
Robotic Process Automation (RPA) is a powerful, emerging technology and a hot topic of conversation. Despite the buzz, many people remain fuzzy on understanding the specifics. Does RPA mean that organizations will soon employ armies of futuristic robots to do the work that humans once did (remember the movie I, Robot)?
Not quite. Let’s start with a definition. RPA is “the use of software with artificial intelligence and machine learning capabilities to handle high-volume tasks that previously required a human to perform.” In other words, RPA uses “software robots” to automate much of the manual “hand work” involved in daily business, such as entering data (invoices, POs, etc.) from one application into another. What RPA does NOT focus on is the “head work,” or cognitive automation, required to extract information from unstructured sources. This is the work—and irreplaceable value—of humans in the organization. RPA is not meant to replace employees, but rather, allow them to leverage their experience and capabilities and focus their efforts on business-critical work. RPA simply fills in the gaps—providing 24×7, cross-geography support for time-consuming, repetitive tasks.
Here’s how a typical task could be automated by a “software robot:”
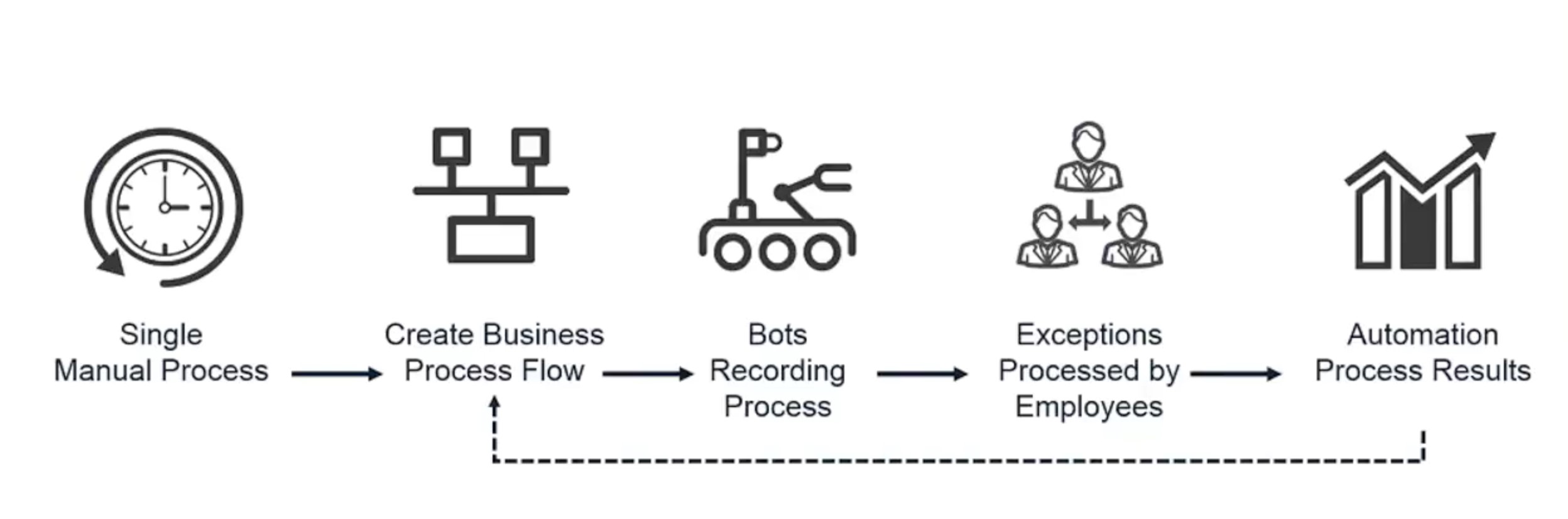
First, a single manual process is used to create a business process flow. The robots would then record that process. From there, any necessary rules, policies or exceptions to that process are identified and assigned to humans to manage. The robotic process is put into production and repeated over and over again. Throughout this loop, corrective actions are made to continuously refine the process and maximize operational efficiency, productivity and cost-savings.
RPA and Privilege Connection
So what do IT security professionals need to know about RPA platforms and the connection to privileged credentials? Simply put, it is a new attack vector and organizations need to protect the powerful, privileged accounts within these RPA platforms.
Because RPA software interacts directly with business applications and mimics the way applications use and mirror human credentials and entitlements, this can introduce significant risks when the software robots automate and perform routine business processes across multiple systems.
To minimize these risks, securing robotic credentials is paramount. In order to automate processes within an environment, software robots need “power access” (or privileged access) to carry out their mission—whether it be logging into a system(s) to access data or moving a process from step A to step B. This results in a large amount of credentials being stored in the application. An attacker that gains access to the RPA password storage location and cracks the proverbial “password piñata,” can then take the credentials, and ultimately, take control of the robots. Just like any other compromised commercial off-the-shelf (COTS) application, attackers can leverage these powerful credentials to do their bidding—but with RPA, it’s at an even greater scale. Most organizations employ multiple—sometimes hundreds or even thousands of—software robots, which access multiple systems and perform multiple processes simultaneously. With this in mind, you can appreciate the magnitude of risk to the enterprise.
