
An infostealer is a type of malware that is focused on gathering sensitive and conditional information from the compromised system. While this information is often related to the user’s credentials, they have also been known to search out financial and personal information.
While infostealers often target high value information, they generally aren’t sophisticated and are usually sold on hacking forums for anywhere from a few dollars to a couple of hundred dollars. Most infostealers in the wild use the same techniques for stealing data, however, the difference in price could be due either to the length of the subscription and/or the robustness of their features – including targeted software, sophistication and other extra features.
Most of the infostealers are sold as Malware-As-A-Service (MaaS) – which allows malware authors to provide a fully working package to their “customers” (a.k.a cybercriminals) and also includes access to a technical support team and updates for the malware (bug fixes and new features). The package typically includes a login to an administrative panel where the attacker can customize the malware functionality, view all the stolen credentials/logs and download builds of the malware. This model allows cybercriminals to get easy access to the stealer and operate in a maintenance-free environment.
Let’s explore the operation methods of a typical infostealer malware named ‘Raccoon.’
Raccoon stealer – first seen in the wild in April 2019 — is a popular infostealer nowadays because of its low price (USD$75 per week and $200 per month) and its rich features. Also known as “Racealer,” Racoon is used to steal sensitive and confidential information including login credentials, credit card information, cryptocurrency wallets and browser information (cookies, history, autofill) from almost 60 applications.
Raccoon stealer is written in C++ and, while it lacks sophistication, it has a wide range of methods and features for stealing data from popular browsers, email clients and cryptocurrency wallets.
Raccoon is mostly delivered using one of two methods:
- Exploit Kits – Malicious website that profiles the victim for any vulnerable browser-based applications and redirects the user to a landing page according to the vulnerability. The landing page contains the specific exploit code that takes advantage of this vulnerability and uses it to install the malware.
- Phishing Campaigns– A type of social engineering, the user is convinced by the seemingly innocent content to execute the malicious payload. Usually, the victim receives an email with a Microsoft Office document attachment, which contains a malicious macro. By default macros are disabled, so the attacker will try to convince the user to enable macros and then the malicious code will be executed.
Initialization
Most malware and particularly MaaS have a C&C server so that it can get information regarding the malware options/features enabled by the attacker and send back all the stolen data from the user.
The malware C&C server is required for malware functionality, therefore, in order to stay stealthy, the malware authors store the C&C server’s address in some way to remain undetectable.
Raccoon Hidden C&C
The stealer binary 3 contains hardcoded values:
- A base64 string Mypo7lAqDGp6xNdb/CUHGKD0x9cCPC4XYTUYxcMwDD/tWbPQlmUzGwH+R8cN9kncB7OZsuFsvcdiB1xtd7BAC0yoPZteuoB1hV5KWIQ0+cA=.
- A first encrypted key for the Google Drive URL decryption routine.
- A second key 26b948359b43d02743bd1fad775a15ca for the C&C server URL decryption routine.
The process of getting the server address is as follows:
- Raccoon decrypts the first key, which will be the Google Drive decryption key 1@zFg08*@45.Part of Raccoon’s strings are encrypted, like the first key. Raccoon creates a byte array where the most significant byte is the XOR key and the rest of the array is XORed and NOTed with the byte-key,
for example 34FA8BB18DACFBF3E18BFFFE→ 1@zFg08*@45.
- The stealer uses a decryption routine (some naive XOR cipher) in order to decrypt the first hardcoded base64; the decryption function gets the first key and the decoded base64.
The decryption function will return a string for Google Drive URL (https://drive[.]google[.]com/uc?export=download&id=1QQXAXArU8BU4kJZ6IBsSCCyLtmLftiOV) that will be the middle stage for getting the C&C domain.
- It will then create a GET request to this Google Drive using HTTPS.
The response from google drive is shown in Figure 2.
