
In December, I’ll have been with CyberArk for seven years, and at a similar point, I’ll have spent two years leading product marketing for cloud security at the company. In my short tenure with CyberArk Product Marketing, I’ve advocated for zero standing privileges (ZSP) as a default mechanism for implementing privilege controls. It’s easier, more effective and doesn’t change how people work.
There’s reason behind my zealotry – I’ve seen customer appetite grow for native, scalable identity security controls every year. ZSP is the easiest way to meet this shift head-on.
However, I’ve never shared my view of why it’s essential: ZSP has a clear goal and end state, clearly worded in the name itself: Zero. Standing. Privileges. No one has any entitlements until they are requested and approved. Zero. Zilch.

I often get asked to expand on the ZSP concept and how to implement it. So, I’ve prepared this blog to explain its details in as much depth as possible.
Let’s examine the most common questions about ZSP to understand better its importance and how it can be implemented in your security strategy.
What’s Zero Standing Privileges?
ZSP is a security principle that advocates removing all persistent user privileges within an enterprise’s estate. In short, access is provisioned just-in-time (JIT) with ZSP, meaning every identity not in use has no entitlements until required by a user and authorized by a policy or automation.
Why Should I Use ZSP?
Implementing ZSP goes beyond the foundational privileged access management (PAM) mantra of ‘vault, isolate, and rotate’ by offering an additional layer of risk reduction. Unlike conventional methods, ZSP operates outside the known accounts of the PAM platform, controlling access through permissions and entitlements rather than account ownership. While ZSP may not be applicable in all scenarios, such as with tenant-level accounts during SaaS tenant creation, its use can significantly enhance your security posture.
What’s Wrong with Just-In-Time Controls?
JIT controls are a valuable part of any security strategy when they meet your needs effectively. However, as our Field CTO Brandon Traffanstedt highlighted in a recent webinar, the landscape of JIT controls is diverse, with each variant requiring different levels of effort to implement and offering varying degrees of risk reduction. This is where ZSP comes into play, providing a more nuanced approach to privilege management that aligns with the dynamic nature of today’s security demands.
Isn’t ZSP Just JIT With Extra Steps?
ZSP indeed shares common ground with JIT controls, as they both embody the principle of granting access only when needed. However, ZSP refines this concept by incorporating Time, Entitlements and Approval-based controls (TEA), which provide a more granular management of user sessions. This approach not only simplifies benchmarking when standing entitlements are present but also ensures that you’re not solely reliant on JIT controls, thus moving closer to a 100% adoption of robust security practices.
When Should I Use ZSP-based Controls?
Embracing zero standing privileges whenever possible can significantly enhance your security framework. By adopting ZSP-based controls, you not only streamline the user experience but also expand the reach and effectiveness of your PAM program. This proactive approach can lead to faster adoption rates as it integrates seamlessly with existing workflows, allowing users to perform their tasks without the need to master new procedures.
The visual below, from a recent CyberArk webinar, focused on zero standing privileges and how it fits in with other privilege controls, nicely sums up how to balance your privilege controls:
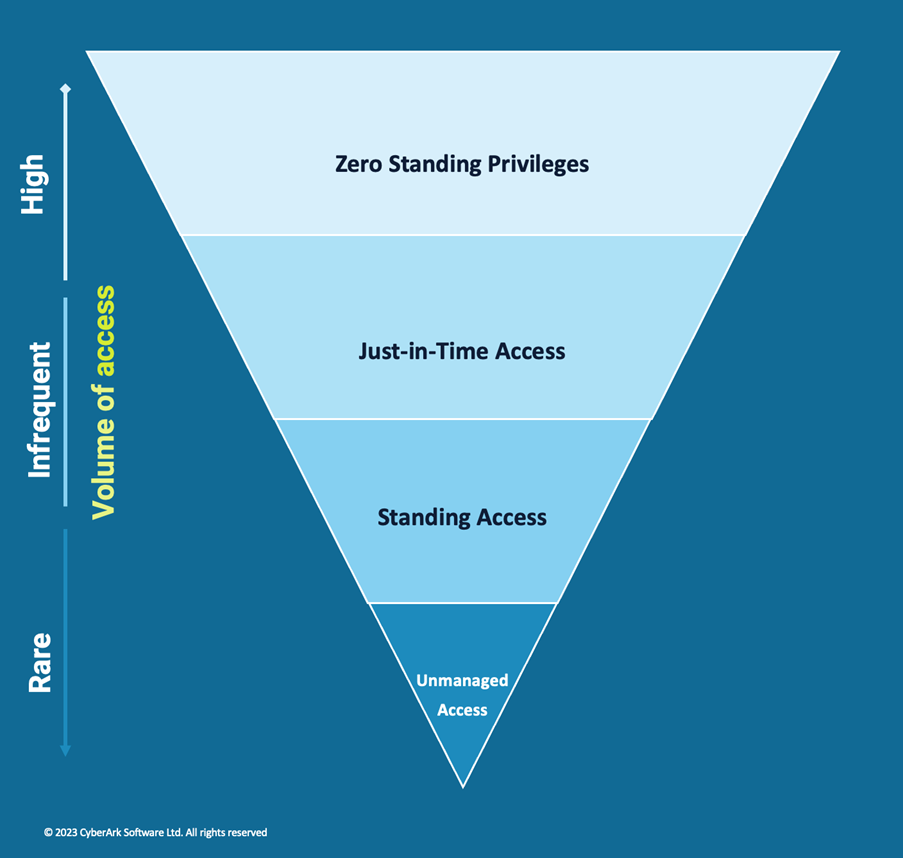
If I Can Use ZSP, What Should I Do?
Implementing ZSP should be a proactive step in enhancing your security measures. Rather than remaining inactive, explore alternative means to implement controls, such as JIT controls, if they are more suitable. If not, consider vaulting as a secure option. The key is to take action and utilize the most effective control mechanisms available.
If I’m Buying a New Solution, is ZSP Enough?
While ZSP is a significant step forward in privilege control, they are not a standalone solution. Recognizing that ZSP controls may not fulfill all your requirements is crucial. Therefore, when selecting a new solution, ensure it encompasses a full spectrum of controls, including vaulting, JIT and ZSP. This diverse range of controls can equip you to tackle every required privilege control.
Embracing the Future with Zero Standing Privileges
Are you starting to feel like I do about the benefits of zero standing privileges? I hope you are (and my ZSP zealotry is rubbing off on you)! Thoughtful application of ZSP controls will help elevate your PAM programs and drive adoption at a rapid pace. I encourage you to embrace this innovative approach with me and transform your security strategies for the better.
Josh Kirkwood is a senior product marketing manager at CyberArk.





















