you can decide on which controls to put in place to mitigate risks to your organization.
Action Steps: Four Ways to Protect Passwords Like They’re Privileged Credentials
Here are four ways you can apply security-first controls to employee passwords while balancing the need for protection and productivity.
1. Security-first Password Storage and Retrieval
IT and security teams can mitigate the risks of highly vulnerable passwords by implementing secure, centralized storage for workforce credentials. Key functions to look for:
- The ability to centrally control how accounts and credentials are stored, managed and retrieved
- The peace of mind of securing passwords with end-to-end encryption in transit or at rest
- The flexibility to host passwords in a secure cloud location or self-hosted vault, depending on your organization’s needs
Organizations can protect employee credentials by enabling automated, real-time password retrieval from their chosen cloud or vault location. Inspired by just-in-time controls typically used for the IT admins of the world, this capability can help CIOs, CISOs and their teams ensure passwords are never stored locally at endpoints — thus reducing the attack surface.
2. Safe Password Sharing and Account Management
Considering the threats we’ve discussed, you’re likely seeking greater control over how employees share passwords. By applying a least privilege approach, enterprises can ensure that employees — for example, line-of-business team managers — can securely share credentials without revealing password characters. Here are key controls to adopt:
- Protect privacy by controlling who can share, view and edit credentials.
- Impose precise time limits on how long a user can access a shared app.
- Manage the transfer of credential ownership to new users.
- Prevent users from saving passwords in built-in browser password managers, reducing the number of accounts and credential repositories.
In an era of increased workforce turnover, this level of control is essential. For example, with automated tools, you could transfer ownership of an app’s account without losing the chain of custody when the primary owner leaves your organization.
3. Frictionless — and Secure — User Experience
Eighty-six percent of security leaders believe that optimizing the user experience is important-to-very important for enabling Zero Trust success through Identity and Access Management tools. Building upon that perspective, enterprises can benefit from the password protection capabilities that can:
- Integrate with corporate directories and third-party identity providers.
- Know when users are entering credentials into web apps’ login forms and offer to save them in a secure vault — and securely auto-fill credential fields in future instances.
- Automatically generate strong, complex and unique passwords for users whenever needed.
4. End-to-end Visibility for Audits and Reporting
An enterprise-grade approach to password protection should provide real-time visibility into users’ access activity. For example, security admins need the ability to determine which employees have accessed a specific application during a particular time — with intuitive reporting for audits.
But what happens to visibility after a user logs in? Security controls must continue past the point of authentication. Enterprises should look for ways to require an extra layer of protection that allows them to monitor and record all actions taking place once a user is logged in.
In light of today’s compliance demands, it’s important to ensure any records surrounding high-risk actions taken in apps are backed up by a full audit trail.
Putting it All Together: Identity Security
Eighty-two percent of security decision-makers have an assume-breach mindset. If you’re among them, you know: no organization is immune to a breach or attack. So as part of your strategic planning, it’s essential to have operations in place to deal with threats as they materialize.
By using the four best practices in this piece, you can meet the urgent need of securing employee credentials and enforcing an enterprise-wide password policy. And while passwords are a reality for organizations today, you can build toward a passwordless future, as our industry continues to innovate.
In the meantime, it’s important to keep the long game in mind.
Securing the enterprise is an ongoing mission. As you bolster your password protection capabilities, you can build toward a holistic Identity Security approach that brings together a range of controls and solutions. Considering what we’ve learned from recent breaches, here are a few examples of how an Identity Security mindset can help you:
If you have enterprise-grade password protection, you can complement it with adaptive multifactor authentication (MFA) that can increase the difficulty of challenges when it identifies signs of risk.
- If you believe parts of your workforce — for example, employees with access to cloud controls — should pass MFA no matter what (keeping in mind MFA fatigue), you can require phishing-proof MFA factors such as number-matching authentication.
- If you’re concerned about attackers stealing credentials at the endpoint, you can establish controls to ensure users can only access critical environments from trusted machines.
- If you’re working on putting the right solutions in place, remember: having the right people in place is also key. From CIOs and CISOs to admins and DevOps teams, everyone has a role to play.
Together, these are key examples of Identity Security in action. We at CyberArk advocate this approach to our customers and partners and we use it ourselves. I believe this is the way to protect passwords, enable Zero Trust and hopefully… reduce the number of concerns keeping you up at night.
You can learn more about our solution for applying enterprise-grade protection to your employees’ passwords: CyberArk Workforce Password Management.
Omer Grossman is the global chief information officer at CyberArk. You can check out more content from Grossman on CyberArk's Security Matters | CIO Connections page.






















