
If the cybersecurity industry was to adopt a motto, the Summer Games’ 2021 “Faster, Higher, Stronger — Together” adaptation should serve as inspiration. As high-profile ransomware attacks continue unabated, the need for a collaborative and unified security approach has never been greater.
Combating today’s advanced cyber threats requires a powerful combination of deep security expertise, diverse experience, shared intelligence, proven processes and defense-in-depth tools — something no single vendor can fully address. That’s why cybersecurity needs to be tackled as a “team game,” and organizations have a vested interest in partnering with one another to build upon strengths and deliver holistic solutions that help defenders stay a step ahead.
At CyberArk, this belief is a foundational tenet in our approach to building technology partnerships that deliver long-term value to our customers. And our C3 Alliance is proof of this ongoing commitment. Today, we have more than 100 certified partnerships with leading providers of enterprise software, infrastructure and security solutions — all featured on the CyberArk Marketplace. This team game mindset is also why we’re part of the Identity Defined Security Alliance (IDSA), a growing community dedicated to helping organizations reduce the risk of breach by combining identity and security strategies.
Training for the Big Game… Ransomware Hunt
Security teams aren’t the only ones preparing for the main event — the inevitable breach. With an eye on the prize, attackers are just as busy innovating and forging alliances. Take ransomware attackers, for example. To accomplish large-scale, targeted campaigns, often referred to as “big-game hunting,” they need to put in the work in advance, pooling necessary resources, doing reconnaissance on their intended victim organization (often for months or even years) and meticulously social engineering specific individuals with direct access to critical assets and systems.
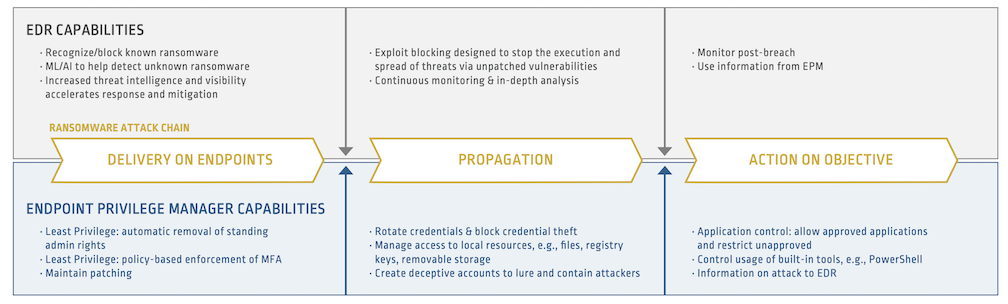
In the following ransomware attack chain example, the attackers’ goal is to hold a global financial service organization’s highest value data hostage through encryption and then execute a double-extortion attack by planting a hidden back door. It’s a sophisticated sequence, but one that’s growing in popularity. Here are four attack steps necessary for them to “stick the landing:”
- Deliver ransomware on the endpoint. The attackers use social engineering tactics to identify their targets — which include highly privileged Microsoft Windows and MacOS administrator accounts — then phishes for poorly protected credentials to gain an initial foothold. This is relatively easy to accomplish since maintaining visibility of dynamic admin privileges on endpoints is a challenge for many organizations, while managing them securely without hindering productivity is notoriously difficult.
- Escalate privileges and fortify access. Once inside, the attackers move between identities, applications and systems to uncover new levels of privileged access to plant and execute the code. They also take evasive action, disabling existing endpoint security and security monitoring tools where possible so they can search for more machines and sensitive data.
- Maximize attack impact. As the ransomware propagates, the attackers disrupt backups, delete shadow copies and unlock files to maximize the impact of the attack — while leaving hidden identities and a back door for future data extortion.
- Execute ransomware. The attackers accomplish this by using read/write permissions to encrypt files, holding them captive and demanding a sky-high ransom, knowing that the organization is highly motivated to pay because of downtime sensitivities.
Fighting Ransomware with a Team Approach
To outperform their adversaries, defenders must do more than just find and block the malware itself. A winning approach to ransomware protection also involves controls and methods that stop attackers from gaining and using powerful privileges to do harm — at every point in the attack chain. This takes a collaborative team effort.
Strong security at the endpoint involves an endpoint detection and response (EDR) solution. EDR technology has come a long way in recent years, and can capture endpoint activity through continuous monitoring, deliver visibility and in-depth analysis and accelerate security operations efforts. According to a 2021 SANS survey, 51.6% of compromises were detected by EDR solutions. And yet, these tools are not designed to specifically look at and securely manage identity and privilege — on which many ransomware attacks depend.
That’s where a reliable teammate who’s trained hard and proven their value comes in: CyberArk Endpoint Privilege Manager (and yes, we can keep this Summer Games analogy going all day long). Designed to substantially reduce the identity-related attack surface presented by distributed endpoints, CyberArk Endpoint Privilege Manager combines least privilege defense, credential theft protection, application control and ransomware blocking. This creates an environment in which other security solutions can play their roles more effectively
In our example attack above, EDR could recognize and stop known ransomware, while prioritizing alerts and fast-tracking investigation and response efforts. For strains evading detection, CyberArk Endpoint Privilege Manager would make it difficult for attackers to gain an initial foothold by automatically removing admin accounts left on endpoints — while blocking attempts to steal credentials cached by web browsers, password managers, single sign-on solutions and other programs.
If any ransomware managed to get through, CyberArk Endpoint Privilege Manager’s strong application controls would allow it to run only under certain conditions, with set policies around read, write and modify capabilities. Meanwhile, lateral movement would be restricted by multi-factor authentication (MFA), and strong least privilege enforcement would inhibit further propagation and damage. What’s more, the attackers’ chances of building (and successfully hiding) a back door would be significantly reduced.
This dynamic duo also works in concert to help organizations mitigate the risk of future attacks. CyberArk Endpoint Privilege Manager produces valuable intelligence on privilege abuse attempts, which can be used to extend EDR solutions’ capabilities so endpoint attacks can be identified and blocked before impact.
Getting Ransomware-Ready
“All organizations must recognize that no company is safe from being targeted by ransomware, regardless of size or location,” wrote U.S. Deputy National Security Advisor for Cyber and Emerging Technology Anne Neuberger in a recent memo.
Of course, getting ransomware-ready doesn’t end with beefing up your organization’s integrated security toolkit. Ongoing cybersecurity training, bidirectional information sharing, adherence to strong cybersecurity fundamentals and frameworks and a strong focus on data hardening are also essential elements of a multi-layered strategy.
“To understand your risk, business executives should immediately convene their leadership teams to discuss the ransomware threat and review corporate security posture and business continuity plans to ensure you have the ability to continue or quickly restore operations,” Neuberger wrote.
And cybersecurity companies play a critical role in helping organizations prepare. By embracing a team approach — and working together in solidarity — our industry as a whole can drive more responsible, accountable and effective control of the digital IT environment. That helps organizations combat evolving ransomware threats and gives them the security confidence to achieve their own gold-medal goals.























