In our mobile, cloud and digital world, physical perimeters have all but disappeared. Gone are the days when users and assets resided within the physical walls of the organization and trust was defined by the perimeter. Today, it’s impossible to contain — let alone trust — all of the people, machines and applications that must dynamically access company systems and data, so Zero Trust models are becoming more popular. Zero Trust, as the name suggests, means anyone and everything trying to connect to an enterprise system is verified before access is granted.
Of course, shifting from perimeter-centric security to Zero Trust is an evolution that takes time, along with a measured, risk-based approach across people, process and technology domains. For those looking to get started with a Zero Trust program, the National Institute of Standards and Technology (NIST) offers insights for building Zero Trust Architectures (ZTAs). Within NIST SP 800-207, the organization outlines 11 logical components within an ideal ZTA, along with migration and threat mitigation strategies and use cases.
Each of these components are meant to limit access to strongly verified identities to protect the integrity of enterprise resources and provide complete audit trails.
Here’s a look at the full architecture:
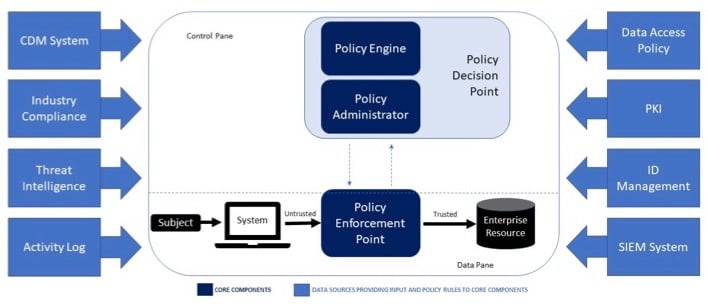
Source: NIST SP 800-207. Core Zero Trust Logical Components
The Core of the NIST Zero Trust Architecture
Three components — the policy engine, policy administrator and policy enforcement point — comprise the core of an enterprise Zero Trust architecture. The policy engine makes the ultimate decision to grant access to the human, machine or application user based on enterprise policy, input from external sources (such as the continuous diagnostic mitigation system or threat intelligence services) and a trusted algorithm. More on that algorithm in a minute.
The policy administrator is responsible for establishing or shutting down the communication path between the user and the target resource. Once it receives the policy engine’s ultimate approval to grant access, it commands the policy enforcement point to initiate a session through the credential, key or token used by the user to access the enterprise resource.
Meanwhile, the policy enforcement point acts as the gatekeeper for the communication path. It is responsible for enabling, monitoring and terminating sessions (when necessary) between the human, machine or application and the target enterprise resource.
A Trust Algorithm to Rule Them All
Because these three core systems are inextricably connected, NIST recommends instituting a trust algorithm, which is built on observable (entity and enterprise system) information in the ZTA. It builds on data access policies and is refined via the organization’s threat intelligence feed(s).
NIST recommends that controls put in place to grant access to systems be responsive not only to policies, but also to an overall trust score that can influence policy evaluation. This score can be calculated through a single evaluation of the algorithm, or it can dynamically change over time based on things like entity behavior patterns.
Eight Data Sources Drive Zero Trust Access Decisions
NIST’s remaining eight logical ZTA components are data sources that provide critical input and policy rules to the core and enable the appropriate access decision. These include:
- Public key infrastructure generates and logs certificates issued by the enterprise to resources, subjects, services and applications.
- Identity management provides a good baseline for a higher degree of trust around entities, through the use of identity proofing.
- Data access policies provide a domain of understanding and controls around what is acceptable behavior for the entities.
- Continuous diagnostic mitigation (CDM) system monitors, reports and corrects on the integrity of systems in the enterprise architecture and relies on support the threat intelligence feed(s).
- Threat intelligence feed(s) provides information from internal or external sources, such as information on newly discovered attacks or vulnerabilities, to help the policy engine make access decisions.
- Industry compliance, security incident and event monitoring (SIEM) system, and network access and activity logs serve to collectively audit and track events and activities, providing analysis or reporting on the access records.
Stand Up Your Zero Trust Architecture with Privileged Access Management
While there are several ways enterprises can get started with Zero Trust, strong privileged access management controls are essential to establishing NIST’s three core architectural components.
Policy engine. Privileged access management solutions enforce authentication and authorization policies for privileged users leveraging enterprise policy and analytic algorithms that track behavioral patterns. Anomalous behavior, such as requesting access from a new location or outside of normal business hours, can trigger alerts so incident response teams can take immediate action.
Policy administrator point. By establishing isolation layers between endpoints, users and target systems while continuously monitoring access, privileged access management solutions secure the communication path between privileged users and target resources. This means you’ll know who gained access, what that user accessed, and exactly when (and for how long) the access was granted.
Policy enforcement point. Privileged access management helps you remediate risky behavior by automatically suspending or terminating privileged sessions based on risk assignment. It can also initiate automatic credential rotation in the event of privileged credential compromise or theft, and keep a full audit record to simplify compliance and aid remediation, when necessary.
Privileged access management solutions are designed to protect your most critical systems and assets — the core of your enterprise. With the right tools, you can grant access to strongly verified identities and leverage integrations with leading security solutions to optimize access policies.
By encompassing the key elements of Zero Trust — verification and monitoring — privileged access management empowers organizations to prevent credential theft, stop lateral movement, limit privilege escalation and abuse, and ultimately, protect what matters most.
Learn more in this on-demand webinar and tap into the CyberArk Blueprint for Privileged Access Management Success for prescriptive guidance on designing core ZTA workflows.
Editor’s Note: Thanks to Carlos Condado who contributed to this blog post.

















