
Ransomware attacks have a profound impact on healthcare organizations, extending well beyond financial losses and the disrupted sleep of staff and shareholders. A University of Minnesota School of Public Health study highlighted by The HIPAA Journal reveals that these attacks can lead to higher in-hospital mortality rates for patients admitted during the incidents.
Additionally, the study found that hospital volumes dropped by 17%-25% during the first week of an attack. Between 2016 and 2021, it is estimated that ransomware attacks resulted in the deaths of 42 to 67 Medicare patients.
In the IT world, we tend to think of healthcare providers as organizations handling the most sensitive information of millions of people. They swim in an ocean of rules and regulations – and their compliance is constantly scrutinized.
It’s easy to forget, at least until your next physical, that chasing compliance and protecting patients’ data are not the top priorities of healthcare providers. These organizations often hold something much more precious than our records: they care for our health. Simply put – they keep us alive.

How is it then that these organizations, the ones we turn to in the darkest moments of our lives, the praised first responders when global pandemics hit, are featured in cybersecurity news seemingly every other day? And usually not with a success story.
Why is this the case, and are we doing something wrong about how we look at healthcare cybersecurity?
Healthcare Cyber Breaches: A Growing Concern
Attackers today deliberately target those who are more likely to pay. It’s not a coincidence that healthcare is frequently hit; it’s a calculated decision. The combination of factors that make healthcare more likely to pay attracts cyber criminals, motivated by the potential for higher financial gain.
Healthcare is a prime target for ransomware attacks due to several factors: the risk to patient safety, access to highly sensitive data, disruption of operations, potential regulatory consequences – and the inherent nature of ransomware. These elements make healthcare providers more inclined to negotiate with attackers and, consequently, more likely to pay the ransom.
According to new research by Barracuda Networks, over a fifth (21%) of ransomware attacks targeted healthcare in the past 12 months, up from 18% in the previous year. Change Healthcare, Ascension and MediSecure are just some recent examples of ransomware attacks against healthcare organizations. One thing to note is that in many cases lately, the data is never even encrypted and only exfiltrated. In other instances, the data is exfiltrated first and then encrypted.
It’s Time to Revisit Our Approach to Healthcare Cybersecurity
I remember driving to work about 10 years ago and listening to a radio interview with the head of a hospital that had just made rare headlines for being hit by ransomware. The hospital head spoke about how he could not justify substantial (read: adequate) investment in cybersecurity because, unlike a new CT scanner, cybersecurity doesn’t affect patient outcomes. Well, this didn’t age well. I don’t think there are any doubts in the healthcare industry that cybersecurity is crucial, as the industry is clearly in the crosshairs.
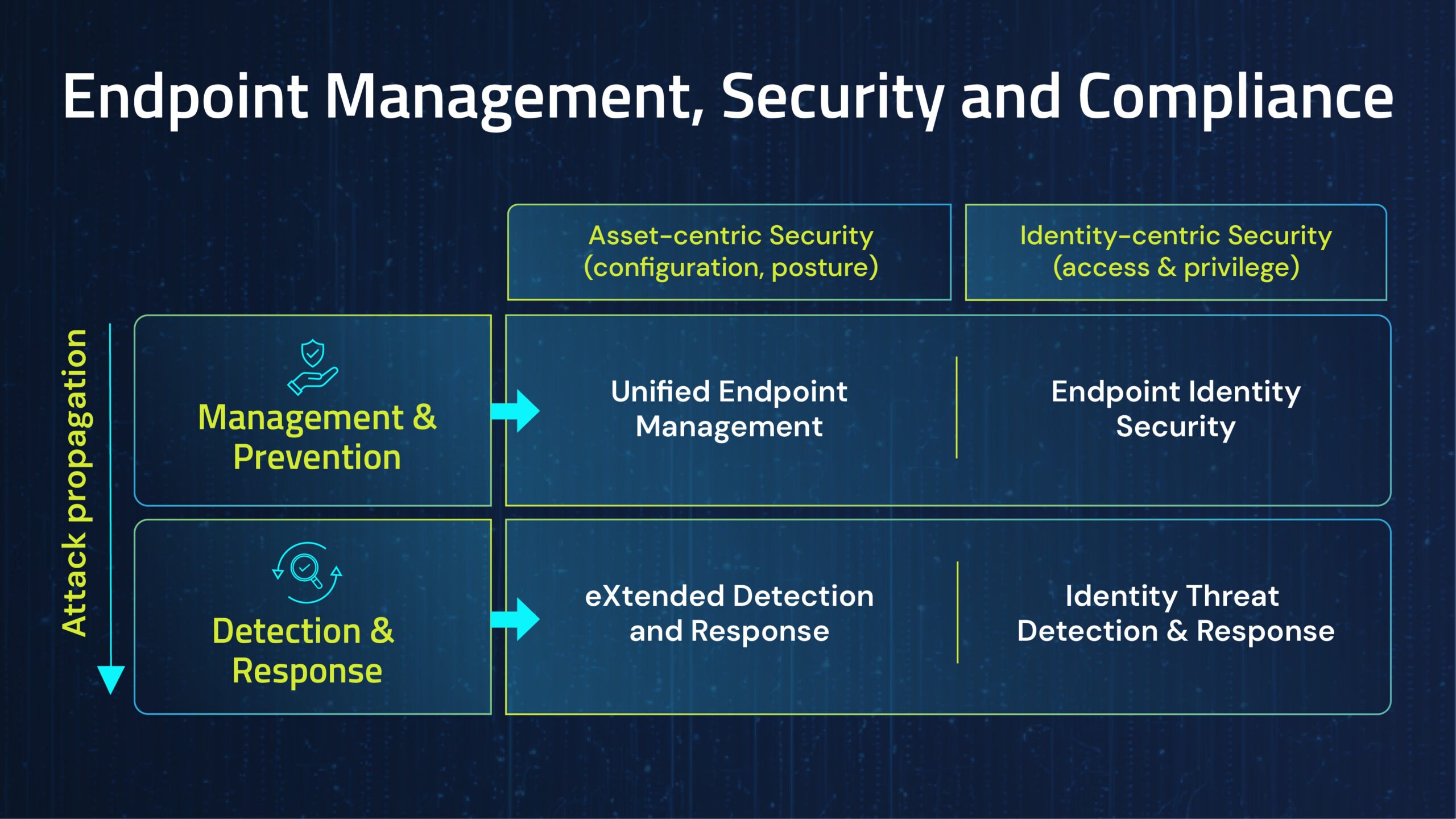
We need to collectively look at how we approach the security of healthcare IT infrastructures and workforce security. Today, endpoint detection and response (EDR) solutions are a default protection standard that helps check many regulatory standard checkboxes. But “compliant” has never been a synonym for “secure.” EDR solutions have specific goals and a specific threat model as a base of their design. And there’s no question that leading EDRs are very effective within their self-defined scope of responsibility. In fact, most IT security professionals I spoke with can reliably reproduce an EDR vendor’s pitch.
