
Fueled by automation, the adoption of DevOps processes and more, the role of the developer has become increasingly important and widespread for enterprises going through digital transformation. Developers need access to privileged credentials in order to access key developer tools like Kubernetes or Jenkins admin console. These credentials can be saved locally, making developers’ workstations — whether they are Macs or PCs — high-value targets for hackers.
These workstations are often vulnerable to something as simple as a phishing email, which attackers can use as an entry point to get access to the developer’s credentials. Because of these vulnerabilities, developers’ workstations are extremely important to secure. However, developers are famous for prizing speed above all else — and seeing security as little more than a speed bump. So how to ensure that developers take security seriously?
Securing privileged access through the principle of least privilege needs to be a top security priority. It is no secret that no-one should have full-time admin rights. But, what does that mean for developers?
Security teams face a difficult dilemma. They need to better secure developer workstations while still providing them the elevated permissions and privileges—and freedom—they need to get their job done. And they need to do all that without impacting velocity.
I recently encountered this comment on the Stackoverflow forum:
“There is almost no legitimate operational reason for restricting admin access to local PCs for staff that need it to do their job.”
Is that true?
Developers, DevOps and other engineers all perform administrative tasks as part of their job responsibilities, so they also have “full control” of their environment. Furthermore, because of the work developers do, there are extra challenges involved in hardening and restraining their workstations regardless of whether they are using Windows or macOS.
Developers install and uninstall software, drivers and system updates. They change operating system internals and use debugging programs on a regular basis. Without full control, developers often can’t do their jobs.
However, developers have access to source code, API keys and other shared secrets – usually more access than the standard user. Compromising a developer is a quick way for attackers to gain immediate elevated access to the most essential, mission-critical information an organization has. Consequently, developers have the kind of access that attackers want, which makes them the type of user who needs the highest levels of protection – whether they like it or not.
Want to take over a company or cause reputational damage quickly? Compromise a developer endpoint.
There are even specific types of attacks designed to target developers. For instance, “watering hole” attacks where cyber attackers will compromise common, popular developer web sites known to be good places to share code and get help troubleshooting programming issues. For example, four of the largest software developer companies in the world were compromised during a single cyber attack campaign that placed a zero-day Java exploit on an iOS developer web site.
Rights and Responsibilities
One way to deal with developers’ requests for full admin rights would be to provide them with virtual machines dedicated to programming, which could be perfectly patched and thoroughly hardened. This is doable with the right amount of monitoring and alerting, antimalware and IPS.
However, a workaround like this has a huge management overhead. It requires more budget, additional machines and another user to manage those machines. It’s not a comfortable situation for the IT team or the developer – and let’s not forget the cost of such a solution.
Additionally, while using their development tools, developers consume a lot of computer resources (e.g. generating millions of temporary files during code compilation). This leaves the security team with the job of ensuring that no significant performance impact occurs while implementing endpoint security products – not an easy task.
Conventional attempts to counter this typically require system administrators or security staff to perform manual inspections and craft security policies in response. As application complexity and development velocity increase, it becomes impractical to determine least privilege ahead of time manually. Furthermore, a central policy gatekeeper won’t scale efficiently and is likely to negatively impact delivery velocity.
Cutting the Gordian Knot
There has to be a better way to balance the needs of the developer with security concerns. Organizations need to be able to remove administrative privileges from developers without preventing them from doing their jobs, reducing velocity or overburdening security teams.
CyberArk Endpoint Privilege Manager can overcome these obstacles, allowing organizations to remove privileged credential rights on Windows workstations, servers and MacOS. It provides privileged access management (PAM), allowing enterprises to easily remove local Admin users – including developers. For instance, CyberArk Endpoint Privilege Manager can elevate specific applications used by the developer on a day-to-day basis or provide just-in-time user elevation for a specified time while recording and logging all user activity.
In addition, since developers may save credentials to their development environments, Endpoint Privilege Manager protects those repositories from credential theft while allowing trusted applications to use the credential stores.
