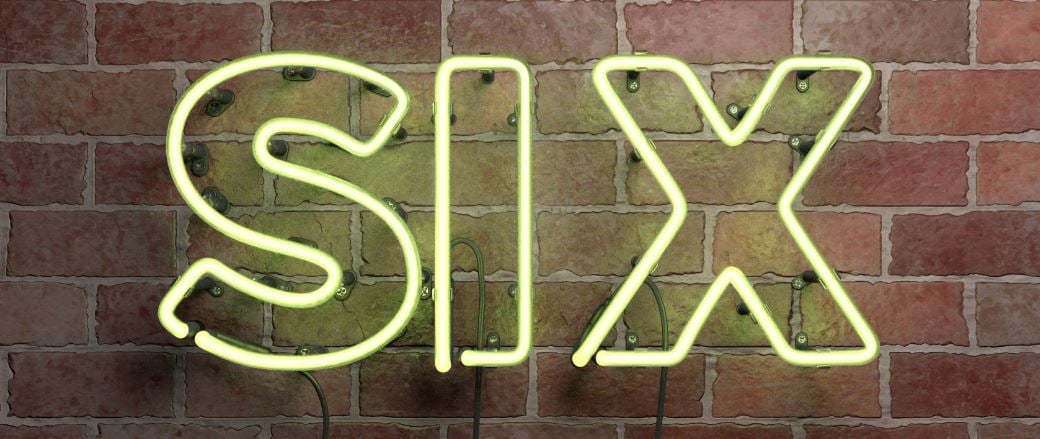
By now, most understand that privileged accounts play a leading role in the cyber attack lifecycle and also in advanced cyber attacks. Privileged accounts can access the most sensitive data in an organization, modify or completely disable security mechanisms, and stop, start, or modify the processes, systems, and apps that the business runs on.
Yet despite this knowledge, many organizations still share credentials directly with users, contractors, or third-party vendors. They also store passwords in spreadsheets, only rotate credentials (at best) every 30 days, and give users—and service accounts—full admin rights on desktops and servers.
In a recent CyberArk webinar, my colleague Kevin Naglich noted that attackers recognize and take advantage of these poor security practices and routinely employ six common techniques to steal privileged credentials:
- Keystroke logging: Capturing everything that a user types, including their privileged passwords.
- Password cracking: Attempting to guess or “crack” credentials with brute force. Industry reports have revealed network administrators, database administrators and system administrators (in other words, people who should know better) are often the worst offenders (and therefore key targets in an attack) when it comes to having easy-to-crack passwords.
- Memory scraping: Looking into the memory on desktops, searching for credentials that may be saved in plain text, or in Windows environments, searching for particular hashes that can be used in pass-the-hash
- Password spreadsheets: Locating spreadsheets containing passwords. (Yes, this is still a thing. If you have one, get rid of it today.)
- Social engineering: Tricking a user into giving up their credentials directly.
- Hard-coded application credentials: Passwords or SSH keys that are within application codes, scripts, or configuration files that enable far-reaching access but are often unchanged for years at a time.
These techniques enable attackers to bypass and short-circuit controls. Think of it this way: privileged account security is THE control that affects all other controls. Even if an organization spends significant time and resources building strong password complexity rules and policies, it may find that all it takes is one keystroke logger to cause everything to fall apart. Consider Verizon’s 2016 Data Breach Investigations Report, which notes, “Prominent malware families […] are designed to capture keystrokes from an infected device. All those efforts to get users to use special characters, upper/lower case numbers and minimum lengths are nullified by this ubiquitous malware functionality.”
Another illustration of the depths of this problem can be seen in Mandiant’s M-Trends Report, which notes that the company’s Red Team, on average “is able to obtain access to domain administrator credentials within three days of gaining initial access to an environment.” While layered security is certainly critical (including proactive controls such as encryption and detection systems to identify malicious behavior), these systems can be largely ineffective without privileged account security in place as a safeguard.
An investment in privilege is not simply addressing one niche area of security, it is raising the security posture of the entire organization. That’s why it’s important to prioritize privilege account security, and approach it with a program mindset. Successful deployments typically define a strategy that follows a risk-based roadmap, establish a maturity model that accumulates quick wins to build momentum, and lay the groundwork for automating as many tasks as possible.
Want to learn more? Watch a brief video about the three primary phases for successfully implementing the CyberArk Privileged Account Security Solution.