As is often the case, the devil is in the details. Credentials are stolen and sold on the black market, users run as admins, legitimate tools are used to steal cookies and hijack the web sessions, weak multi-factor authentication (MFA) is used at best and servers sit unprotected because their attack surface is small.
George Kurtz, CEO of CrowdStrike, perhaps said it best answering a senator’s question during congressional hearings in 2021 on the SolarWinds breach about why EDR didn’t sound the alarm and how it got disabled: “… once you have admin access on a particular system if you are shutting it down, you can do pretty much whatever you want on it.”
This answer lets us peek behind the curtain just enough to understand that EDR is not the panacea we once believed it to be. Over the years, we have learned to rely on EDR for security, but it has become the single point of failure.
EDRs Lack Foundational Controls
Let’s consider just a few inherent EDR shortcomings that stem from EDR’s focus, threat model and operational model:
- EDR is not user-aware. It does not have a way of authenticating the user and relies on the operating system. Whoever has got the password is the right kind of user for EDR.
- EDR does not differentiate between an administrator and a regular user. There are several published techniques of tampering with EDR without tripping the wire using elevated access, such as removing EDR hooks.
- EDR focuses on malicious files and behaviors. A “legitimate” user leveraging legitimate tools will likely never draw attention.
- Credential theft from the operating system, third-party software and browser credential stores is protected, at best, from a malware perspective (e.g., blocking infostealers), while access to LSASS dumps, NTLM hashes, PuTTY files, cookies and web session data is not universally blocked.
- Users typing passwords is business as usual for EDR. Keyloggers will likely be found and terminated, but more sophisticated attacks, including phishing, would leak passwords.
- Ransomware attacks don’t give second chances. There’s no acceptable “Response” in a ransomware incident.
- Ransomware attacks get second chances. If the attacker successfully bypassed EDR once, without proper infrastructure and system hardening, they can return for a second ransom payment. While EDR can help determine how attackers gained access and what tools they used, it cannot provide adequate remediation without an update from the vendor. To help ensure attackers are shut out of environments, implement system hardening, least privilege and user authentication.
- Many out-of-the-box (OOTB) detections in EDR systems, which perform well in demo or lab settings, often need to be disabled or excluded in a production environment due to false positives caused by in-house developed applications and accepted user behaviors that can be difficult to differentiate from an attacker’s tactics. The variation in these factors from one organization to another results in widely differing levels of protection.
- Comprehensive 360-degree identity security, application control and isolation, strong continuous MFA, credential theft protection, role-based least privilege, local administrator account security and other critical foundational endpoint security technologies are not part of EDR solutions.
Preventing Cyberattacks: The Ultimate Defense Strategy
Many healthcare organizations today lack the preventative, identity-centric component in their endpoint security strategy, which is crucial for preventing identity-based attacks on endpoints. This component is endpoint identity security. By adding endpoint identity security to their endpoint security stacks, healthcare organizations can unprivilege the attacker, reduce the endpoint’s attack surface, prevent administrator and regular user credential compromise and enable an end-to-end passwordless user experience on endpoints. This experience spans from the moment the user attempts to sign in to their machine, through strong MFA for risky desktop applications, to secure browsing and web session experiences. If we keep relying on EDR to solve all of our security problems, we’ll keep seeing “successful,” “suffered from” and “reported” attacks.
Healthcare Cannot Afford to Put All Its Eggs in an EDR Basket
A defense-in-depth cybersecurity approach necessitates that while EDR is a valuable tool in the fight against cyber threats, it should never be the only line of defense. Given a cyberattack’s high stakes and potential consequences, healthcare providers cannot afford to rely solely on EDR. The industry must adopt a holistic security strategy that includes endpoint identity security as a foundational control. By doing so, they can better protect their networks, safeguard patient data and ensure the continuity of critical services.
For a deeper dive into this subject, check out our eBook, “Why EDR Isn’t Enough to Stop Cyberattacks.”
Andrey Pozhogin is a director of product marketing at CyberArk.





