Another key feature for the developers use-case is the out-of-the-box predefined policies for different developer tools like visual studio, Eclipse, Git and others.
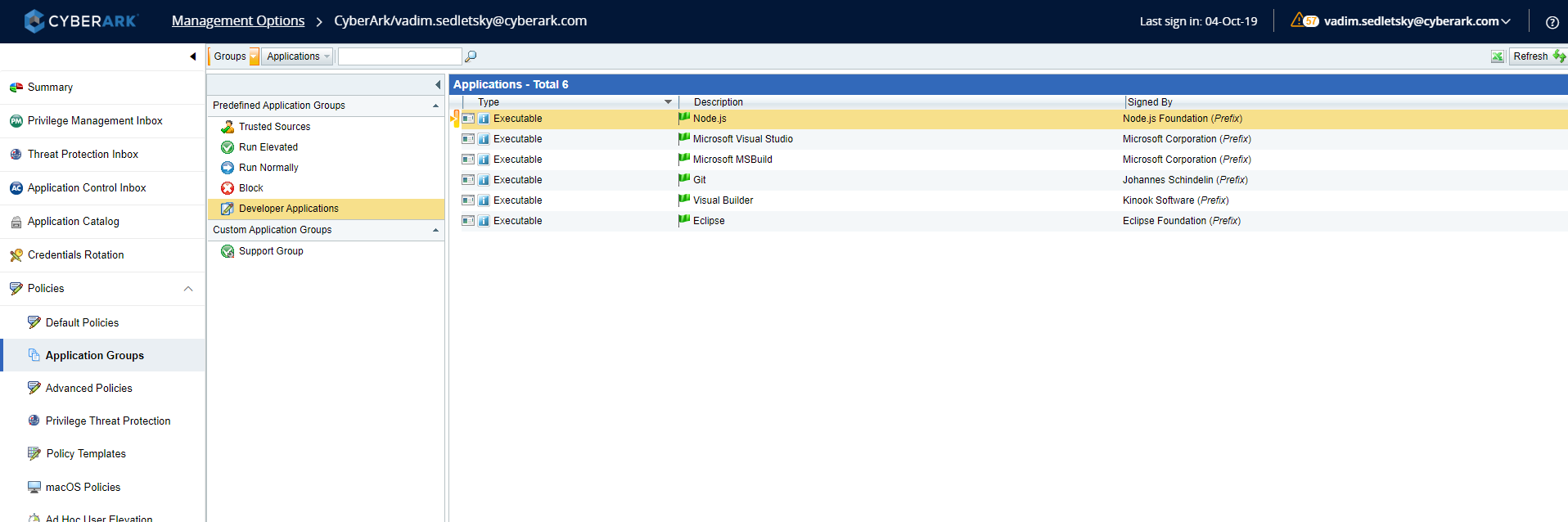
Final Thought – The Developer Resistance
Each new security-driven restriction impacts the developer productivity throughout the entire software development process. Consequently, developers may fight the rules and restrictions necessary to maintain a strong security posture. What makes Endpoint Privilege Manager any different?
Endpoint Privilege Manager minimizes interference in the developer workflow. Developers – and other users – don’t need to go through the extra step of involving an administrator when they need access to certain applications. For a predefined, approved set of applications, users can seamlessly gain access through an automated process.
Furthermore, Endpoint Privilege Manager allows users to elevate privileges to access these approved applications while continuing to access other, unapproved applications as non-privileged users. This means that developers can continue to access the majority of the applications they use on a daily basis without having to slow down – without losing out on the benefits of application security.
Developers are like builders constructing a house on an empty lot. They need to be armed with the best tools to do their best work. If you give them old equipment, they will spend more time working around it than actually building. Endpoint Privilege Manager lets developers do what they do best – without interrupting their workflow with compliance and security requirements – so that they can write code faster.
Developers don’t need to be the last hold out for administrator rights within an organization. Learn how this is possible today.























