2023 was a lucrative year for ransomware actors, with victim organizations paying $449.1 million in the first six months alone. Maintaining this cash stream requires frequent technique shifts, which may be why more attackers are exploiting legitimate software to propagate their malware.
Abusing organizations’ existing enterprise tools can help attackers blend in while they’re doing reconnaissance, and also aids them with privilege escalation and persistence. Coupling this technique with ransomware as a service (RaaS) also lowers the bar to entry by eliminating the need for attackers to create malware – something that requires skills, resources and time. This means more adversaries can get in the game and do more damage.
Enterprise software isn’t the only target. Ransomware actors have also been known to exploit vulnerabilities found in open-source software (OSS), inject their own payloads into OSS and use OSS in lieu of custom-crafted malware. According to a recent advisory from the U.S. The Cybersecurity and Infrastructure Security Agency (CISA), the notorious Lockbit operation has been observed using legal freeware for a host of nefarious purposes, including network reconnaissance, remote access and tunneling, credential dumping and file exfiltration.
When attackers exploit legitimate tools, traditional endpoint security solutions are unlikely to catch them unless behavior analytics capabilities are in place to flag unusual logins, privilege escalation, program execution or other risky activities.
Tracking Legitimate Software Abuse Across the Attack Chain
Ransomware actors increasingly use legitimate software to their advantage at various stages of the attack lifecycle. They employ many different tactics, techniques and procedures (TTP) to advance their missions, including the examples highlighted below.
Initial infection. It’s choose-your-own adventure when it comes to gaining initial access. Some attackers use exploits such as employing common vulnerability exploitations (CVEs) against vulnerable targets. They also steal, forge, alter or manipulate cookies from users’ web sessions to get in. Or, they send phishing emails and trick users into downloading legitimate applications. For instance, in January 2023 CISA warned of a widespread campaign involving remote monitoring and management (RMM) software that, once downloaded, could be used as part of a refund scam to steal money from victims’ bank accounts.
Persistence. Attackers also use legitimate software to establish backdoors for persistence and/or command and control (C2). Along the way, they may use them to bypass MFA and/or modify or disable existing security tools to avoid detection, from terminating endpoint detection and response (EDR)- protected processes to modifying/deleting registry keys or configuration files. In the RMM ransomware attacks described above, threat actors used the software’s portable executables to gain access without the need for local admin privileges or full software installation. This allowed them to “effectively bypass common software controls and risk management assumptions,” according to CISA.
Many software programs run by default on a machine. By hijacking these programs, attackers can guarantee that their malicious programs will run too. They can also abuse application features such as task schedulers (that launch programs or scripts at pre-defined times or after specified time intervals) to maintain persistence. Even legitimate tools built into the operating system, such as living off the land binaries (LOLbins), can be maliciously abused to cover attackers’ tracks, gain persistence or escalate privileges.
Privilege Escalation. Windows operating systems are protected by User Account Control (UAC), a native security feature designed to protect against malicious software and unauthorized changes. If regular business users try to run a program as an administrator, UAC will prompt them to enter the credentials of an admin user before changes can be made. Though most ransomware on the market today doesn’t require admin rights to encrypt data, attackers often target and bypass UAC to elevate access and establish persistence.
Lateral Movement. Many tools can inadvertently facilitate malicious privilege escalation and lateral movement. AdFind, a free command-line query tool used to search Active Directory (AD), is a popular choice. Another is AdvancedRun, which allows software to be run with different settings and enables privilege escalation by changing settings before running software.
What’s more, numerous Windows features built for managing machines are also remote procedural call (RPC) servers. This means that they can receive remote commands from other machines on the network to run programs. Many RPCs expose functions to end users while enabling communication between client and server programs, opening the door for attackers who can abuse them to move laterally.
Encryption. Encryption can be used both as a tool and a weapon. Encryption tools are critical for hiding data from unauthorized users. These same tools can also be used as ransomware. Or attackers can compromise users with legitimate access to encrypted data to bypass encryption controls altogether.
