Zero Trust.
You’ve heard about it. A lot. But there are quite a few nuances when it comes to how Zero Trust security is defined and discussed. Is it a platform or a principle? It’s one of those terms that’s so widely cited that it has the tendency these days to elicit eye rolls within the cybersecurity industry and to be referred to as a buzzword by those sitting at the cool kids’ lunch table.
At its core, though, Zero Trust is a strategic cybersecurity model enabled to protect modern digital business environments, which increasingly include public and private clouds, SaaS applications, DevOps and robotic process automation (RPA). It’s a critical framework, and every organization should adopt it and understand the fundamentals of how it works. Identity-based Zero Trust solutions like single sign-on (SSO) and multi-factor authentication (MFA) are designed to ensure that only authorized individuals, devices and applications can access an organization's systems and data.
Stated simply, Zero Trust works on the holistic approach that you can’t separate the “good guys” from the “bad guys.” Traditional approaches that focused on establishing a strong perimeter to keep the bad guys out no longer work. In today’s world, the rapid pace of digital transformation, increased use of cloud services and adoption of hybrid work has created a continually shifting enterprise environment that’s chaotic and difficult to secure. This resulted in the “never trust, always verify” Zero Trust approach to secure identities, endpoints, applications, data, infrastructure and networks, while providing visibility, automation and orchestration.
With Zero Trust, no actor can be trusted until they’re verified. Nobody. No one. Zero exceptions. It’s a holistic, strategic framework for security that ensures everyone – and every device – granted access is who and what they say they are.
So, Why Zero Trust?
Today, cybersecurity incidents ranging from ransomware and phishing to denial-of-service attacks dominate the news. An increase in cloud applications, mobile devices, remote workers and IoT-connected devices has forced organizations to align their security policies based on business intent. Embracing Zero Trust means adopting technologies, ways of working and policies that support business agility while enhancing security. Consider these findings:
- Ransomware breaches rose 13% from 2021, representing an increase greater than the past five years combined.
- Seventy-one percent of organizations suffered a successful software supply chain-related attack in the past year, resulting in data loss or asset compromise.
- Meanwhile, the average cost of a data breach hit an all-time high of $4.35 million in 2022.
So, before an organization can take advantage of Zero Trust, it must create a set of identities for its employees, their devices and the applications they use. Most importantly, it is essential that all these capabilities are integrated and work together so they can be applied in real time without adding delays to access decisions for APIs or for users who are logging onto applications.
From Novel Cybersecurity Concept to De Facto Approach
The phrases “Zero Trust” and “Zero Trust architecture” were coined by industry analyst John Kindervag in 2010, who recognized the futility of perimeter-based security. Though the philosophy upended conventional thinking about infrastructure, network and data security, it began to take hold as identity-based threats surged. Fast-forwarding to the present day, Zero Trust is the de facto cybersecurity approach – the digital modernization measuring stick championed by government and industry leaders alike. Why? Because identity is more important than ever.
- Identities are everywhere: The average staff member now has 30 identities and machine identities outnumber these human identities 45:1.
- Identity is the easy way in: 52% of organizations don’t protect identities linked to business-critical applications, and nearly half lack Identity Security controls around cloud infrastructure and workloads. Meanwhile, 87% report that secrets are stored in multiple places across DevOps environments.
- Identity worries keep teams up at night: Security leaders say credential threat is their number one area of risk. As more assets move to the cloud, hybrid work becomes the “forever” model, digital transformation continues and third-party access needs expand, attackers are targeting identities that aren’t often secured and properly managed.
With this as a backdrop, it’s no surprise that 88% of senior security executives say adopting more of a Zero Trust approach is “very important” or “important.” And many are taking action. According to Enterprise Strategy Group’s (ESG) research report “The Holistic Identity Security Maturity Model,” more than half of global organizations surveyed have implemented or have started to implement a well-defined Zero Trust strategy across their IT real estate to enable Zero Trust.
