
Following our post “A Brief History of Game Cheating,” it’s safe to say that cheats, no matter how lucrative or premium they might look, always carry a degree of danger. Today’s story revolves around the developer of the popular EvolvedAim, a cheat for Escape From Tarkov. He sold his tool with an information stealer bundled with it, double-dipping and causing damage to his clients and to the game itself.
Escape From Tarkov is a hardcore and realistic military simulator that has gained popularity over the years. With an estimated 14.7 million players, the underground cheats market thrived. One of those cheats is EvolvedAim, a tool that promises a large set of features like automated trading in the game’s built-in auction house and automatic training of specific skills through repetitive actions. The developer has operated like a small software company, even developing a tiered recurring revenue strategy and running ad campaigns on various cheat-related forms.
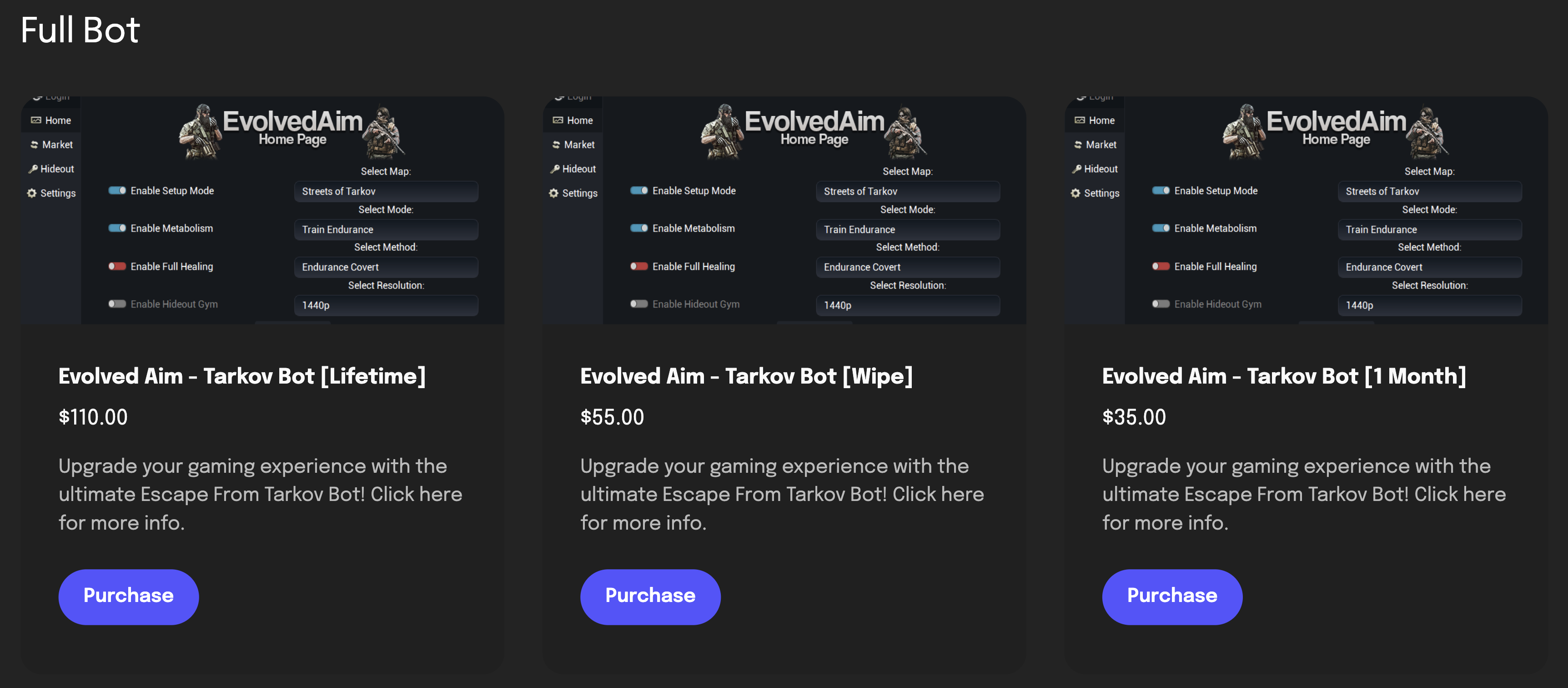
Figure 1: EvolvedAim pricing
Malware in cheats is not uncommon, but the potential impact is significant in this case. Not only is Escape From Tarkov a game popular among young adults aged 25 and older, but this particular cheat costs real money in a subscription payment structure, as seen above. This implies that the majority of users affected are adults. The information stolen from these users could potentially be used to pivot and gain access to personal information and even to companies worldwide, as more detailed below.
