
After a decade in the making – or waiting, as the case may be – the National Institute of Standards and Technology (NIST) has released the first major revision to its Cybersecurity Framework (CSF), a set of voluntary standards and best practices for managing cybersecurity risks. NIST CSF 2.0, released on Feb 26, 2024, expands the scope and applicability of the framework to cover more types of organizations and industries, including the private sector, government and nonprofits. The new framework comprises six core functions: Govern, Identity, Protect, Detect, Respond and Recover. (I will detail these functions later on in this blog post.)
In this era of heightened digital vulnerability, the need for robust security measures has never been more pressing. NIST CSF 2.0 provides organizations with detailed guidance on managing their cybersecurity risks based on six main functions. The new framework includes a list of desired outcomes for organizations when building their cybersecurity strategy. It does not, however, detail how to achieve those outcomes in an identity security program – this is where you’ll want to take the advice of a trusted partner that can provide you with a best practices framework to follow.
This blog post will overview how identity security best practices related to people, processes and technology can help organizations adhere to NIST CSF 2.0 guidelines. The published guidelines are constructed on six interconnected functions, as shown in the figure below.
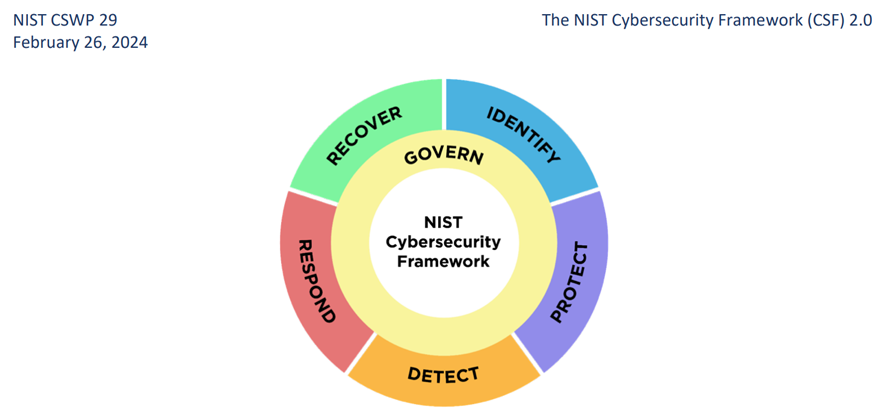
NIST CSF 2.0 functions (Source: https://www.nist.gov/)
Function 1: Govern – Understanding the Organizational Strategy and Policy
Focused on organizational strategy, the Govern function guides actions to achieve and prioritize outcomes in alignment with the organization’s mission and stakeholder expectations. NIST highlights understanding organizational context, establishing cybersecurity strategy and supply chain risk management, defining roles and responsibilities and enforcing policies.
Best practice identity security frameworks can help you achieve these goals. Organizations need clear and documented KPIs for their identity security programs. Such frameworks could offer risk-based prioritization guidance to help accelerate risk management decisions and determine key KPIs.
A comprehensive privileged access management (PAM) program should also include solutions for securing third-party access to reduce supply chain-related risks as much as possible. According to NIST, vulnerabilities resulting from external identities can directly impact an organization’s security. By identifying and mitigating those risks, organizations can enhance their overall cybersecurity posture and better protect themselves against threats.
Function 2: Identify – Mapping and Understanding Organizational Assets and Risks
The Identity function covers identifying and prioritizing the organization’s current cybersecurity risks in alignment with the strategy and mission needs. This function involves identifying opportunities for improvement in policies and processes related to risk management and informing actions across all organizational functions.
A best practices framework can also help you recognize high-risk resources and identify common identities such as IT admins, developers, workforce and machine identities. Advanced solutions for account discovery, intelligence and auditing can help with ongoing control and visibility of your environment.
Function 3: Protect – Securing Risky Assets
The Protect function involves utilizing capabilities to safeguard sensitive assets and reduce or eliminate the risk of incidents. Outcomes covered by this function include identity management, authentication and access control, awareness and training, data security, platform security and the resilience of technology infrastructure.
Thorough identity security programs can help address all these subcategories. A unified set of solutions that enables secure access to organizational assets with intelligent privilege controls, regardless of the environment (i.e., cloud services, elastic workloads, long-lived systems and high-risk apps) is recommended. Solutions include:
- Credential management and rotation – including extensibility to workforce passwords and application secrets.
- Automated discovery and onboarding of privileged accounts.
- Adaptive multi-factor authentication (MFA) to secure access to resources.
- Support for access to cloud workloads and services with zero standing privileges (ZSP), with best-in-class control of time, entitlements and approvals (TEA) settings for access to cloud services.
- Native UX for privileged sessions to servers, elastic VMs and databases, cloud services and SaaS apps.
Function 4: Detect – Finding and Analyzing Attacks
The Detect function calls for continuous monitoring of assets and detecting anomalies from internal users and external vendors, as well as incident response and recovery solutions. Taking a proactive stance on risk management can significantly enhance your ability to uphold this function.
Centralized audit and identity threat detection and response (ITDR) capabilities, should be applied consistently across all sessions. This entails centralized monitoring of employee and external vendor access to corporate resources.
Function 5: Respond – Acting Upon and Containing Attacks
In the NIST CSF 2.0, the Respond function outlines the necessary actions to take upon detection of risky activities, including containment and eradication of incidents. It covers incident management, analysis, mitigation reporting and communication. The first step in this process is deploying your incident response (IR) plan and conducting an ongoing investigation to ensure an effective response.
Once again, intelligent privilege controls and expert remediation services can help you detect and identify threats faster, with broader coverage, quick response and minimal damage.
Function 6: Recover – Restoring Affected Assets
This function involves restoring assets and operations affected by the incident and executing the recovery portion of the IR plan. This function covers reporting, documenting and communicating the outcomes and consequences of the incident, both internally and externally.
Strong identity protections facilitate easier auditing of malicious access and can help reduce the damage and allow faster and easier recovery. For instance, access can be deemed invalid if not provisioned through a PAM solution. Additionally, through lessons learned, the recovery process identifies relevant attack methods, targeted identities and resources, which triggers new risk assessments and reassessments of the security roadmap and plan.
The six functions of NIST CSF 2.0 are circular and interconnected. Therefore, the greater the investment organizations make in preparing and implementing the necessary protections, the smoother their ability to respond to threats and recover from cybersecurity incidents.
Unified under CyberArk’s identity security platform, our solutions align closely with NIST’s approach, offering comprehensive support and services for securing all identities – human and machine – across hybrid and multi-cloud environments.
Lilach Faerman Koren is a senior product marketing manager at CyberArk.























