
These days, when the world is focused on getting a handle on the COVID-19 crisis, cybercriminals are taking advantage of our desire for information. We’re seeing all kinds of attacks leveraging the Coronavirus or COVID-19 name.
Today, we are going to focus on one specific piece of malware named “CoronaVirus.” This malware is a new type of ransomware that spreads through a phishing website, WiseCleaner[.]best. The website is supposed to resemble WiseCleaner.com, which provides free system utilities for Windows to improve the computer’s performance.
The ransomware is distributed alongside an infostealer named KPot, also known as Khalesi, a which is an infostealer popular in the underground community.
In this blog, we’ll provide more details on the delivery and execution of this new ransomware as well as discuss some of the prevention methods we tested against it.
Delivery
As mentioned, this malware is delivered through a user visiting a fake website and downloading the malicious file – “WSHSetup.exe.”
WSHSetup.exe is a Downloader, which is the first stage of infection. It is usually small and pre-programmed to download and start other malicious files.
The malicious file from the fake website downloads the KPot stealer – an information stealer that focuses on exfiltrating account information from web browsers, instant messengers, email, VPN, RDP, FTP, cryptocurrency and gaming software – and the CoronaVirus ransomware.
After it executes the KPot stealer, it downloads and executes the CoronaVirus ransom. The Downloader trying to download the malware from trynda[.]xyz; file1.exe is the KPot stealer; file2.exe is CoronaVirus ransomware and the other files numbers returned 404 (Figure 1).
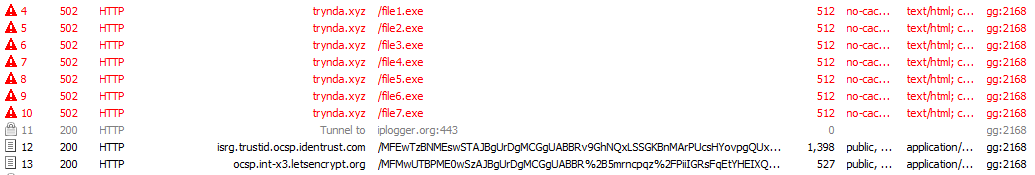
At the time that this research was accomplished, the malicious website was not active.

Ransomware Execution
CoronaVirus Ransomware encrypts the victim’s data and demands a very low-price ransom (0.008BTC, approximately $45), which is atypical for ransomware.
- The ransomware encrypts the files, deletes shadow copy backups and changes their names to [email protected]___%file_name%.%ext%.
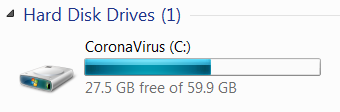
- It renames the drive CoronaVirus.
- It then modifies the BootExcute key on HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager in order to display a ransom note on reboot (before windows loaded). The ransom note will display for 15 minutes.
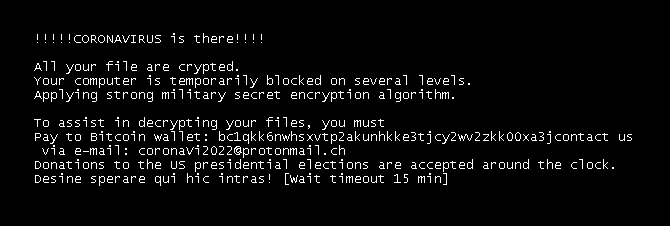
- In every directory where it encrypts a file, CoronaVirus ransomware creates a text file named txt that contains the ransom note with the attacker details.
After encrypting all the files, CoronaVirus deletes itself and reboots the machine. To deploy some of the ransomware functionality, like changing the BootExcute registry key and renaming the drive name, it must have elevated privileges; therefore, it has to run as an Administrator.

Prevention
Using the tools at our disposal, we tested the CoronaVirus ransomware against our Endpoint Privilege Manger. The good news is that it was 100% effective during our tests at preventing this malware from encrypting files. We also found that Endpoint Privilege Manager’s advanced credential theft protection capabilities can detect and block threats like the KPot infostealer and protect the user’s credentials. This proactive approach is not dependent on the ability to detect a new type of malware; instead, EPM treats all unknown applications as potentially suspicious and protects information accordingly.
It’s also important to note that these attacks are based on social engineering, so basic prevention technique also apply here. Avoid clicking on unknown URLs or opening suspicious attachments. Make sure there are backups and the systems have the latest security updates.
IoCs
SHA256
- Downloader – 5987a6e42c3412086b7c9067dc25f1aaa659b2b123581899e9df92cb7907a3ed
- KPot Stealer – a08db3b44c713a96fe07e0bfc440ca9cf2e3d152a5d13a70d6102c15004c4240
- CoronaVirus Ransomware – 3299f07bc0711b3587fe8a1c6bf3ee6bcbc14cb775f64b28a61d72ebcb8968d3
- CoronaVirus’s BootExcute driver -e742ff574b7fba5dff1788237822aabb803e53f043a0940548aec4f1d6d2d673
Network Communication
- WiseCleaner[.]best
- trynda[.]xyz