As we understand it, the story begins with EDP, the owner of one of the largest forums for Tarkov cheats and bots, including a large marketplace booming with activity with over 30k visits a month. About a year ago, EDP was contacted by the leading developer of EvolvedAim (the cheat with malware potentially embedded in it) – Mythical, with the intent to sell his tool on EDP’s forum and, in turn, give him a cut of the profits.
This deal held for almost a year, bringing both parties a nice revenue stream. It also helped EvolvedAim gain traction outside the EDP forum, as they have expanded to selling their tool on their website (as seen in Figure 1) and ran ads in various forums. The issue started with a conflict between them as Mythical wanted to lower the cut that EDP takes from his profits and continue to sell on his forum. Around the same time, EDP noticed several suspicious logging attempts on his accounts and screenshots of his desktop being leaked on various occasions.
This is where we step in. We’ve seen this situation unfold and discussed on various forums related to cheats and malware, and it piqued our interest. As such, we have decided to check if there’s any merit to the stated claims. In the following sections, we will review our technical findings and dig deeper to understand what is bundled inside the EvolvedAim cheat.
EvolvedAim Technical Analysis
EvolvedAim is written in Python 3.10 and is converted into an executable using the very popular library PyInstaller, which makes the analysis process of executables of this type very straightforward. First, we use pyinstxtractor (or PyInstaller Extractor) to recover the .pyc files that are embedded in the executable and give us the potential entry points for the project, as displayed in Figure 2:
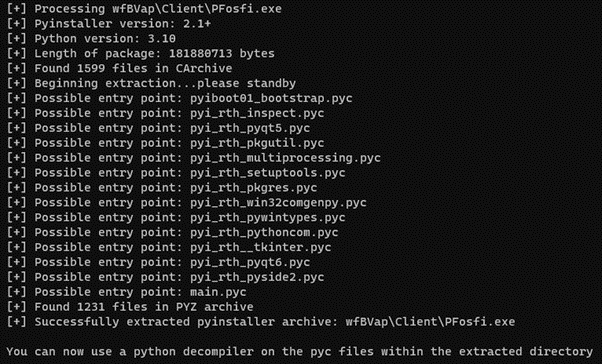
Figure 2: pyinstxtractor output
The .pyc files contain Python bytecode that is not human readable as they are meant for Python’s interpreter. Decompiling them back to human-readable form can be done through pycdc, with a small caveat – Python versions above 3.8 are not fully supported by any decompiler as of this moment, and errors like those in Figure 3 will occur from time to time, causing partial decompilation of files.