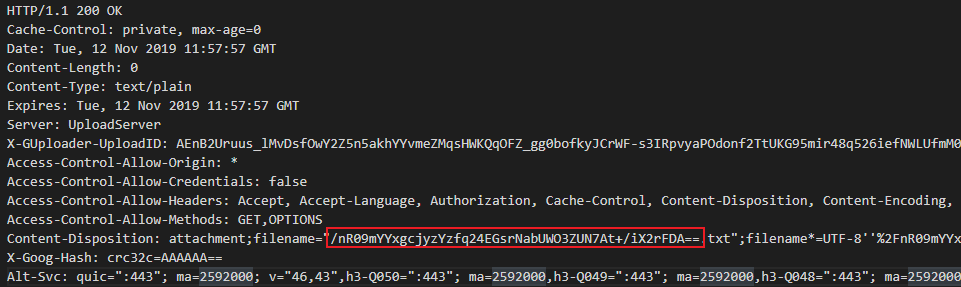
- Raccoon filters the response in order to get the file name from the Content-Disposition response header.
“attachment (indicating it should be downloaded; most browsers presenting a ‘Save as’ dialog, prefilled with the value of the filename parameters if present), MDN.”
The filter function gets the response as a string and two others strings (attachment;filename=” , .txt”;filename*=UTF-8 ) and returns the string between those two strings → /nR09mYYxgcjyzYzfq24EGsrNabUWO3ZUN7At+/iX2rFDA== which is the encrypted C&C server URL.
- Finally, Raccoon decrypts the filtered base64 string by using its naive decryption routine and passing the decoded base64 from the response and the second hardcoded private key. The decryption routine will return Raccoon’s C&C http://35[.]189[.]105[.]242/gate/log.php.
Stealer’s Config
Like most of the credential stealers, the client (i.e. the attacker) can customize his or her own configuration for the stealer functionality, which can be saved in the binary built by the malware or in the C&C server, and sent back to the malware when executing.
In Raccoon, after the client chooses the configuration, the malware builder generates a configuration ID for the client’s configuration and writes this ID to the compiled malware.
In this case, the config ID is encrypted, Raccoon has another hardcoded base-64 encoded string in the binary. To decrypt the config ID, it uses the first key (1@zFg08*@45) and, after the decryption routine, gets the config ID (which is, in this case, 4ede41fe0ea963034a3d65f0dd442de4671c214f).
To get the full configuration, the stealer has to query the C&C.
- The malware generates an ID for the machine from MachineGuid, which is a quite common ID (query this registry keyHKLM\SOFTWARE\Microsoft\Cryptography for the value MachineGuid) and from the current username (calling to GetUserNameA).
- It creates the next machine profile bot_id=%machineGUID%_%username%&config_id=%configID%&data=null and encoded the string as base64.
- What’s left is to send the machine profile to the C&C. It connects the encoded base64 string to params= and sends a POST request with params=%base64MachineProfile% as the content of the request.

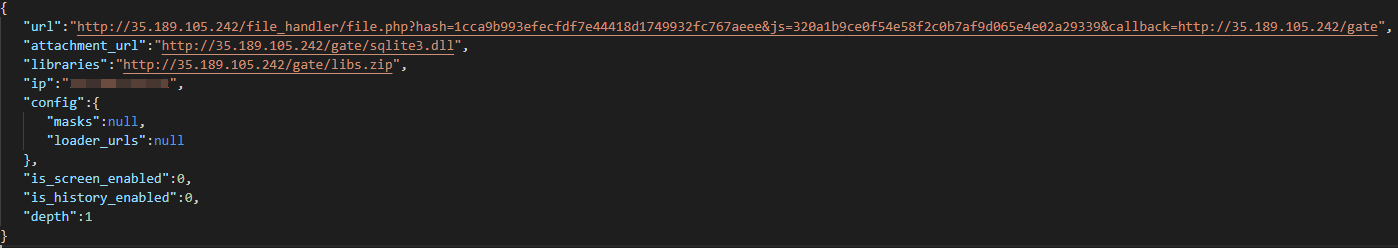
The C&C server returns JSON that contains the configuration the stealer needs for its functionality.
