
When complying with regulations and frameworks, it’s hard to keep up when the rules keep evolving.
Auditors are no longer just seeking reports on what your identities can access – they now require proof that you have controls for securing those identities (like a math assignment, you have to show your work).
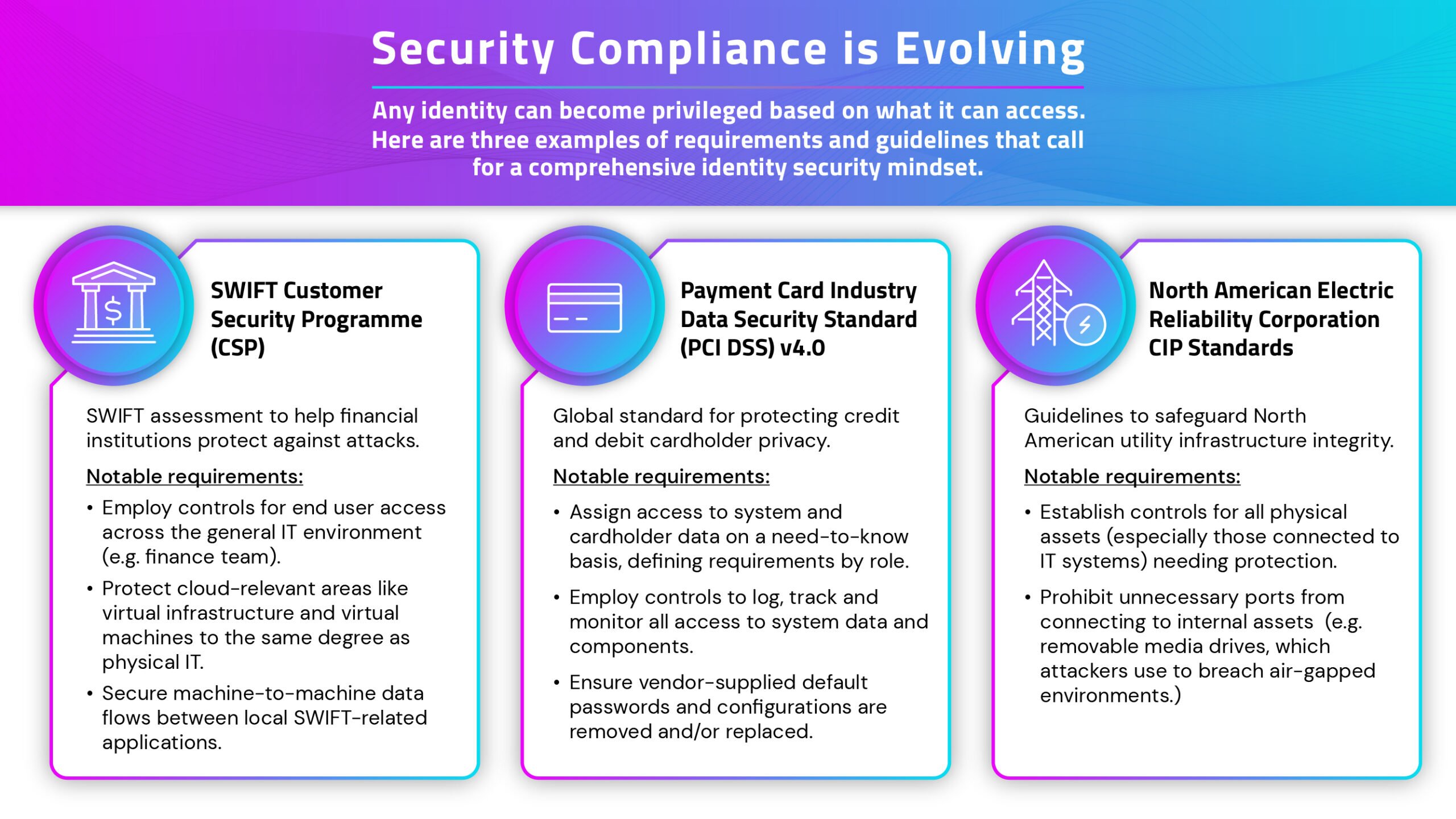
And if a framework or regulation’s requirements previously focused on highly privileged IT users’ access … that’s evolving too. While foundational PAM controls and reporting will always be essential, now you must apply the requirements to a broader range of human and non-human identities across any environment.