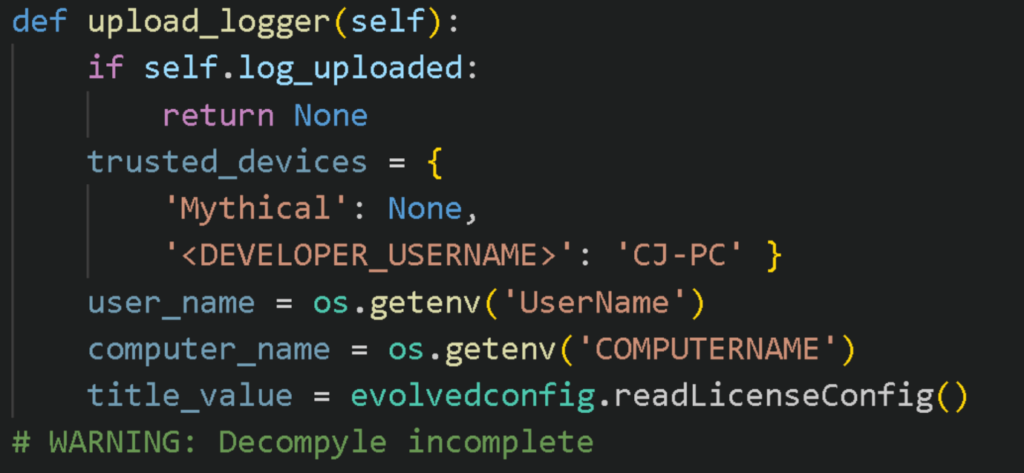
Figure 3: Partially decompiled file
Luckily, pycdc has another tool to help in this situation – pycdas. This tool is used to convert the Python bytecode from a non-human readable format into one we can actually understand.
Although it is very convoluted and complex to analyze, as seen in Figure 4 below, it is more than enough to give us a glimpse of the missing logic from Figure 3.
Figure 4: Python bytecode
Runtime Flow
Figure 5: EvolvedAim license key input
When we run EvolvedAim, we are greeted by an input box, as seen in Figure 5, asking for a license key. However, by the time the user enters the key, their information has already been stolen and exfiltrated, as the malicious code runs in a separate thread that starts at the initial execution of the cheat.
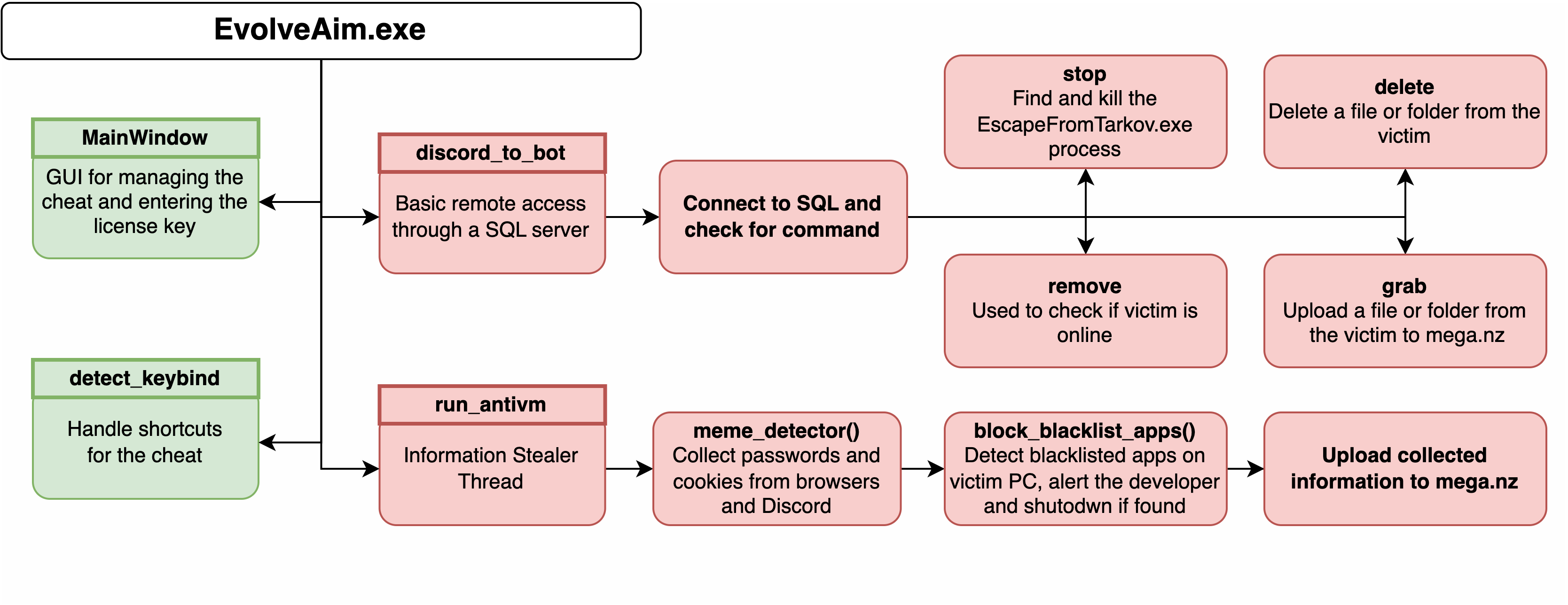
Figure 6: EvolvedAim Logic
As seen in the simplified logic flow in Figure 6, EvolvedAim runs four threads. The two on the left are benign (MainWindow and detect_keybind) and are used for the cheat functionality. The remaining two are malicious, cleverly hidden, with non-suspicious names like discord_to_bot and run_antivm. This trend extends further into other parts of the logic, as the function that steals all the information is called meme_detector.
