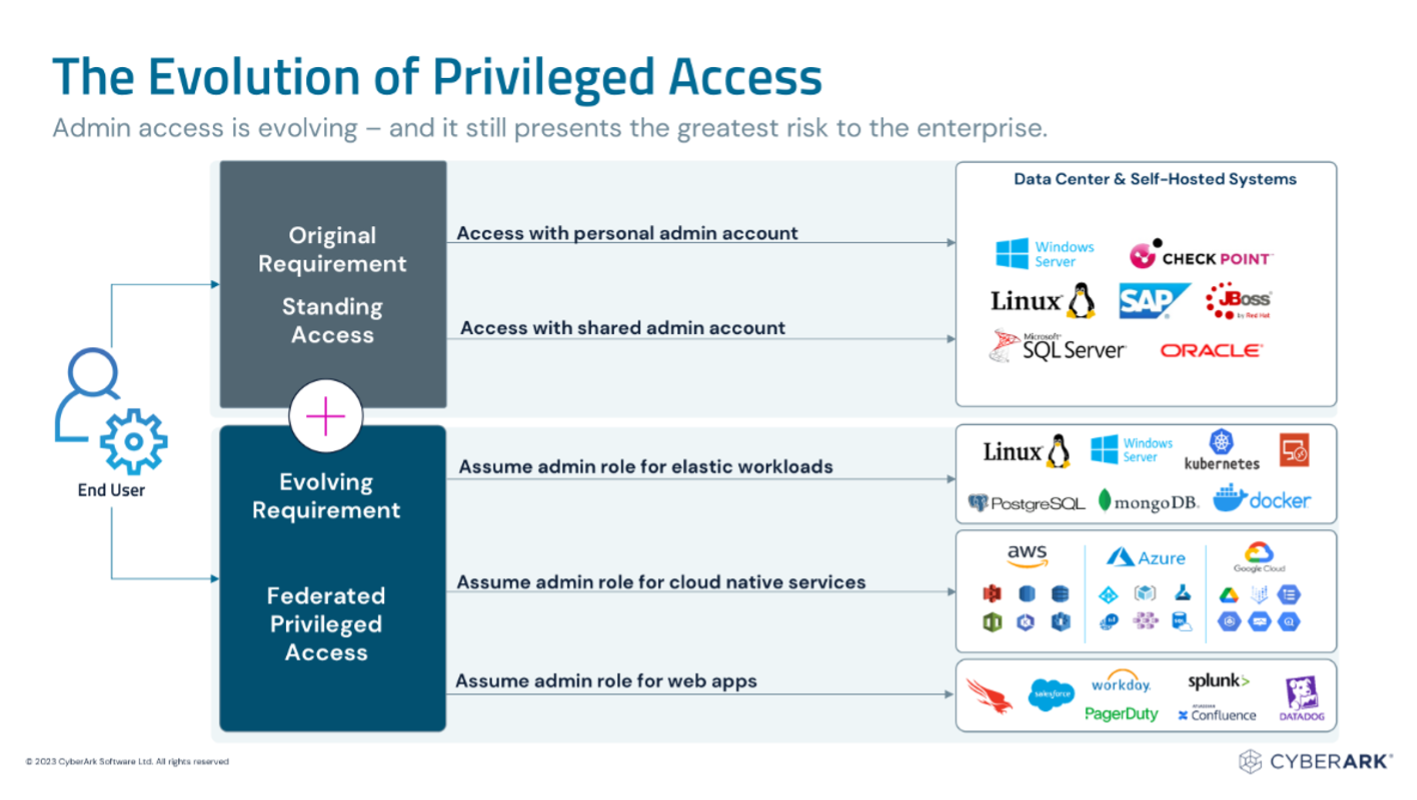
In today’s digital landscape, Privileged Access Management (PAM) has evolved beyond rotating and vaulting privileged credentials for long-lived systems. As organizations expand cloud investment and scale sustainable hybrid work, PAM has also grown into a multi-faceted discipline that must secure all identities across the enterprise.
The 2024 Gartner® Critical Capabilities for Privileged Access Management1 – link to reading copy – outlines six Use Cases organizations should evaluate across PAM solutions:
- Privileged Account and Session Management (PASM)
- Windows Privileged Elevation and Delegation Management (PEDM)
- Unix/Linux/Mac Privileged Elevation and Delegation Management (PEDM)
- Secrets Management
- Cloud Infrastructure Entitlement Management (CIEM)
- Remote PAM
In this post, we’ll explore our state-of-the-art in these Use Cases and how we believe they align to modern PAM programs.
