
Trust lies at the heart of every relationship, transaction and encounter. Yet in cyberspace—where we work, live, learn and play—trust can become elusive.
Since the dawn of the Internet nearly 50 years ago, we’ve witnessed incredible digital transformations paired with increasingly formidable threats. Knowing who and what to trust has become so difficult that the very notion of trust has been flipped on its head. This new philosophy of “never trust, always verify” is widely accepted, yet implementing Zero Trust effectively across technology infrastructure, partner ecosystems and even daily digital interactions can still be challenging.
I recently had the honor of discussing trust in cyberspace with a group of global technology leaders as part of CyberArk’s 10-year celebration as a public company at Nasdaq. Following are highlights from our wide-ranging conversation, along with some key considerations for building an anti-fragile digital ecosystem.
The Importance of Building Trust
“Trust is built in drops and lost in buckets.”
I can’t take credit for this quote—it belongs to Kevin Plank, founder of Under Armor—but it’s one of my favorites. As CIO at CyberArk, building trust internally and externally is integral to my job. In fact, forging trust is THE most essential part of any software provider’s job. And as the world becomes increasingly interdependent, this also becomes the most challenging part.
Virtually every organization relies on third-party products and services—and for good reason. SaaS makes teams more efficient and effective and can strengthen security. Cloud platforms fuel innovation by lowering barriers to entry and eliminating back-end IT infrastructure headaches. Meanwhile, generative AI has ushered in an exciting new wave of productivity, quality and creativity.
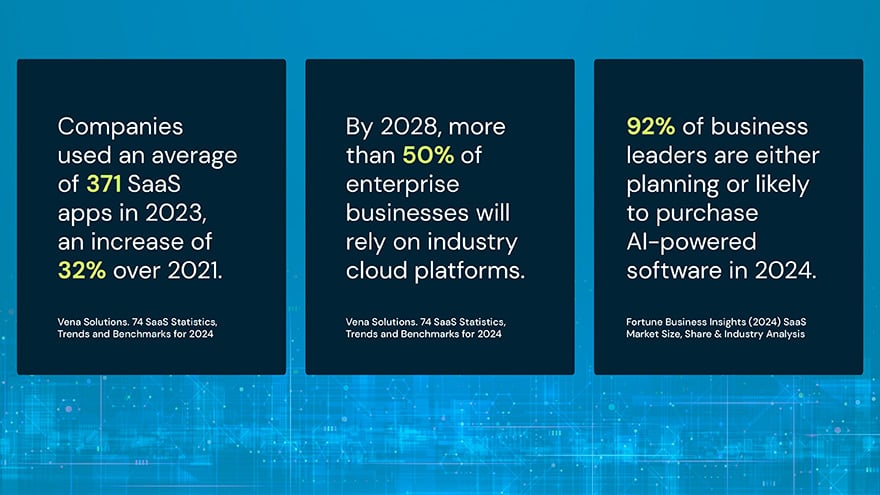
With any technology disruption comes risk, and risk cascades downhill. According to research from data science firm Cyentia Institute, the average organization does business with 11 third parties, and 98% of organizations do business with a third party that has suffered a breach. Those numbers and associated risks quickly balloon when fourth-party relationships enter the picture: the average firm has indirect relationships with 200 fourth parties that have been breached.
A compromise on one party can lead to a compromise on all. Consider the recent attacks targeting cloud storage firm Snowflake customers, which snowballed into a massive global breach.
Yet the notion of trustworthiness goes beyond cybersecurity. Increasingly, the narrative is shifting to resilience. The July 2024 CrowdStrike incident—in which a corrupt update file crashed millions of Windows-based machines worldwide—highlighted an inherent trust gap in today’s interdependent cyberspace architecture. Though the internet’s early founders took decentralization precautions to avoid such catastrophic events, we’ve reached a point today where some significant single points of failure jeopardize its resilience.
Bridging the Trust Gap
In this environment, organizations must rely on partners who can demonstrate their ability to uphold service availability requirements, secure environments and protect data. Building trusted vendor partnerships starts with a solid strategy and guardrails for good decision-making, such as certifications (i.e., ISO and SOC2), frameworks (i.e., SBOM), third-party risk scoring mechanisms, clear contract terms and conditions and many other aspects (i.e., MFA, data at rest encryption and patch management requirements).
As GenAI use surges, organizations are increasingly focused on ways to understand and govern the AI-based tools of their third-party vendors. While frameworks are evolving, the most crucial consideration—at least for now—is that the customer organization’s data is safe. Some critical questions to ask potential partners include:
- What steps does the vendor take—including using GenAI—to improve product resilience and security?
- Does the vendor follow privacy best practices? For instance, can customers opt out of certain features to ensure their data remains theirs?
- Are vendor employees required to use MFA and other identity security mechanisms to access customer data?
Building trust with third-party vendors must be balanced with building internal resilience to prepare for an inevitable black swan event. By embracing an “assume breach” mindset and continuously stress-testing contingency plans and processes, teams will be better prepared to respond and prevail.
Ensuring a Resilient Cyberspace for Our Future
Bridging the trust gap to ensure a resilient cyberspace for all requires collaboration on many fronts—beginning with stronger public-private partnerships. Recent strides made by the U.S. CISA, NSA, Cyber Command and several major tech corporations to share threat intelligence, mitigate attacks and promote secure by design practices are very encouraging. The behind-the-scenes collaboration happening right now to protect the U.S. 2024 election is a great example. In an unprecedented year marked by AI-based deep fakes and misinformation campaigns, these partnerships are crucial for defending democracy and preserving modern infrastructure.