String Deobfuscation
Some of EvolvedAim’s more intriguing strings are stored in an encrypted format, decrypted at runtime using the overlay.decrypt_bot_string function. This function employs the AES encryption algorithm and uses a hardcoded key in combination with the IV value embedded at the start of the encrypted string, allowing us to decrypt all the values even before running the malware.
autu_enc = overlay.decrypt_bot_string('353239313430353738393039313134308f13e0577c6a4a9dbc2f39a0bda73d5f')
After string decryption, we can find various credentials and URLs used by the attacker, including login info for a file share service, SQL server credentials and several Discord webhooks, all of which are being used for malicious purposes.
autu_enc = 'EvolvedTarkovBot' auto_enc = 'tdmigO6jXK' auts_enc = '5141f47bbf3fbc01f5270224bf51229ab214957ad30t31a118620889a09c072x' wh1_enc = 'https://discord.com/api/webhooks/<REDACTED>/3x7y9Mm2DhtSh2W4Cz1iTkXor9a85Q_cYf5n0H8CK-Tz-HmNCudH4_AmK5e8P2y-QS5J' wh2_enc = 'https://discord.com/api/webhooks/<REDACTED>/sQLOKdK4N8q13PrW6w-LVbROhlPbSoKXuUoBlQ3UPZxOw5RWsecicPtuiJHiO5G254fo' meu_enc = '<EVOLVE AIM EMAIL>@gmail.com' mep_enc = '<MEGA PASSWORD>' edbu_enc = 'admin' edbp_enc = '<SQL DB PASSWORD>' edbh_enc = 'evolve-data.<REDACTED>.us-east-2.rds.amazonaws.com' edb_enc = 'evolve_db'
Data Collection and Exfiltration
As seen in the program flow in Figure 6, four threads run simultaneously; one appears as an innocent anti-virtual machine detection but, in fact, houses the malicious logic “hidden” within EvolvedAim.
The antivm thread initially checks the PC name, and if it matches one of the two blacklisted names, it will not proceed with the information stealer. Interestingly, it seems they intended to run the cheat on their machines, as the two blacklisted names we found belong to the developers of EvolvedAim:
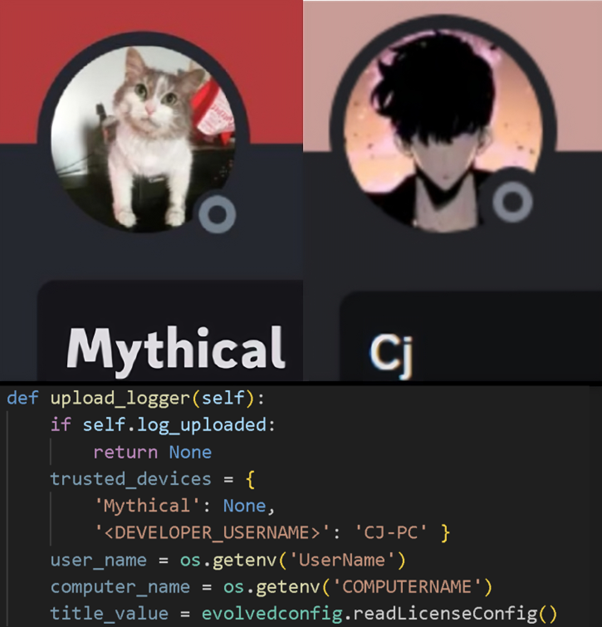
Figure 7: Developers want to cheat too!