Privileged Account and Session Management (PASM)
Secure Access, With or Without Vaulted Credentials
Modern PAM programs extend PASM beyond traditional credential vaulting to secure access across elastic Infrastructure-as-a-Service (IaaS) workloads, IaaS resources and Software-as-a-Service (SaaS) applications. IaaS and SaaS providers recommend federating privileged access to roles, rather than specific privileged accounts and passwords to access shifting target systems. We believe PAM programs must support privilege controls and low-friction user experiences for your entire hybrid IT environment.
Continuous Authentication and Zero Standing Privileges
“The principle of least privilege should guide the vision of every PAM practice and several strategies for PAM, including time-based access to shared-privileged accounts, JIT and zero standing privileges (ZSP). The risk of privileged accounts, stemming from the permissions they carry, can be mitigated by taking a JIT approach. JIT means privileges are available only when they are required to fulfill legitimate operational needs and at the appropriate level. The purest form of JIT is ZSP, which means there are no standing privileges, and all administrative access is defined and allocated on a JIT basis.” 1
Emerging best practices for PASM include implementing controls within a user’s native tooling (e.g., RDP, SSH, Cloud CLIs) and continuous authentication for privileged sessions: sessions are continuously monitored and re-validated. Paired with the adoption of a Zero Standing Privileges (ZSP) model, this significantly reduces the risk of malicious lateral movement within enterprise environments.
Windows Privilege Elevation and Delegation Management (PEDM)
Beyond Removing Local Admin Rights
Traditional PEDM solutions remove the need for users to have admin rights by automatically elevating privileges for native applications, thus reducing IT support tickets and burden.
As ransomware threats evolve and become sophisticated enough to disable Endpoint Detection and Response (EDR) tools, cyber insurers and compliance frameworks have taken notice: “PEDM tools are often a mandatory requirement for regulated industries and where compliance with PCI DSS, SOX and other regulatory and financial controls are stipulated. Defense and government environments also often mandate the removal of local administrative privileges.” 1
Modern PEDM tools should:
- Automatically detect and eliminate local admin rights.
- Harden the operating system (OS) to reduce attack surface.
- Discover, suggest and enforce policies for application control.
- Restrict endpoint resource and data access.
- Enforce least privilege.
We believe modern security should incorporate endpoint identity security, with capabilities that include credential and browser protection; continuous authentication; and strong, phishing-resistant multifactor authentication (MFA) for high-risk application access to prevent account takeovers.
With the complexity of security toolsets growing, customers are asking for frameworks, templates and assistants to simplify initial set up, day-to-day operations and governance. CyberArk provides a Blueprint best-practices framework and AI-based policy recommendations to help teams achieve compliance and navigate least privilege enforcement with ease.
Unix/Linux/Mac PEDM
Cross-Platform Consistency and Security
Unix, Linux and Mac environments are often overlooked when it comes to PEDM, but they are just as crucial in a comprehensive PAM strategy. Strong PEDM solutions ensure consistent privilege management for diverse operating systems and server use cases, centralizing visibility, management and consistent ease-of-use. Key capabilities feature “AD bridging, which applies AD controls to Linux/UNIX systems, including the ability to authenticate to these systems with AD credentials” 1, and sudo management — the ability to dynamically manage and monitor sudo rights. Leading solutions add additional layers of defense-in-depth security by combining this with session isolation, automatic credential management and detailed access controls.
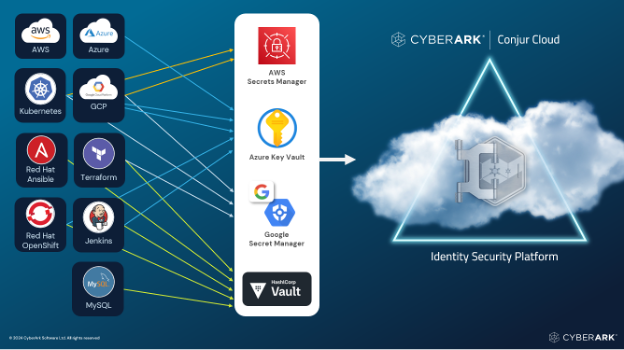
Secrets Management
Scaling Securely in a Multi-Cloud World
As organizations scale their DevOps practices, the challenge of managing secrets with a consistent security policy and audit trail has significantly grown. For example, Microsoft recommends using one Azure Key Vault, per application, per environment per region. “Secrets management scenarios are typically dynamic – as, for example, with brokerage of trust between individual applications, services or devices, containers and DevOps pipelines.”1
Centralized Secrets Management
PAM programs address this specialized use case by offering a solution that integrates seamlessly with popular DevOps tools like Terraform, Jenkins and Kubernetes. This approach not only helps secure secrets at scale but also prevents vault sprawl, providing a unified solution for managing secrets across the enterprise.