Capabilities
Raccoon targets a wide range of applications and uses known techniques in order to extract sensitive data from those applications.
Raccoon uses the same procedure for each of the targeted applications:
- Get the application file that contains the sensitive data.
- Copy the file to its working folder (%Temp%).
- Perform the specific routines for the application in order to extract and decrypt the related data.
- Write a text file to its working folder with the stolen information.
In order to extract and decrypt the credentials from the applications, Raccoon downloads the specific DLLs for the applications. The config JSON contains a URL from where the malware will download those libraries.
Raccoon targets 29 chromium-based browsers including Google Chrome, Opera, etc. (full list below) that have the same folder structure and share a similar codebase, which leads to a similar way of handling sensitive data. The sensitive data in those browsers is saved in the same format and the “User Data” application folder contains the SQLite databases. Most of the stealers, like Raccoon, perform SQL queries using sqlite3.dll in order to get the user autologin passwords, credit card information, cookies and browser history.
The stealer also relies on the same methodology for Mozilla based applications. Because these applications have the same method and folder structure, the stealing techniques for the applications are the same. The only difference is the names. The stealer targets four Mozilla-based browsers including Firefox and SeaMonkey, (full list below) and one Mozilla-based email client, ThunderBird. For those applications, the stealer extracts and decrypts sensitive data like username and password, cookies and history. It is important to mention that Raccoon also supports an older version of Mozilla based applications – it supports Firefox versions <32, for example. In order to do so, Raccoon downloads a zip file containing a lot of DLLs for decrypting protected data. By using functions from nss3.dll, the malware is able to decrypt and extract the data from the SQLite databases and the JSON login file.
When looking for cryptocurrency wallets, Racoon targets popular applications like Exodus, Jaxx and more. Like most stealers, Raccoon is looking for those wallet files in the default application locations, but it also has a wallet scanning feature that allows it to grab any wallet.dat file.
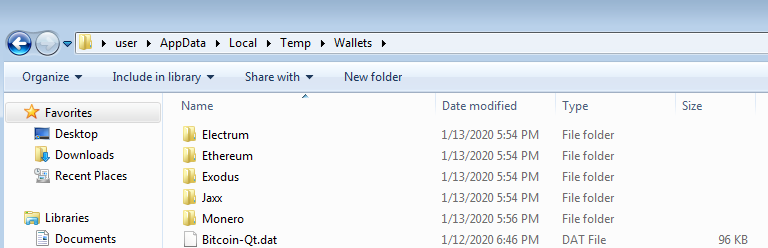
The malware gathers information about the machine like the OS arch and version, system language, hardware information and installed applications. In addition, it can take screenshots from the user’s machine if that was enabled by the attacker’s configuration.
After fulfilling all its stealing capabilities, Raccoon gathers all the files that it wrote to the temp folder into one zip file named Log.zip. Now all it has to do is send the zip file back to the C&C server and delete all traces of itself.
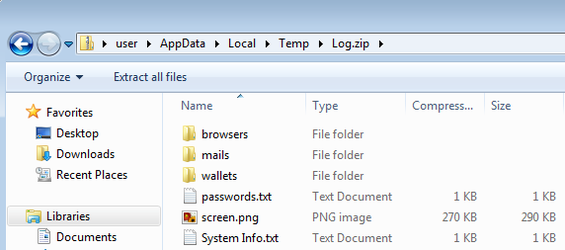
Raccoon doesn’t use sophisticated methods to send the file back to the C&C. It simply gets the URL of the C&C handler (from the config JSON) and the path for the Log.zip file and sends the Log.zip as is, without any encryption, using an HTTP POST request.