What does this expanded focus look like? Here are a few examples:
- The NIS2 directive emphasizes strengthening security for critical infrastructure sectors, which are increasingly reliant on cloud infrastructure and operational technology (OT), two areas full of frequently-targeted identities.
- The Digital Operational Resiliency Act (DORA) calls upon financial services companies to apply security oversight to internal users and third parties (e.g., vendors) with high-risk access.
- The NIST Secure Software Development Framework requires that software developers and procurers attest to adequate and proper security features, including identity management.
Meanwhile, the stakes of security compliance keep rising. The average cost of a data breach increases by as much as 12.6% when an organization is found to be non-compliant:
Average cost overall: $4.45 million
Average cost when non-compliant: $4.67 million
Average cost when highly non-compliant: $5.05 million
The good news is that there’s a direct correlation between strong controls and strong compliance. With the right capabilities for discovering, securing and reporting high-risk access, you can achieve a proactive stance to meet regulatory demands. In this post, we’ll explore some key steps you can take.
Discovering and Assessing High-Risk Access
You can’t protect (or report on) what you can’t see. And that’s why it’s so concerning that 62% of security decision-makers lack a complete picture of human and non-human access to sensitive resources.
Let’s look at a few examples of how discovering high-risk access can bolster your visibility, security, and, in turn, compliance posture.
One place to start: conduct an inventory of all accounts with administrative or elevated privilege to systems, apps, servers, networks and more. Another critical step is discovering privilege across your organization’s myriad endpoints, like workstations and servers. These are fundamental types of visibility; many organizations are accustomed to them.
But when we delve into new types of identities and environments, compliance becomes more difficult.
For example, developers and cloud ops teams are often over-permissioned with direct access to sensitive resources as their organizations rush to innovate. A CyberArk analysis of the three major cloud service providers shows that a user can access approximately 1,400 native services that, collectively, have over 40,000 access controls.
As part of their compliance programs, security teams should lean into cloud complexities and discover the following:
- Over-permissioned IAM roles and excessive permissions.
- Toxic combinations of permissions allowing privilege escalation or lateral movement.
- Unmanaged shared accounts and their myriad dependencies.
- Hard-coded credentials for developers working in the cloud.
- Everyday employees’ access to business applications.
In many cases, it’s up to you to interpret compliance requirements and guidelines in the context of new identities, environments and threats (these variables won’t necessarily be mentioned by name in a 100-page regulatory document). In other cases, the direction may be clear-cut, calling out specific areas like virtual infrastructure. Regardless, high-risk access – in all its shapes, forms and locations – requires fierce protection.
Implementing and Demonstrating Identity Security Controls
As mentioned, giving auditors a report on what you’ve discovered is only part of the job. You must demonstrate that you have strong controls in place to reduce risk and build organizational resilience against attacks.
Let’s say you’ve completed an inventory of high-risk across privileged IT users and accounts. Your next step is securing that privileged access. This starts with creating policies and implementing controls around password length, complexity, storage and rotation schedules. The work continues with steps such as enabling just-in-time (JIT) access and requiring multi-factor authentication (MFA).
What comes next after you’ve finished discovering privilege across your organization’s endpoints, like workstations? Here, a near-term priority would be revoking local administrator rights. An essential next step would be implementing capabilities to elevate privileges for authorized applications or tasks. These are effective ways to protect against ransomware – and great proof points for auditors to demonstrate progress.
As mentioned, even if securing access in the cloud isn’t explicitly described in a regulation – you’re still on point to bring entitlements and roles into compliance. Where to start? Consider applying a fast-emerging security principle known as zero standing privileges (ZSP), which – among many benefits – can help your organization by:
- Reducing the risk of credential theft by preventing standing access.
