
In recent years, cybersecurity has become a board-level issue resulting in several executives taking greater responsibility in cybersecurity-related decisions. As a result, the CISO is no longer a technical subject matter expert but an executive risk manager who shares a responsibility matrix with the board of directors, CEOs and other executives to make informed risk decisions. At the highest levels, these executives care about the organization’s revenue, mission, risk and costs, leading to strategic questions about assurance, compliance and security practices.
Recent years have highlighted the need for a robust Identity Security strategy to secure the business from modern-day threats and attacks. CyberArk’s upcoming Identity Security State of the Market survey indicates that in 2023, 81% of 1,500 respondents will exponentially increase their spending on Identity Security as part of their cybersecurity budget. This increased investment drives varied perceptions across C-Level executives and all other personnel, including other senior decision makers (VPs/directors/managers) and security practitioners.
Our research finds that C-level executives have an abnormally high degree of confidence in mitigating Identity Security-related risk as opposed to other personnel who are technically astute and aware of the complexities of their IT environments. For example, 69% of the C-level executives believe they are making the correct Identity Security decisions. On the contrary, only 52% of all roles believe the same to be true. This higher confidence of C-level executives was also reflected in their perception of the impact of cybersecurity investment. The chart below highlights this concerning trend across multiple facets of Identity Security.
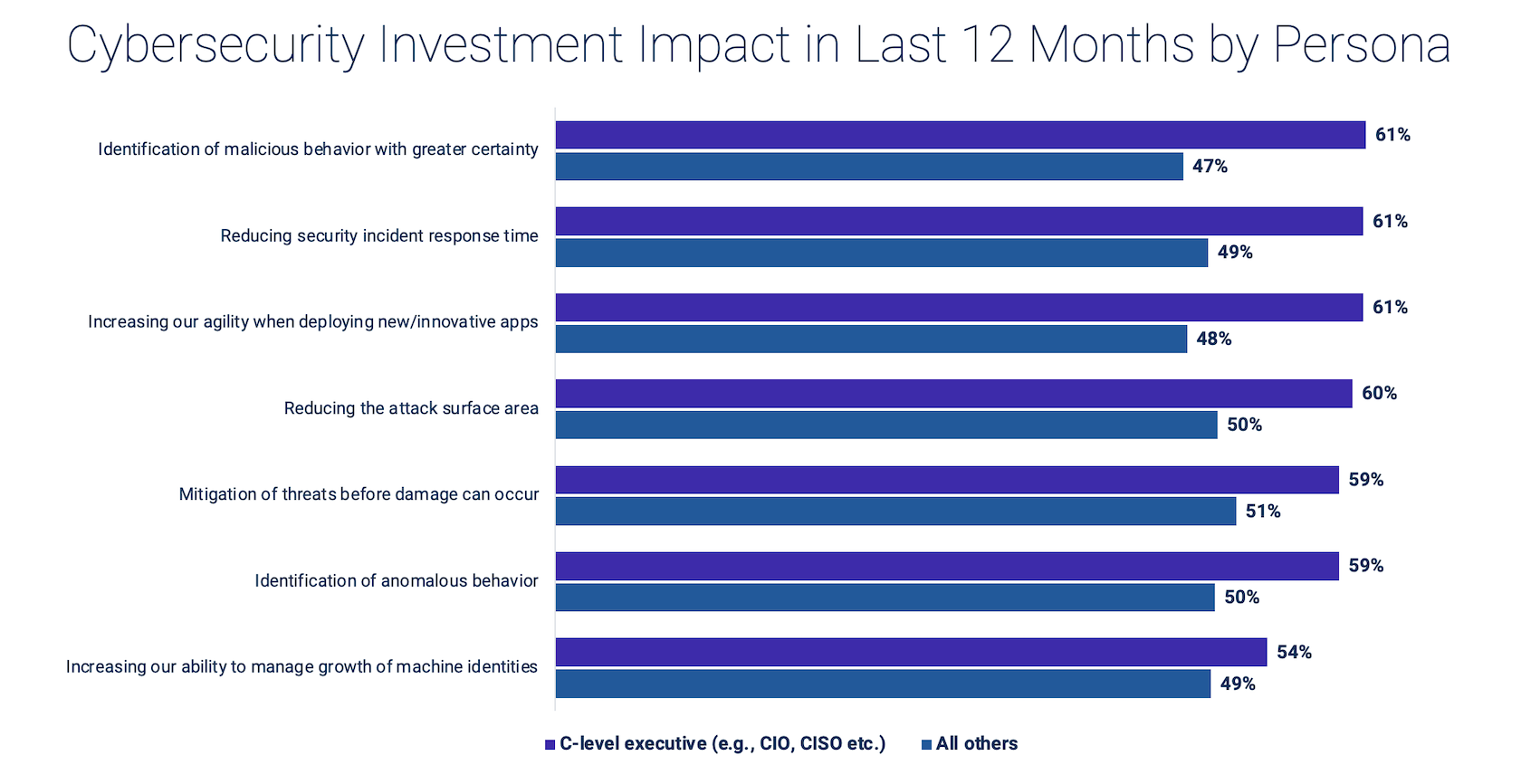
The survey’s findings reveal a sharp disconnect between the confidence of the C-level executives in their organization’s Identity Security strategy and the actual damage that identity-related cyber incidents can inflict.
