
In a pandemic-altered business world, one of the most striking developments that’s still unfolding is the global movement of workers rethinking what matters most — in work, life and everywhere in between.
Some call it the Great Resignation: The Labor Department said a stunning 4.2 million U.S. workers quit their jobs in October 2021 alone. Others call it the Great Reconsideration: A Harris Poll found that more than half of U.S. workers want to leave their jobs, with 76 percent citing a need for flexibility in how, when and where they work.
Either way, the pace and magnitude of employee turnover is unprecedented, and that’s affecting organizations’ strategies at every level — culture, operations, technology and, of course, security. In response, organizations are scaling up their efforts to find, hire and integrate new talent with a constant focus on empowering workers with the tools to thrive.
During such change, the only constant seems to be the need to make sure work-from-anywhere employees are up and running on the right applications, devices and systems with the right level of access. And on the flip side, it means being able to shut off access quickly and at scale to protect corporate assets amid personnel changes.
Exploring the role of virtual collaboration apps — and their inherent risks
According to Gartner®, nearly 80 percent of workers are using collaboration tools for work in 2021, up from just over half of workers in 2019.[1] If you’re working remotely some or all the time, collaboration tools are the primary means of interacting with co-workers, performing job duties and, in turn, driving your career forward. This includes mainstays such as Slack, Teams and Zoom that are used across industries and professions.
The trouble is all these changes — while full of opportunity — also open to the door to new threats. Every time an organization deploys any type of application to help workers do their jobs, this results in more identities to secure.
Here’s a snapshot of some interrelated access management workforce trends we’ll continue to see in 2022.
Fast turnover + remote work = trouble in assigning and revoking workers’ access
Every time a new worker enters the company or an existing one leaves, it’s another identity lifecycle management challenge for HR and IT to solve. Incoming talent needs new accounts and quick access to a range of critical applications. Meanwhile, organizations need to shut off most access for outgoing talent — and every time somebody falls through the cracks, productivity and/or security can take a hit.
Collaborative tools empower remote workers but also create new security headaches
Imagine a scenario in which a worker gives two weeks’ notice but then (with an eye toward getting a head start at a new job) retrieves a few files from a collaboration app’s shared folders. The employee isn’t planning to use any proprietary information after leaving the company — just some key points and slide templates.
But for some reason, weeks pass, and the now-former employee’s access still hasn’t been revoked. They can just dip in and retrieve old files whenever they want.
What could the harm be?
For starters, who’s managing the former employee’s credentials for the application? Not the employee, who’s moved on a new company and no longer getting monthly emails from their old IT team requiring password updates. And not the former employer, who’s unaware of the employee’s lingering access and — for the sake of this hypothetical scenario — doesn’t know the password for this application was weak, easy to guess and used across various accounts.
This lax approach to passwords is all too common and reflects a prime target for today’s attackers. Indeed, 97 percent of security leaders say end-user credentials make up the largest increase in attacks against their organizations. Relevant to the above example, cyber criminals look for dormant application accounts and stale privileges, which are security lapses that high workforce turnover can intensify.
Collaboration apps, in the wrong hands, can be the entrance to a virtual goldmine.
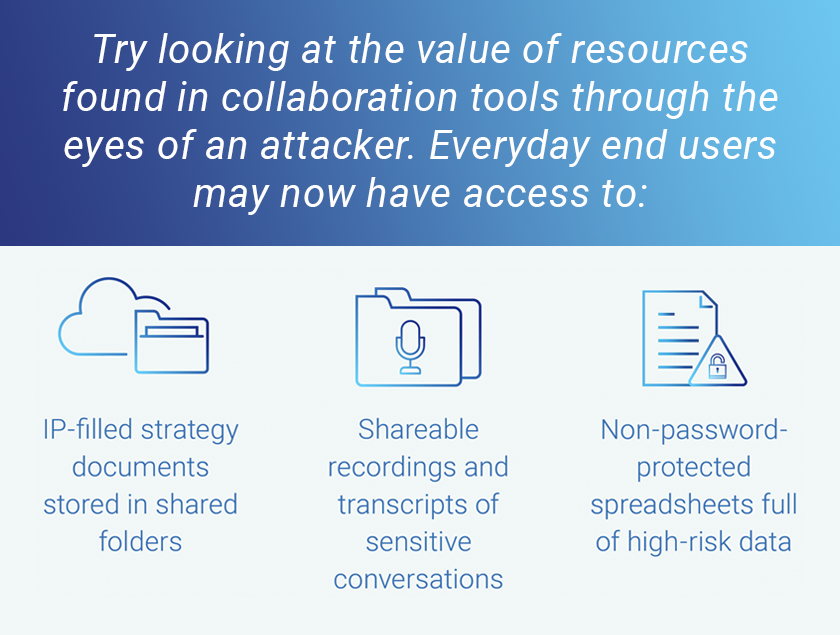
How to get ahead of converging workforce trends in 2022 and beyond
Even when collaboration apps with functions such as real-time chatting or video conferencing are deployed and work smoothly, they aren’t always fortified properly against malicious actors. A single failure in this area can translate to a world of difficulties by giving attackers a foothold from which to collect sensitive information or move on to other resources.
For IT and security leaders, it’s a good time to think about ways to update access management strategies to reflect the ever-changing workforce. Here are three areas to consider:
- In times of high turnover, employ AI and automation to make the tasks of granting, adjusting or revoking a worker’s access … well … more workable. This includes onboarding and offboarding, as well as career moves that not only change a worker’s job function but also the types of access they should (and shouldn’t) have within a collaboration application.
- Secure identities holistically by applying protection and transparency to not only the initial point of authentication but also to users’ activity within application sessions. This includes recording, monitoring and auditing activity in applications where users can take high-risk actions with high-value resources.
- Lastly, protect the wide range of endpoints that a distributed workforce now uses to gain access to applications, systems and data from distributed locations. This includes desktops, laptops and devices used at home, in the office and in public locations.
Final thoughts: Securing your workforce in times of constant change
Organizations have a major opportunity to empower their employees with applications that help them drive success for key initiatives, including apps that foster collaboration, creativity and a sense of community. The key is ensuring that your users’ engagement with these tools is secure — from the point of authentication, to the actions they take within the apps — and that their access is up to date, in light of any changes to their jobs.
In a world in which the so-called “future of work” is really anybody’s guess, we can count on the fact that every home office will be its own IT infrastructure, and the corporate perimeter requiring protection is essentially limitless, embedded into every identity. Getting ahead of the security risks of trends like the Great Resignation isn’t just forward thinking; it’s critical to securing your distributed workforce.
Read our new eBook “4 Global Workforce Trends Influencing Identity and Access Management Strategies” for insights on how to secure and empower your workforce.
[1] Gartner Press Release, “Gartner Survey Reveals a 44% Rise in Workers’ Use of Collaboration Tools Since 2019,” August 25, 2021. GARTNER is registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.