Advanced Cloud Integration
If developers don’t adopt security tools, the result is shelfware. User-friendly solutions also extend to native cloud secret stores, such as AWS Secrets Manager, Azure Key Vault and Google Cloud Secrets Manager. By integrating with these platforms, innovative secrets management allows organizations to enforce robust security controls, including automatic rotation of secrets, without disrupting existing DevOps workflows. This ensures that security is maintained without hindering development velocity.
Cloud Infrastructure Entitlement Management
Adapting to the Dynamic Nature of Cloud Environments
The dynamic and ephemeral nature of cloud environments presents unique challenges when managing entitlements and permissions. Many PAM solutions often struggle to keep up with the pace of cloud workloads, which are constantly spinning up and down. This makes them significantly easier to access with federated workflows, as opposed to shared accounts that must be created for every ephemeral server. CIEM capabilities provide real-time visibility and control over cloud entitlements, applying the tried-and-true first principle of least privilege to the cloud. By helping organizations continuously monitor and adjust permissions, CIEM solutions reduce the risk of over-privileged access, a common misconfiguration seen in cloud environments.
Zero Standing Privileges in the Cloud
A cornerstone of modern PAM programs is the enforcement of Zero Standing Privileges (ZSP) in the cloud. By creating roles with privileged entitlements on demand and removing them immediately after approved use, organizations can ensure that in the case of account takeover or stolen credentials, there are no residual privileges to exploit. This approach is critical in mitigating the risks associated with over-permissioned accounts and roles, helping organizations extend a strong security posture to dynamic cloud environments.
Remote PAM
Securing Remote Access in a Distributed Workforce
Traditional approaches to remote access, such as VPNs and jump servers, introduce security risks due to lack of granular control and limited visibility. In today’s distributed work environments, these methods are no longer sufficient to ensure secure remote access for privileged users and third-party vendors.
Modern Remote PAM: Beyond VPNs
Effective PAM solutions redefine secure remote access by focusing on JIT provisioning, session recording and endpoint posture checks. These controls ensure that remote access is granted only to authorized users from secure devices and that all privileged activities are monitored and audited. Together, these capabilities are essential in reducing the attack surface and preventing unauthorized access.
Securing Remote Cloud Access
We believe that third-party privileged access doesn’t stop in the data center. Organizations must address the unique challenges associated with remote access to cloud environments. This includes protecting browser sessions, managing identity cookies and enforcing continuous authentication. By securing these access points, CyberArk ensures that privileged access to cloud resources remains secure and compliant across remote and third-party work scenarios.
Modernize Your PAM Program for a Multi-Cloud World
The evolving nature of IT environments — driven by cloud adoption, DevOps practices and remote work — demands a modern, comprehensive approach to Privileged Access Management. We believe the CyberArk Identity security platform embodies this approach by addressing these six use cases outlined by Gartner, while also extending its focus to emerging needs like workforce identity management and DevOps security.
Key Benefits of CyberArk’s Approach:
- Reimagine Workforce Identity Security: Provide secure access to necessary tools and resources for all users, enhancing productivity while maintaining security.
- Modernize IT with Least Privilege and Zero Standing Privileges: Minimize the attack surface and limit potential damage from compromised accounts and roles used by administrators.
- Secure Developers: With multilayer protection for federated access to cloud workloads, secrets and machine identities, you can protect sensitive data and resources. Enforce least privilege from the endpoint to the cloud and protect developer workstations from identity-based attacks. Integrate security into development processes without sacrificing speed or agility.
- Scale the Rise of Machine Identities: CyberArk automates the management of machine identities, including for service accounts, bots and IoT devices. This automation helps security scale with machine identities without additional operational complexity.
With the CyberArk Identity security platform, organizations can consolidate their security stack, reduce operational complexity and achieve a resilient security posture against modern threats.
Get your complimentary copy of the Gartner Critical Capabilities for PAM report.
Evolve your PAM program in tandem with your IT environment. Embrace a modern approach to privileged access management with CyberArk and secure your organization against today’s evolving threats.
1 – Gartner® Critical Capabilities™ for Privileged Access Management, by Paul Mezzera, Abhyuday Data, Michael Kelley, Nayara Sangiorgio, Felix Gaehtgens, 9 September 2024.
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
Gartner does not endorse any vendor, product or service depicted in its research publications and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.