Identity Security Confidence Is Not Synonymous With Reality
What’s the proof of this executive overconfidence? Our research indicates that in 2022, 58% of respondents believed they made the right Identity Security decisions. However, this confidence did not necessarily reflect positive outcomes. 63% of the respondents indicated that they suffered at least one successful identity-related attack last year.
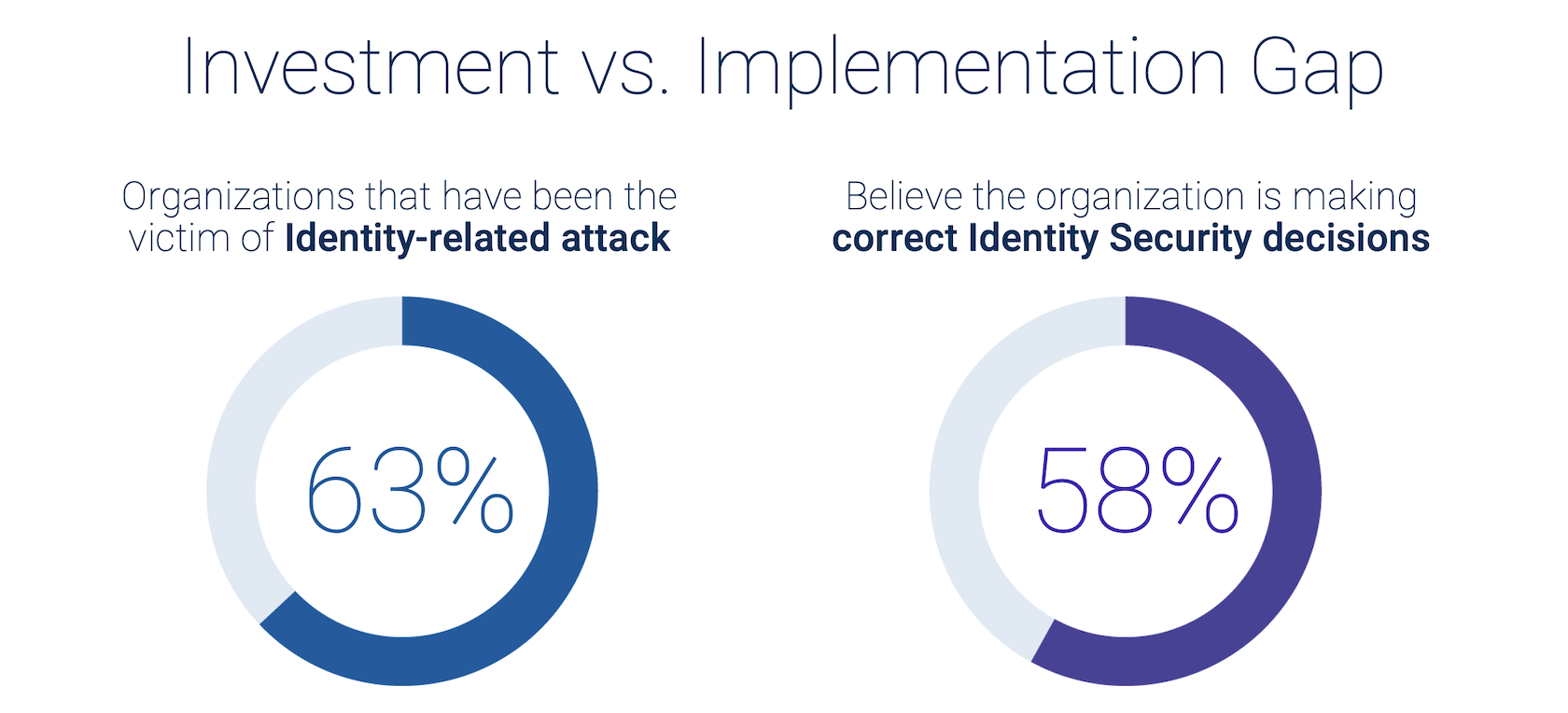
This C-level overconfidence could indicate a more significant problem: a lack of understanding of what a robust Identity Security strategy means beyond just investing in tools. Allocating line-item budgets to procure identity-related tools is the first step of a robust Identity Security strategy. Additional measures include integrating those tools, automation and continuous threat detection and response, based on specific business requirements of a given organization.