Raccoon also has the functionality to be used as a dropper, a feature that specializes in loading a second-stage malware payload onto a victim’s system. It downloads malicious files and runs them. This is mostly used to run other malware. In this case, the dropper feature is disabled by the config JSON, but when it is enabled, Raccoon takes the URLs from the loader_urls key, downloads the file to the temp folder and executes it by calling to ShellExecuteA with the file path.
Raccoon Stays On Track
Similar to other “as-a-service” offerings, Raccoon is still being developed and supported by a group. Since we started the analysis of this sample, the Raccoon team members have improved the stealer and released new versions for the build, including the apability to steal FTP server credentials from FileZilla application and login credentials from a Chinese UC Browser. In addition, the attacker panel has been improved, some UI issues were fixed and the authors added an option to encrypt the builds right from the panel and downloaded it as a DLL.
Potential Damage & Mitigation
This kind of information stealer can cause a lot of damage to individuals and organizations. The attackers are looking for privileged credentials in order to achieve privilege escalation and lateral movement. What used to be reserved for more sophisticated attackers is now possible even for novice players who can buy stealers like Raccoon and use them to get their hands on an organization’s sensitive data. And this goes beyond usernames and passwords to information that can get them immediate financial gain like credit card information and cryptocurrency wallets.
Even though Raccoon is not the most sophisticated tool available, it is still very popular among cybercriminals and will likely continue to be. To defend against credential stealing malware, organizations can use a solution like CyberArk Endpoint Privilege Manager, combined with basic common sense tactics like updating systems and applications, avoiding opening suspicious attachments or clicking on unknown URLs. Proactively protecting vulnerable endpoints is critical to improving an organization’s overall security posture.
If you’re interested in a comprehensive technical analysis of this malware’s techniques and capabilities, download our free whitepaper, “Analyzing the Raccoon Stealer.”
Appendix
Targeted Applications
Browsers
Google Chrome, Google Chrome (Chrome SxS), Chromium, Xpom, Comodo Dragon, Amigo, Orbitum, Bromium, Nichrome, RockMelt, 360Browser, Vivaldi, Opera, Sputnik, Kometa, Uran, QIP Surf, Epic Privacy, CocCoc, CentBrowser, 7Star, Elements, TorBro, Suhba, Safer Browser, Mustang, Superbird, Chedot, Torch
Internet Explorer, Microsoft Edge
Firefox, WaterFox, SeaMonkey, PaleMoon
Email Clients
ThunderBird, Outlook, Foxmail
Cryptocurrency Wallets
Electrum, Ethereum, Exodus, Jaxx, Monero, Bither
YARA Rule
CODE
rule raccoon_stealer_rule{ meta: author = "Ben Cohen, CyberArk" date = "16-01-2020" strings: $stealer_typo = "g:\stealer\stealler\json.hpp" wide $path1 = "\Google\Chrome SxS\User Data" wide $path2 = "\Chromium\User Data" wide $path3 = "\Xpom\User Data" wide $path4 = "\Comodo\Dragon\User Data" wide $path5 = "\Amigo\User Data" wide $path6 = "\Orbitum\User Data" wide $path7 = "\Bromium\User Data" wide $path8 = "\Nichrome\User Data" wide $path9 = "\RockMelt\User Data" wide $path10 = "\360Browser\Browser\User Data" wide $db1 = "Login Data" wide $db2 = "Cookies" wide $db3 = "Web Data" wide condition: $stealer_typo or (4 of $path* and 2 of $db*)}
IoCs
- SHA256
- a57e1f3217b993476c594570095d28b6c287731a005325e5f64a332a86cb7878
- Malicious Activity
- Mutex – rc/%username%
- exe /C ping 1.1.1.1 -n 1 -w 3000 > Nul & Del /f /q %malware_path%
- Network Communication
- https://drive[.]google[.]com/uc?export=download&id=1QQXAXArU8BU4kJZ6IBsSCCyLtmLftiOV
- http://35[.]189[.]105[.]242/gate