This summer, the U.S. Department of Health and Human Services (HSS) alerted healthcare organizations of a ransomware attack on a medical facility that “significantly reduced patient treatment capability, rendered digital services unavailable and also threatened exposure of patient personal health information (PHI) and personal identifiable information (PII).” TimisoaraHackerTeam – the ransomware-as-a-service (RaaS) group behind the attack – is described as “unique among attackers” due to its characteristic tactic of abusing legitimate encryption tools including Microsoft BitLocker and Jetico BestCrypt to live off the land and eventually encrypt data.
Data Exfiltration. Somewhat surprisingly, ransomware operators that employ double-extortion techniques rarely create their own tools to steal the data used for their leak sites. Rather, they’ll often use legitimate backup tools or similar programs to exfiltrate their victims’ data. Earlier this year, CyberArk Labs observed threat actors using Discord, a popular collaboration app, to exfiltrate data via webhooks. Rclone, a command line program for syncing files with cloud storage, is another appealing option as it allows attackers to easily move files via transfer protocols such as FTP and SFTP. Attackers also employ tools like 7-zip, an open source file archiver, to compress data, which helps them avoid detection before exfiltration.
While most of the above examples focus on Windows, ransomware actors are also modifying their tools to attack across platforms and operating systems. For instance, some employ the cross-platform programming language Rust to target Linux. macOS isn’t immune either. One popular method to infect macOS and iOS devices is exploiting Find My iPhone, an Apple feature that helps users lock their devices if they get lost. If an attacker successfully steals or purchases a user’s Apple ID and password and logs into the device, they can enable the remote device lock via the Find My iPhone app, hold data hostage and display a ransom note on the screen.
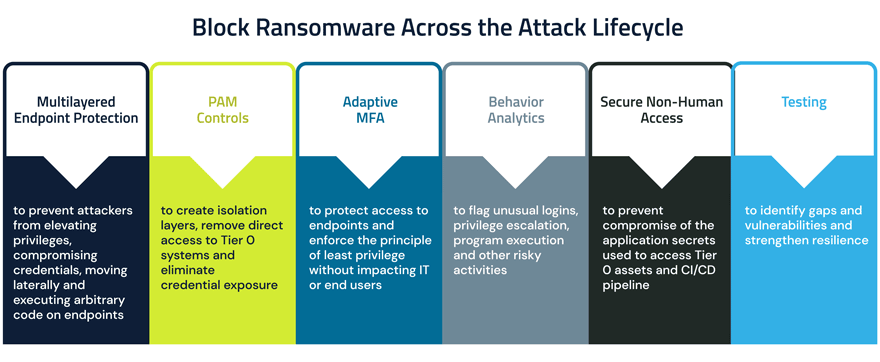
Block Ransomware Across the Attack Lifecycle
Attackers’ shift to legitimate software is concerning given the highly stealthy nature of these attacks. But fortunately, organizations that take an identity-centric defense-in-depth approach to ransomware protection can largely stay the course. Fundamental endpoint security controls remain the same, including endpoint detection and response (EDR), anti-virus (AV)/next-generation antivirus (NGAV), content disarm and reconstruction (CDR) email security and patching. But most important of all is application control. It doesn’t matter if it’s RaaS, polymorphic malware or some other malicious ransomware variety, if it can’t execute, it can’t deploy ransomware.
This trend underscores the fact that endpoints play a leading – but not singular – role in ransomware attacks. This is becoming increasingly clear as more adversaries embrace this method. When attackers hijack legitimate tools to gain a foothold, least privilege and behavioral analytics capabilities become even more critical for quickly detecting and blocking cloaked threats as they attempt to move through the network, bypass or disarm security systems and reach high-value targets.
CISA offers a list of in-depth mitigations recommendations for organizations looking for ways to improve their cybersecurity posture to better defend against ransomware attacks utilizing legitimate software programs. This defense-in-depth perspective on ransomware also outlines best practices for shoring up vulnerabilities to mitigate risk. And CyberArk Labs offers extensive research insights on ransomware families, commonalities, the path to encryption and mitigation strategies.
Andy Thompson is CyberArk Labs’ Offensive Security Research Evangelist.























