
The increased use of electronic personal health information (ePHI) coupled with rapid advances in healthcare technology – from cloud-based applications to IoT-enabled devices to telemedicine – has created complex healthcare delivery networks that are target-rich environments for cyber attackers.
Outdated and unsupported software, a massive cyber security skills shortage and rapidly evolving technology have left hospitals and healthcare systems vulnerable to ransomware and internal threats to ePHI – both malicious and those resulting from human error. All the while, regulations around ePHI, such as HIPAA HITECH and GDPR, continue to increase while non-compliance is bringing stiffer penalties, particularly with regard to privileged access management.
According to Verizon, “58% of incidents involved insiders—healthcare is the only industry in which internal actors are the biggest threat to an organization. However, the attack vectors are expansive in healthcare. When it comes to privileged access, you have to consider all of the human points of access, including people with administrator rights, along with non-human access – including the applications and medical devices that interact with critical systems and enable fundamental processes such as integrating patient diagnostic data from third-party services or seeking reimbursement from a payer organization.
Managing access to privileged accounts, credentials and secrets is an effective way to limit the moves a threat actor can make after they establish a foothold on the network. With privileged access security measures in place, an attacker’s ability to escalate privileges and move laterally to access sensitive systems will be minimized. Proper cyber security hygiene in an environment where the stakes are so high is absolutely critical. This starts with effectively managing privileged access.
The Current Healthcare Environment
Innovation continues to introduce new technologies that improve patient care, but could leave organizations at risk. With ePHI now being dispersed across expansive networks of patient monitoring devices, mobile endpoints for employees and self-service patient web portals, the risk to healthcare providers continues to evolve. Only those organizations that take a holistic approach to securing their environments – including correct privileged access control – will reduce the risk of a catastrophic cyber security incident.
Building “high walls” to protect an organization’s perimeter is an outdated approach to security. According to the CyberArk Global Advanced Threat Landscape Report 2018, 52 percent of healthcare IT decision-makers cannot prevent attackers from breaking into their networks, and 59 percent believe that customers’ personally identifiable information (PII) could be at risk. Therefore, we challenge organizations to assume that a breach will happen and to implement security tools that prevent an attacker from gaining access to sensitive systems.
Tightening Regulations and Harsher Penalties
As ransomware and other cyber attacks continue at an alarming rate, IT organizations face an increasingly tight regulatory environment. Strong privileged access security (or the lack thereof) can make or break a healthcare organization’s ability to demonstrate compliance and avoid financial penalties. This was illustrated last year, when Florida-based Memorial Healthcare Systems (MHS) agreed to pay the U.S. Department of Health and Human Services (HHS) $5.5 million to settle violations of HIPAA HITECH rules. This fine was a result of failure to review access controls and examine audit logs, giving unauthorized employees access to ePHI through shared login credentials.
The following diagram from HIPAA Journal outlines the potential penalties healthcare organizations face for non-compliance with HIPPA HITECH. As evidenced in the MHS case, penalties for “willful neglect” can reach millions, and under certain conditions, penalties can now extend to third-party contractors and business associates.
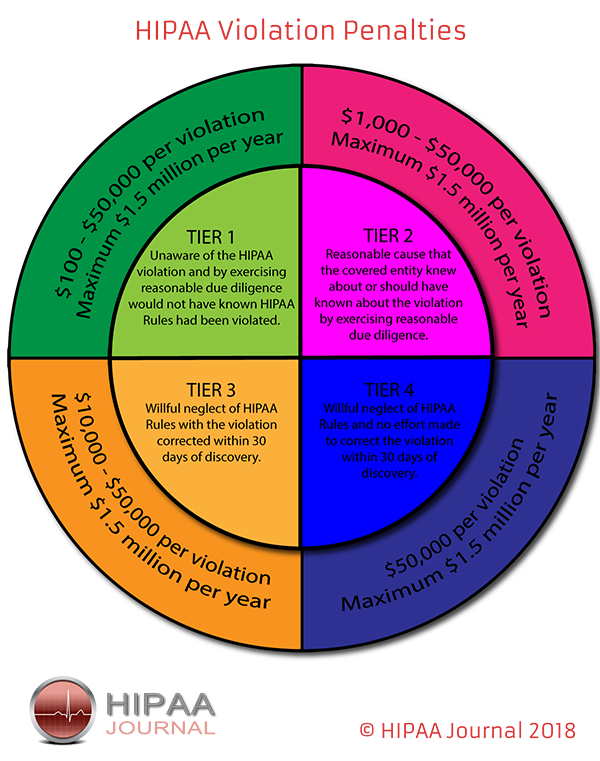
SOURCE: HIPAA JOURNAL (https://www.hipaajournal.com/hipaa-violation-fines/)
Beyond these regulatory penalties, there are significant operational costs to recover from a data breach. A Ponemon study found that a healthcare data breach costs on average $380 per record – more than 2.5 times the global average across industries.
To demonstrate compliance with HIPAA HITECH, GDPR and other industry regulations, healthcare providers must have access to documented, auditable proof of their efforts to protect privileged access. Audit trails require a solution that enables comprehensive monitoring, recording and isolation of all privileged user sessions, detailed activity reports on critical ePHI databases and applications, fully searchable audit logs, and complete, multi-layered audit trail data protection.
Protecting Your Integrated Care Delivery Network Investment with CyberArk
Organizations must manage privileges to proactively protect against, detect and respond to attacks in progress before attackers compromise vital systems and data. But managing privileges does not mean denying them. Instead, it is a matter of controlling who has access to what and why. Managing privileged access is a part of basic cyber security hygiene and can have a huge, positive impact on an organization’s security posture and compliance efforts.
Because privileged access security complements existing security tools, it helps organizations leverage their existing cyber security investments towards demonstrable improvements. Privileged access security is an essential first step in maturing healthcare cyber security program and must be a priority.
The CyberArk Privileged Access Security Solution provides proactive, automated, end-to-end detection and protection for all privileged access to systems containing ePHI. Privileged threat detection and analytics provides the ability to respond and remediate to any anomalous or high-risk activities. Monitoring the behavior of privileged activity to ensure users are not disabling, circumventing or altering implemented security safeguards and controls is not only a best practice but often required by regulations.
An enterprise architect at a major public research university health system commented, “Our systems are critical to patient care. Compromised account credentials or compromised applications can lead to PHI/PII exposure and/or outages to patient care systems. The CyberArk Privileged Access Security Solution gives us the ability to expose and understand where our risks are, allowing us to take steps to secure things better.”
To learn more about how CyberArk can help your healthcare organization protect its investments, simplify compliance and continue to deliver the highest quality patient care, read more on our website here.






