The Five Principles of Any Zero Trust Implementation
Many frameworks exist to help organizations move toward Zero Trust, such as CISA’s Zero Trust Maturity Model and NIST’s SP 800-207 Zero Trust Architecture. Since every company is different, these frameworks are designed to guide – not prescribe – Zero Trust strategy and roadmap development, along with implementation and compliance. While this leaves room for flexibility, every effective Zero Trust program should share five constants:
- Strong, adaptive authentication. Adding an adaptive form of MFA with intelligent risk-based access strengthens password security and provides important user behavior analytics for everyone’s benefit. Organizations can spot potential threats faster, and users can simply and securely access resources.
- Continuous approval and authorization. Reauthenticating and revalidating user identities (after high-risk web browser sessions or periods of inactivity, for example) help ensure the right user has access to the right resources.
- Secure, least privilege access. Intelligently granting access to individual enterprise resources – from the endpoint to the cloud – requires advanced privileged access management (PAM) controls. The most effective approaches enable dynamic provisioning, such as granting just-in-time (JIT) privileged access on a per-session basis to reduce standing privileged access risks.
- Continuously monitor and attest. Just as privilege is not binary, neither are access decisions. Continuously monitoring is the best way to understand what is happening and confirm it should be happening, while detecting anomalies as they arise and maintaining optimal system security.
- Credential and authentication protection. Endpoint privilege management is the cornerstone of strong endpoint protection, critical for detecting and blocking credential theft attempts (via software abuse or memory scraping), enforcing least privilege consistently (including local admin rights removal) and applying flexible application control (such as allow-listing for well-known sources) to defend against malware and ransomware.
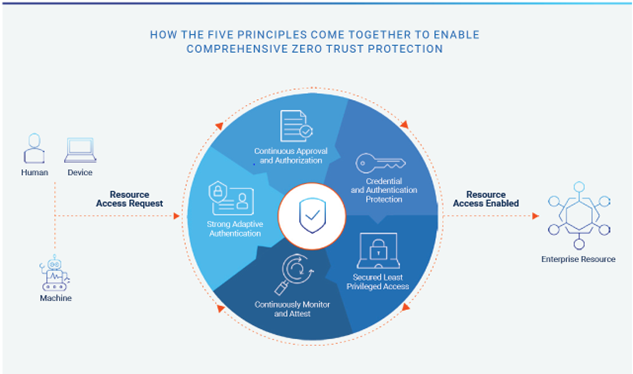
Five principles of Zero Trust strategic cybersecurity model
While definitions for these principles (or “tenants” or “pillars”) vary somewhat across frameworks, Identity Security is foundational to all of them. Apply these identity-based principles first to accelerate the journey, measurably reduce risk and improve business outcomes.
Identity Security as the Central Pillar of Zero Trust
By now, it should be clear that Zero Trust is not a single technology but an approach for denying access by default, verifying every identity, validating every device and intelligently limiting access to every resource. Identity Security offers a robust set of unified access controls to enable Zero Trust by:
- Enforcing least privilege and securing access for humans and machines across any device, anywhere.
- Introducing intelligent privilege controls — and infusing them across the board — to help isolate and stop attacks, protect critical assets and grant access for just the right amount of time.
- Automating management of the identity lifecycle through seamless, no-code app integrations and workflows, taking control of excessive permissions to enforce least privilege.
- Continually monitoring for threats so enterprises can adjust controls based on user behavior to identify when an identity has been compromised.
With Identity Security as the backbone of a Zero Trust approach, teams can focus on identifying, isolating and stopping threats from compromising identities and gaining privilege before they can do harm.
Putting Your Trust in Zero Trust
Zero Trust security is a journey, not a destination. It's an iterative process. As such, organizations need other security measures to complement mature and measurable Zero Trust programs. Most importantly, it’s not a one-time implementation but an ongoing process that requires continuous monitoring and improvement to boost your cybersecurity posture. For a deeper dive into Zero Trust, check out the CyberArk whitepaper “Zero Trust’s Evolution: The Role of Identity Security.”























