In today’s dynamic threat landscape, a robust identity security strategy is paramount to protecting enterprises. With the digital perimeter extended to every user identity, securing access across your complete environment – on-premises, multi-cloud and everything in between – is no longer optional, but essential.
For enterprises leveraging Microsoft E5 licenses, security leaders are considering resources and budget to activate Azure Privileged Identity Management (PIM) to help manage Azure identities.
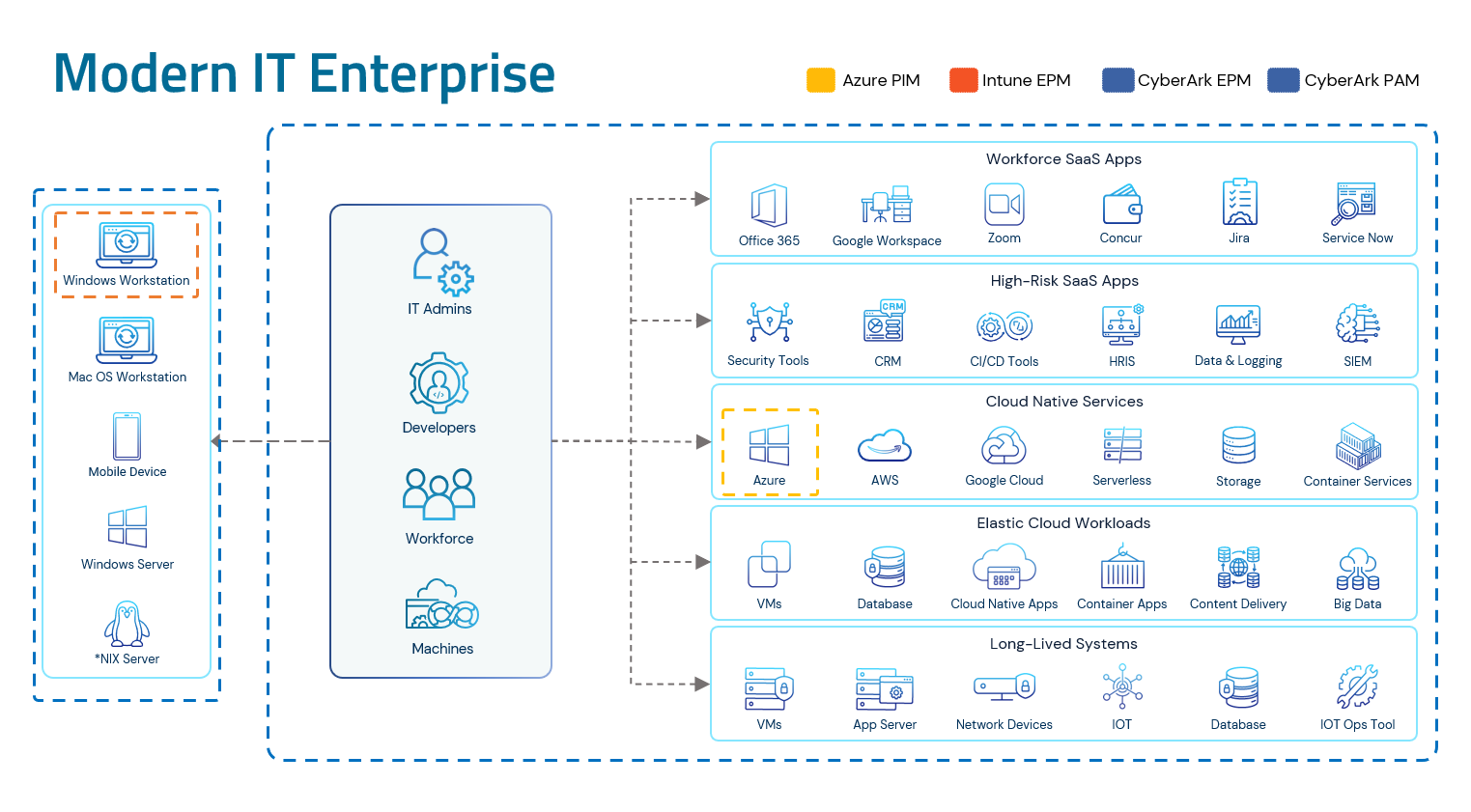
Together with the CyberArk Identity Security Platform, organizations can deliver a consistent identity security strategy without sacrificing native workflows and user experience. This includes IT Admins, developers, the workforce and especially machine identities and secrets, as that is the fastest-growing segment across enterprises today.