Building on these resilience efforts is what I call the Solution Hygiene Framework, another mechanism organizations can utilize in their own cyber resilience journeys.
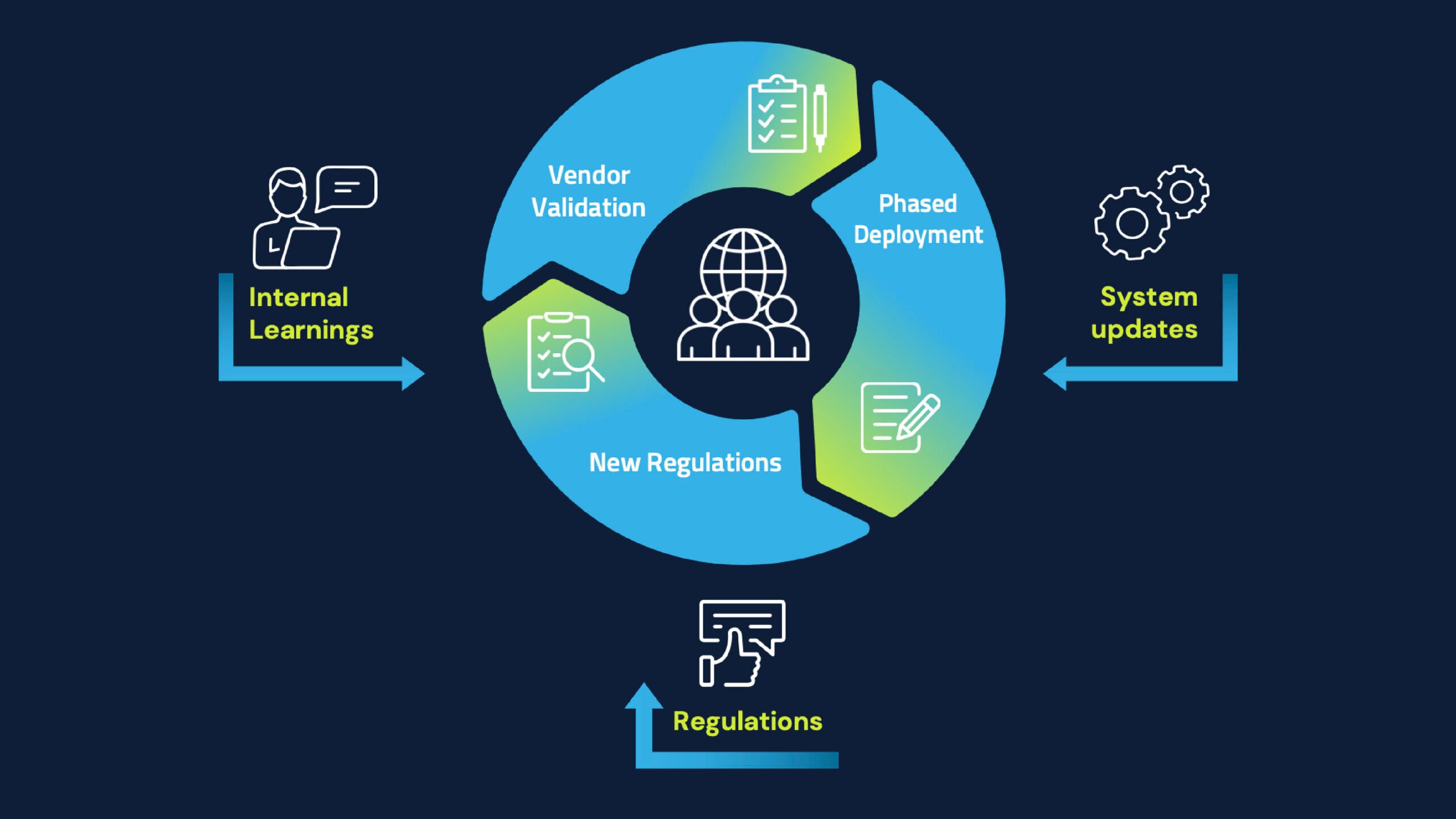
This three-pronged framework includes:
1. Vendor validation, mapping the organization’s complete vendor ecosystem and identifying critical ones. It’s important to establish an annual cadence (at minimum) for evaluating vendors to identify any changes, both good (such as a new certification with a better recovery time objective that supports its availability) and bad (such as a recent breach).
2. Regulation assessment must be a continuous exercise since regulations—from new AI acts to GDPR updates to MITRE framework changes to new NIST standards for post-quantum encryption—are constantly evolving.
3. System updates happen over time in a phased sequence as the world continues to change and new lessons are constantly learned. Our digital landscape is defined by new attack methods, technologies, identities and regulations, and only through thoughtful, risk-prioritized updates can organizations build truly resilient digital infrastructures.
It Begins and Ends with Trust
Trust is vital to business resilience and success. If we lose it, the internet will cease to be a powerful tool for good. But if we preserve it, we can unleash infinite possibilities.
I’m optimistic that we can realize a brighter digital future together by focusing on trust—building it drop by drop, maintaining it, evaluating it and continuously investing in it.
Omer Grossman is the global chief information officer at CyberArk. You can check out more content from Omer on CyberArk’s Security Matters | CIO Connections page.






















