
The U.S. Department of Defense (DoD) is going all in on Zero Trust. In late 2022, the Pentagon released its long-anticipated Zero Trust strategy and roadmap for migrating “trusted” perimeter-based networks to a department-wide Zero Trust framework by fiscal year 2027. It’s an ambitious step for the nation’s largest employer of 3.4 million people, but it’s critical.
DoD Principal Deputy Chief Information Officer John B. Sherman didn’t mince words about the agency’s cybersecurity stance, writing, “Our adversaries are in our networks, exfiltrating our data, and exploiting the Department’s users.” This assume breach mindset goes hand-in-hand with the Zero Trust philosophy of denying access by default and verifying every identity – human and machine – to protect sensitive government assets and reduce the risk of data breach.
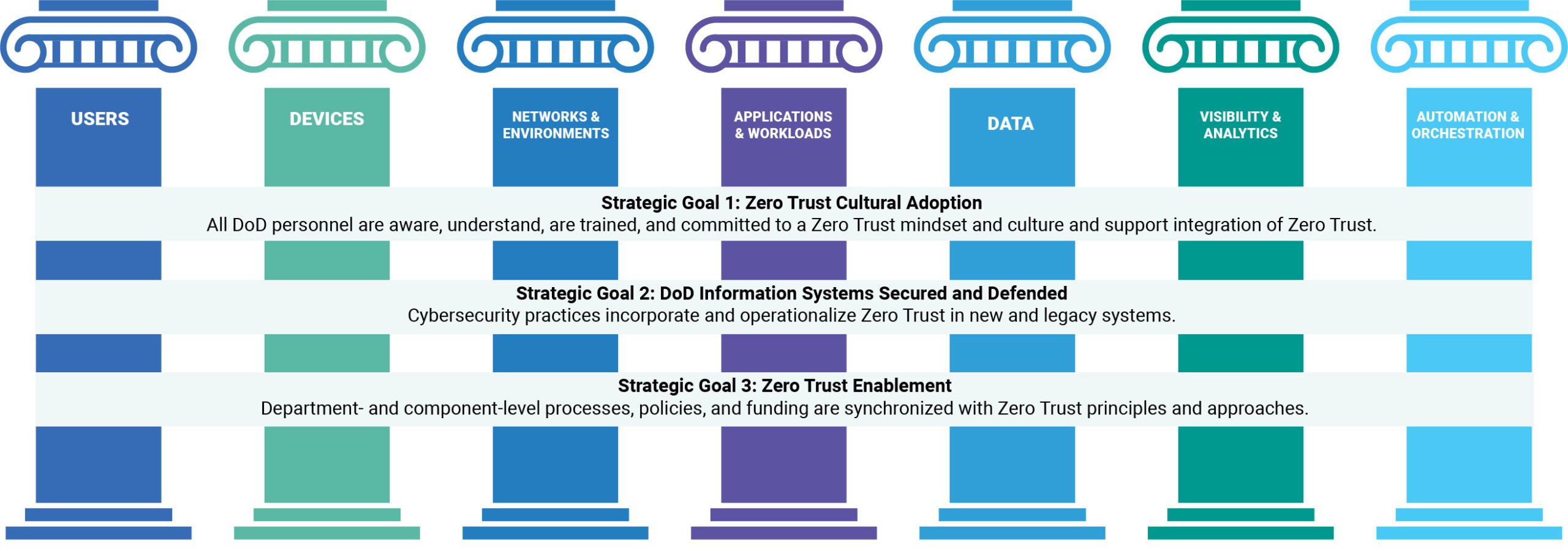
The DoD’s Zero Trust Strategy at a Glance
The DoD’s Zero Trust strategy calls for layered cybersecurity controls for existing IT infrastructure and cloud services to “reduce the attack surface, enable risk management and effective data-sharing in partnership environments, and quickly contain and remediate adversary activities.” It spans seven pillars and aligns to four high-level goals, shown below. Every agency within the DoD must implement baseline capabilities across these seven pillars to achieve compliance – or “targeted Zero Trust.” Certain organizations must implement more “advanced Zero Trust” capabilities based on system and information sensitivity.