The Wide-ranging Impact of Identity-based Attacks
Of the 63% of respondents who were victims of an identity-related cyberattack in the last 12 months, 27% have experienced more than one. And the consequences of experiencing a cyberattack are multi-fold. After an attack, the most popular response among respondents was increased investment in cybersecurity technologies and services, which was determined after a thorough gap analysis and risk assessment. Cybersecurity quickly became a board-level discussion if it wasn’t already.
The short-term impact of a successful identity-related cyberattack includes delayed projects due to the significant manpower and time allocated to resolving the issue. On the other hand, products and services are impacted, causing problems like customer experience degradation and potentially lost revenues, compliance fines and extensive audits.

Our research also indicates that insufficient cybersecurity staff and inadequate in-house expertise when it comes to securing identities or mitigating identity-based risks are two major risk factors. The third risk factor – perhaps the most important – is that many organizations lack a specific line-item budget for Identity Security.
Identity Security’s Four Tenets
IDC FutureScape: Worldwide Future of Trust 2023 Predictions states that by 2025, 45% of CEOs, fatigued by security spending without predictable ROI, will demand security metrics and results measurement to assess and validate investments made in their security program. CyberArk believes that this prediction has the potential to materialize sooner, given the rate and sophistication of modern cyberattacks.
The proliferation of identities and endpoints, increased adoption of hybrid and multi-cloud environments and vulnerabilities from inadequately secured identities in the software supply chain are significant causes for concern. 85% of respondents expect to use three or more public cloud service providers in 2023 – and 57% of them have two independent teams responsible for securing identities in the public cloud and on-premises. The CyberArk 2022 Identity Security Threat Landscape Report indicates that respondents use over 70 security vendors on average. As a result, they prefer to procure platform-like “unified controls” from fewer vendors. But a strong Identity Security platform hinges on the four tenets of a robust Identity Security strategy.
In addition to investments in Identity Security tools, C-level executives must regularly seek updates on the state of integration, automation and continuous threat detection and response capabilities to ensure they are well-informed on their organization’s cybersecurity posture related to Identity Security. The following four tenets are foundational to ensuring that the investments adequately deliver on the promise of reduced cyber risk and increased resilience for your organization on an ongoing basis:
- Identity Security tools span management, privileged controls, governance, authentication and authorization for all human and machine identities.
- Integration of Identity Security tools across IT and security solutions is a must to secure access to all corporate assets and the entire IT estate.
- Automation ensures continuous compliance with policies, industry standards and regulations, enabling rapid responses to high-volume routine and anomalous events.
- Continuous threat detection and response provides organizations with a solid understanding of baseline identity behaviors to better react to anomalous activity.
Do you relate to any of the issues mentioned above? Are you beginning your journey to develop and implement robust Identity Security strategies? If so, it is important to consider comprehensive capabilities from Identity Security vendors that span identity management, access management and privileged access management (PAM) with leadership across these categories.
To read the complete results and analysis, stay tuned for the release of the CyberArk Identity Security State of the Market survey – coming soon.