Next, the information-stealing logic is executed, collecting passwords and cookie values from the following browsers:
| Chrome | Firefox | Kometa | 7Star |
| Opera | Amigo | Opera GX | Sputnik |
| Tor | Torch | CentBrowser | Vivaldi |
| Chrome SxS | Epic Privacy Browser | Uran | Yandex |
| Iridium |
Additionally, all the files stored by the popular crypto wallet extension MetaMask are collected and uploaded, and the same goes for sensitive files in Discord, a popular chatting platform and Steam, the most popular online game store in the world. On top of that, a file list from the Documents and Downloads folder is collected, and last but not least, a screenshot from the victim’s PC is taken, giving the attacker a preview of the victim’s PC.
All of the collected information is temporarily stored in a folder and then compressed to a zip archive with the victim’s PC name. That same zip is then uploaded to Mega.nz, a file hosting service used by the attacker to store and manage the collected data.
After collecting the information and uploading it to Mega.nz, the malware uses a Discord webhook to notify the attacker on Discord.
Command and Control
In addition to the information-stealing capabilities we’ve already discussed, EvolvedAim runs a thread called discord_to_bot. This thread implements a rudimentary remote logic using a MySQL database as a communications channel. The thread runs in an infinite loop, periodically checking for commands, and this allows the attacker to send one of four commands:
1. Stop – kill the process “EscapeFromTarkov.exe,” which is the game’s main executable.
2. Delete – delete a file or folder from the victim’s PC.
3. Grab – collect an arbitrary file or folder from the victim and upload it to Mega.nz.
4. Remove – delete the command from the database used to check if the client is still active.
While active, the SQL database would look something like this:
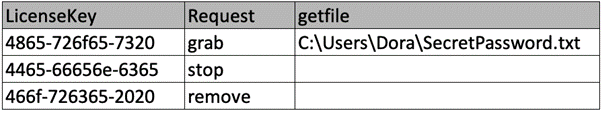
Figure 8: SQL database example
Impact and Consequences
Following this discovery, EDP and various other forum owners publicly warned their users about EvolvedAim and banned Mythical from their servers. With a speculated clientele of over one thousand users and the targeted population group being young adults, the damage and amount of information stolen are significant.
EvolvedAim is no longer operational. Its Discord server has been closed, and it seems like it’s been forced to close shop, hopefully for good.
Cheating is frowned upon in all aspects of life and always has a downside. In this case, the downside is paying hard-earned money to gain access to the cheat and also paying with personal information, passwords and files.
This impact is not confined to the victim, as people may log into work-related accounts on their personal computers, thus opening their workplace to potential danger.
Malware in cheats and cracked software is not uncommon, but this is the first case we’ve stumbled upon where a paywalled cheat developer is double dipping on the profits by attacking his own clients.
IOC
| EvolvedAim Executable | 9794729e54bb19f5dca7f43c8402a7e9dcc375d57f8c2d6bd26ba05122665d97 |
| EvolvedAim Executable | 0d5913fce37577426cff7abe31db60d518058fc90315d15b624415839cb5e1c7 |
| EvolvedAim Executable | 715f1772f4fb5b9a4f576bf3c099779733967ea90c329b2f470581c7f99f0e24 |
| EvolvedAim Executable | 9794729e54bb19f5dca7f43c8402a7e9dcc375d57f8c2d6bd26ba05122665d97 |
Disclaimer
Some information in this post has been altered to protect the privacy of the involved parties. Additionally, we have deliberately not covered the cheating aspect of EvolvedAim and its implementation as we do not support this kind of action, especially when it is strictly forbidden based on Escape From Tarkov’s policy.
David El is a malware researcher at CyberArk Labs.




