Locking Down RPA Credentials
CyberArk solves the privileged access security challenge for both human and application users. Through the C3 Alliance, we’ve partnered with some of the world’s leading RPA players, including Automation Anywhere, BluePrism, WorkFusion and UiPath, to provide a simple, easy-to-deploy and cost-effective solution to this growing security challenge. This best-in-breed credential management solution:
- Implements and manages a unique account for every target system that needs to be accessed by a robot: This eliminates the need to put a powerful credential, such as a domain credential, into the application’s server for the robots to leverage. Additionally, if a system is breached, the breach will only affect that particular system—there will not be a larger, ripple effect across multiple systems.
- Securely stores and retrieves credentials: Instead of storing credentials within the application, robots can request credentials from CyberArk’s centralized, encrypted vault, as needed, via CyberArk Application Identity Manager, to perform their necessary tasks.
Here’s an illustration of this in action:
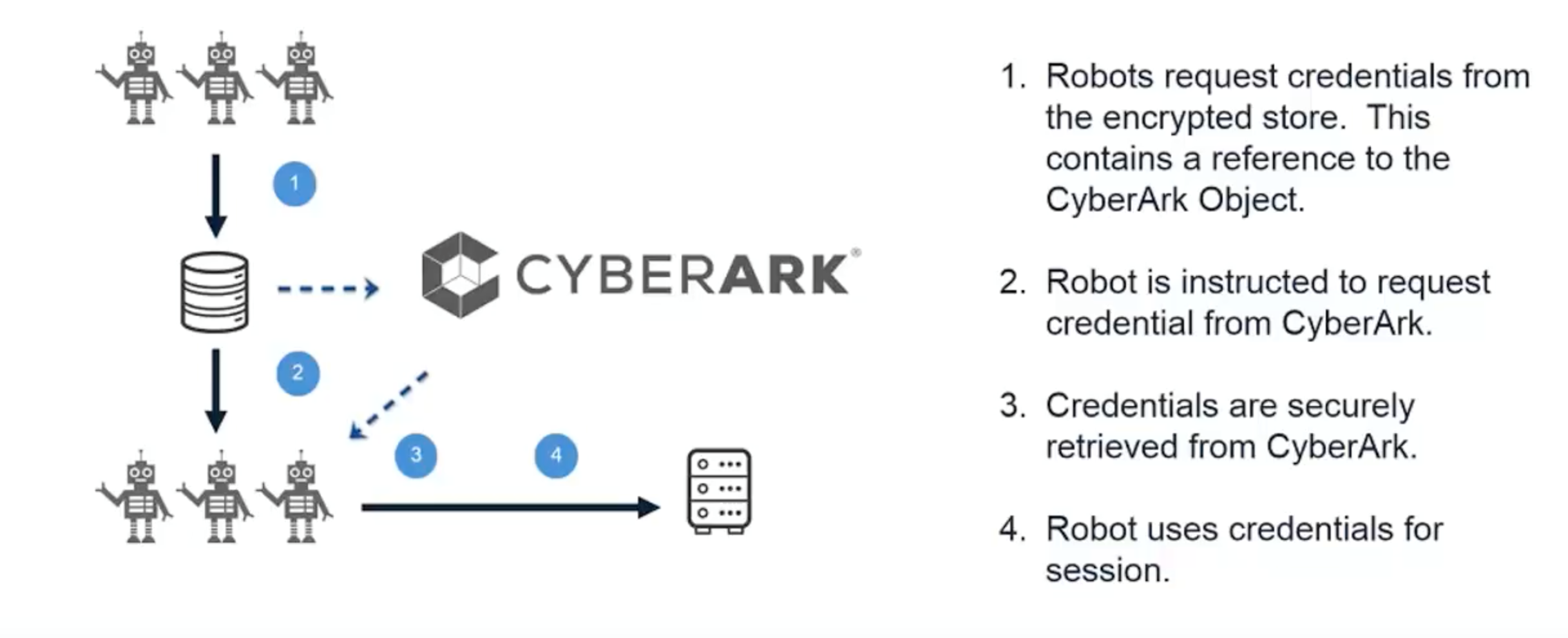
Interested in learning more about securing RPA with CyberArk? Watch a recent, on-demand webinar, which outlines what IT security professionals need to know about RPA platforms and the connection to privileged credentials. And for further reading, discover five RPA security best practices for privileged credentials and access, and download the “The CISO View: Protecting Privileged Access in Robotic Process Automation.”






