- Enforcing real time least privilege in the cloud by granting only the relevant permissions a user needs – and only when required – to accomplish a given task.
- Invalidating developer secrets that are embedded into code.
Gaining Nonstop Visibility Across Identities
You can build upon the findings from your initial discovery process with ongoing, real-time visibility into the access (and actions) of identities across your organization.
This is where it’s essential to look beyond siloed categories of controls or tools. We recommend an integrated identity security approach, where the underlying solutions can share information, act on insights and provide a unified view of audit data across all forms of human and non-human access.
With this approach, you can gain a comprehensive view of who has privileges and authorization to what resources, with capabilities for discovering, adjusting, certifying and revoking access.
With identity security, you can bring together:
- Session recordings and audit trails for high-risk scenarios – applied to highly privileged IT users and third-party vendors or workforce users in web applications storing sensitive data.
- User behavior analytics for building a knowledge of each user’s access behavior, authentication history, and anomalous activity.
- Audit trails to track and analyze privilege elevation attempts for human users and applications, enabling continuous visibility and control over endpoints.
- Integration with security information and event management (SIEM) tools for collecting/exporting log data.
Gaining Efficiencies to Help Overstretched Security Teams
Improved visibility and controls can help you build a proactive stance to meet auditors’ requirements. But how do you account for the limitations many organizations have regarding time, bandwidth and staffing?
For example, research shows that the mean time for organizations to identify a data breach is 204 days. And yet, the SEC now requires public companies to report attacks within four days of determining an incident is “material.”
How can organizations be proactive when timelines are tighter than ever?
Organizations can gain back time and potentially save money by applying automated capabilities to replace resource-intensive, manual tasks that often bog down security teams. This includes automating governance processes to ensure checks and balances are in place for maintaining compliance.
For example:
- Continuously enforcing least privilege with access reviews and certifications scheduled for recurring dates.
- Integrating access certification processes with your privileged access management (PAM) program and generating detailed logs and reports for audits.
- Continuously discovering which identities have access to specific privileged accounts and sensitive resources.
Building Compliance Strategies to Earn Auditors’ Trust
Visibility and controls can’t exist in a vacuum; they need to be part of a strategy that you can communicate to auditors. Here are three key building blocks for developing a compliance program that reflects today’s realities.
1. Discover and Plan
As mentioned, you can only secure and protect what you know. This part goes beyond an inventory or system discovery process to include:
- Engaging in dialogue with relevant teams (application, support, etc.) to understand how they currently work.
- Documenting their systems and access – but also ensuring they’re on board early. Successful adoption requires winning hearts and minds.
2. Implement and Rollout
If you’re regulated or if external auditors have called out gaps in controls, focus your implementation on a combination of:
- Prioritizing critical systems and reducing complexity, e.g., avoid getting bogged down by low-priority, high-complexity use cases.
- Employing automation from the implementation, e.g., automated checks and balances, to ensure recurring access certifications.
3. Expand and Communicate
You can’t do everything on day one. But in the same breath, attackers only need one gap to breach and wreak havoc. A proactive approach means building:
- A clear plan for how you intend to bridge gaps identified in your discovery process. Audits and reviews are always a work in progress.
- An implementation roadmap for a) progression tracking and b) open dialogue with regulators to discuss plans, goals and gains.
Building a Proactive Compliance Approach Centered on Identity Security
The best practices we’ve discussed apply to a wide range of frameworks and regulations across industries and geographic regions. No matter what, the connection between a strong security posture and a strong compliance program is clear. If you have full visibility into what your identities can access, complemented by controls for securing that access, you’ll be in a much better place to meet auditors’ requirements.
If you’d like to learn more, here are two resources that can help you:
- Watch our webinar, “How to Achieve Continuous Audit and Compliance with PAM.”
- Download the CyberArk Blueprint for Identity Security Success.
John Natale is a senior content marketing manager at CyberArk.