We can help you expand, measure and report on a multi-layer strategy that protects your highest-risk users (including third-party vendors), sessions, endpoints and non-human identities across the modern hybrid IT environment.
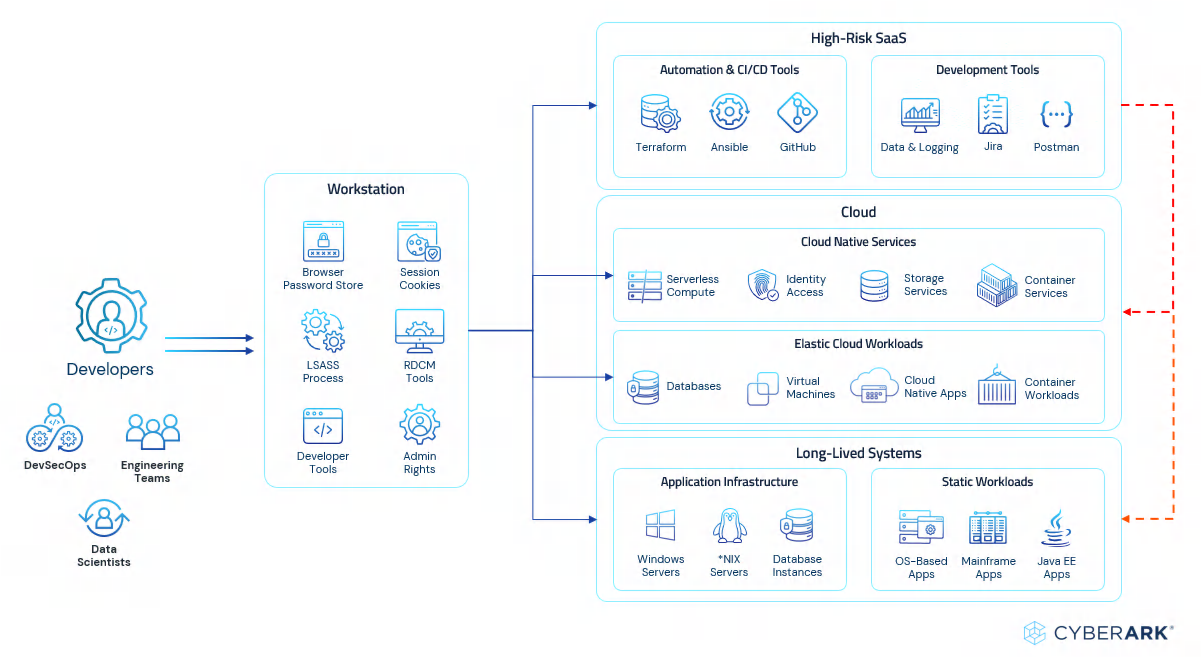
Architecture Diagram
The following illustrates how CyberArk extends Microsoft E5 capabilities to provide a unified identity security solution:
CyberArk addresses the following use-cases:
- Extending to On-Premises & Multi-Cloud: CyberArk elevates endpoint privilege management to comprehensive endpoint identity security for Windows workstations and servers, Linux workstations and servers and Mac workstations. CyberArk Privileged Access Management (PAM) supports Entra ID and broader identity providers and extends to on-premises databases and applications, as well as cloud services and infrastructure hosted across Microsoft Azure, Amazon Web Services and Google Cloud Platform.