Identity Security is a Must for Achieving Government-Wide Zero Trust
The DoD’s Zero Trust plan is part of a broader, government-wide push to strengthen defenses against constant and increasingly sophisticated attacks. In the spring of 2021, the White House issued an executive order outlining guidelines for modernizing and securing federal digital infrastructure. A Zero Trust architecture strategy followed in early 2022 that emphasized identity-centric security, without which “adversaries can take over user accounts and gain a foothold in an agency to steal data or launch attacks,” wrote authors.
Now comes the more difficult job of operationalizing Zero Trust, which requires a complicated mix of policies and technical controls, along with a massive cultural shift, to be successful. Fortunately, federal stakeholders and partners have the Zero Trust Reference Architecture (ZT RA), a prescriptive playbook developed by the Defense Information Systems Agency (DISA) and National Security Agency (NSA) to guide their efforts. Among its guiding principles is the “strict enforcement of identity-based authentication and authorization for all connections and access to infrastructure, data, and services.”
Addressing Key DoD Zero Trust Requirements with Identity Security Controls
Of course, identity isn’t the sole security focus in an agency’s Zero Trust journey, but it’s a big one. Modern Identity Security controls – centered on privilege controls and combining strengths of identity and access management (IAM), identity governance and administration (IGA) and privileged access management (PAM) – work in concert to mitigate the risk of advanced cyberattacks and meet many of the DoD’s Zero Trust requirements, while providing a strong Zero Trust foundation on which to grow:
Users. Adaptive multifactor authentication (MFA) paired with strong passwords secures identities and to authenticate the identity of every user – employee, partner or contractor. After login, these user identities can be revalidated to help ensure they should have access and reauthenticated for sensitive actions or after periods of inactivity.
Meanwhile, intelligent privilege controls make it possible to enforce least privilege – a Zero Trust “must” – consistently for both human and machine identities (i.e., service accounts) across any device, anywhere. Users only get only the permissions needed to perform a specific task, for just the right amount of time. And sessions – for both privileged and workforce users with high-risk access – are continuously monitored and analyzed to help agencies quickly detect and respond to threats.
Devices. User devices are gateways to highly sensitive government resources and prime targets for phishing and ransomware attacks. Identity Security controls make it possible to authorize user devices at each access request, and automatically detect security issues. Automated detection controls that block credential theft (via software abuse or memory scraping) are key to slowing down and containing attacks early on – before they circumvent other defensive layers and cause damage.
Networks and Environments. The traditional perimeter is dead, making “flat” networks even more dangerous. Creating credential boundaries makes it harder for attackers to get from “point A” to “point B,” and to their ultimate target. Session web session management for all users helps strengthen these boundaries and create extra layers of security. For instance, by isolating sessions to critical resources to prevent malware from spreading, and enforcing granular access control to improve individual accountability.
Applications and Workloads. The Zero Trust “never trust, always verify” mantra doesn’t just apply to people – especially since machine identities outnumber human identities 45:1. All calls from machine identities seeking access to network resources must be protected. Credentials should be managed and automatically retrieved, and access is securely granted to applications and bots – with the same robust Identity Security controls used for human identities. Likewise, secrets used across the DevOps pipeline must be managed appropriately to protect applications and the broader digital supply chain.
Visibility and Analytics. Thanks to advancements in artificial intelligence (AI), security teams can put analytics engines to work to better visualize, understand and detect their identity-centric risk profile. This gives them a simpler, more effective way to baseline typical user or device behavior, assign risk to each access event, automatically flag issues, identify protect and protect against of risky access conditions over time.
Automation and Orchestration. The vast number of human and machine identities across government networks today represent a greatly expanded attack surface that adds pressure to mounting compliance requirements. Implementing processes to automate the identity lifecycle through seamless, no-code application integrations and workflows can help agencies take control of excessive permissions to enforce least privilege and move closer to Zero Trust.
The DoD’s new Zero Trust strategy outlines clear requirements and timelines, and agencies need outcome-driven solutions to meet their Zero Trust charge. As the established industry leader, CyberArk offers the most complete and extensible Identity Security Platform, protecting identities and critical assets by enabling Zero Trust and enforcing least privilege. With multiple DoD customers and more than 130 installations across the U.S. federal government today, CyberArk stands ready to help government organizations secure sensitive data and infrastructure, fulfill their Zero Trust mandates and achieve mission success.



