- Security Before and After the Login: CyberArk uniquely helps secure cloud access with session protection and recording, AI-powered threat detection and prevention for key credential and cookie-based threats – all while supporting native user experiences.
- Machine Identity Security & Management: 68% of security professionals agree that machine identities are the leading cause of identity growth and up to 50% of them have access to sensitive enterprise data . CyberArk integrates with Azure Key Vault and leading Cloud Service Providers (CSPs) to discover cloud vaults and automatically rotate secrets, all without altering the developer experience. Security teams can centralize and standardize policies for secrets across any cloud, DevOps tool or even on-premises environments. This can be combined with automated certificate lifecycle management* and workload identity security and governance for robust machine identity security.
Azure PIM Use-Case
Microsoft E5 offers a foundation for identity management within Microsoft environments with Azure PIM.
- Azure PIM enables just-in-time and just-enough access to Azure resources. This is helpful, but not yet comprehensive, as support is currently for Entra ID.
Benefits of CyberArk for Enterprises with Microsoft E5
1. Intelligent Privilege Controls for Every Identity
CyberArk is laser focused on delivering identity security across your enterprise. This means providing the right level of privilege controls to every user in your environment.
CyberArk Identity Security Platform |
||||
| Identity | Workforce | IT Admin | Developer | Machine |
|
System Support & Integrations |
|
|
|
|
|
Use-Cases |
|
|
|
|
|
Unique to CyberArk |
|
|
|
|
|
Guidance to Leaders |
Protect user identities and endpoints with Endpoint Identity Security. Complement Endpoint Detection & Response (EDR) solutions while driving IT & Sec Ops efficiency. Protect and audit high-risk access with a Secure Browser. | Implementing privileged access management across crown jewel targets prevents damaging breaches. Drive a unified strategy that includes modern technologies for multi-cloud environments. | Protect developer and DevOps workflows, without disrupting native workflows and productivity. Secure JIT (Just in time) & ZSP (Zero Standing Privileges) with CSP, transparent secrets management, privileged access and machine identity management. | |
2. Efficiency & Cost-Savings for Service Desk & Security Operations
CyberArk provides several ease-of-use and cost-saving benefits:
- Cyber Insurance: Reduce premiums by reporting on how the organization is protecting critical assets and high-risk access.
- Service Desk: CyberArk Endpoint Privilege Manager (EPM) lowers ticket volume, as users have smooth, privilege escalation step-ups on endpoints. With CyberArk PAM, secure, time-limited access to any critical target, supported by session recording and centralized audit trails.
- Security Operations: Protect against post-authentication threats such as credential and cookie theft. CyberArk EPM sits alongside Microsoft Defender and 3rd party EDR. CyberArk reduces the number of total alerts sent to SecOps, serves as an effective last-line defense vs unknown ransomware and integrates with Azure Sentinel.
3. CyberArk Blueprint, Red Team and Remediation Services
Driving a robust security strategy while making a positive impact – is never easy. With over 8,800 customers, CyberArk distills key learnings in our Blueprint best practices framework that can help you balance enterprise security and operational efficiency.
With CyberArk Red Team, Remediation Services and partner network, you can proactively spar with your team, meet heavy regulatory requirements and strengthen your overall security posture.
CyberArk extends and amplifies your Microsoft E5 investment, allowing you to protect your data and users no matter where they reside. If you would like to discuss the right identity security strategy for your environment, contact us, view our CyberArk Blueprint resources, or start with the latest Gartner Magic Quadrant for Privileged Access Management.
*CyberArk signs definitive agreement to acquire Venafi: https://www.cyberark.com/press/cyberark-signs-definitive-agreement-to-acquire-machine-identity-management-leader-venafi-from-thoma-bravo/
Eric Sun is responsible for competitive programs at CyberArk.























