
A digital identity, as we discussed in our earlier blog, is a unique representation of the real-world individual in an online world, as the individual participates in an online transaction. In many cases, a service or a Relying Party (RP) does not necessarily need to map that digital identity to the real-world identity of the individual, especially in cases where there is a genuine need to ensure the complete protection of the individual’s privacy and even anonymity. But in other cases, for reasons that could range from regulatory (e.g. Know Your Customer) and security (fake accounts in social media, DeepFake) to others, there may be a need to ensure that the digital identity is mapped to and validated against a unique real-world individual. This process of mapping and validation is called enrollment and identity proofing.
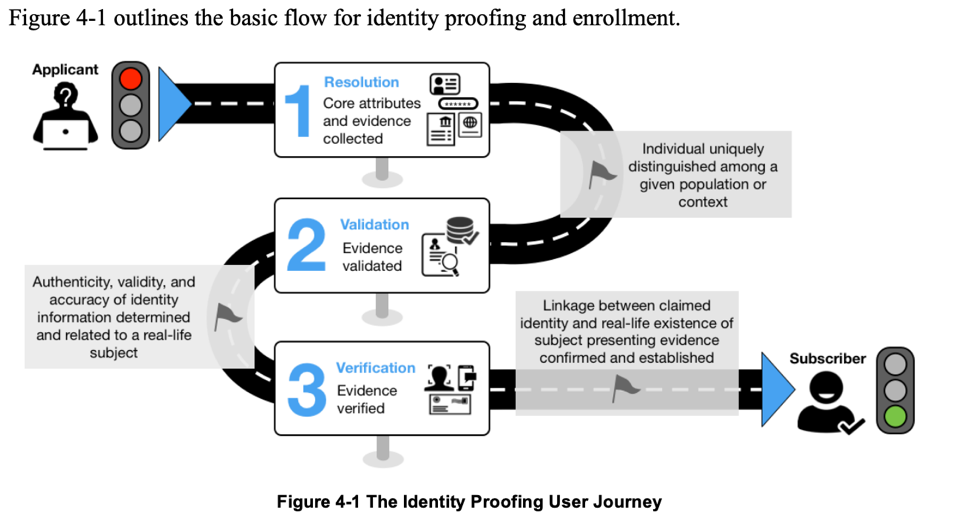
Figure: The Identity Proofing User Journey, Source: NIST Special Publication 800-63A
Identity Assurance Levels
The “strength of the assurance” with which this digital identity is mapped to and validated against a unique real-world individual is referred to in the NIST guidelines as Level of Assurance. NIST defines three levels of assurance (LOA) for the identity proofing process — 1, 2 and 3 — in increasing order of their strengths.
Identity Assurance Level 1 (IAL1)
NIST provides the following description for IAL1: “There is no requirement to link the applicant to a specific real-life identity. Any attributes provided in conjunction with the subject’s activities are self-asserted or should be treated as self-asserted (including attributes a CSP asserts to an RP). Self-asserted attributes are neither validated nor verified.”
In other words, IAL1 does not require any verification of claims and attributes that the user provides to the credential service provider.
Identity Assurance Level 2 (IAL2)
For IAL2, NIST provides the following description: “Evidence supports the real-world existence of the claimed identity and verifies that the applicant is appropriately associated with this real-world identity. IAL2 introduces the need for either remote or physically-present identity proofing. Attributes could be asserted by CSPs to RPs in support of pseudonymous identity with verified attributes. A CSP that supports IAL2 can support IAL1 transactions if the user consents.”
IAL2 allows for remote or in-person identity proofing. Example of this proofing includes services that may request an individual to prove proof of possession of an identity document, such as a Driver’s License or a Passport. As part of this, collection of personally identifiable information (PII) should be kept to a minimum – only to resolve the user’s identity in the context of the service that requires the identity. Also, the credential service provider may collect biometrics for the purposes of non-repudiation and re-proofing.
Identity Assurance Level 3 (IAL3)
IAL3 is described in the following way: “Physical presence is required for identity proofing. Identifying attributes must be verified by an authorized and trained CSP representative. As with IAL2, attributes could be asserted by CSPs to RPs in support of pseudonymous identity with verified attributes. A CSP that supports IAL3 can support IAL1 and IAL2 identity attributes if the user consents.”
In essence, IAL3 is stricter than IAL2 in terms of requiring further and stronger evidence of the user’s attributes so as to protect the identity and the relying party from impersonation, fraud or other such issues. Biometrics are considered mandatory as part of IAL3.
Summary of the IAL Requirements across LOA 1, 2 and 3
The actual requirements of the three IALs are far more comprehensively discussed in the document, but below is a summary table discussion them, also courtesy the guidelines document.
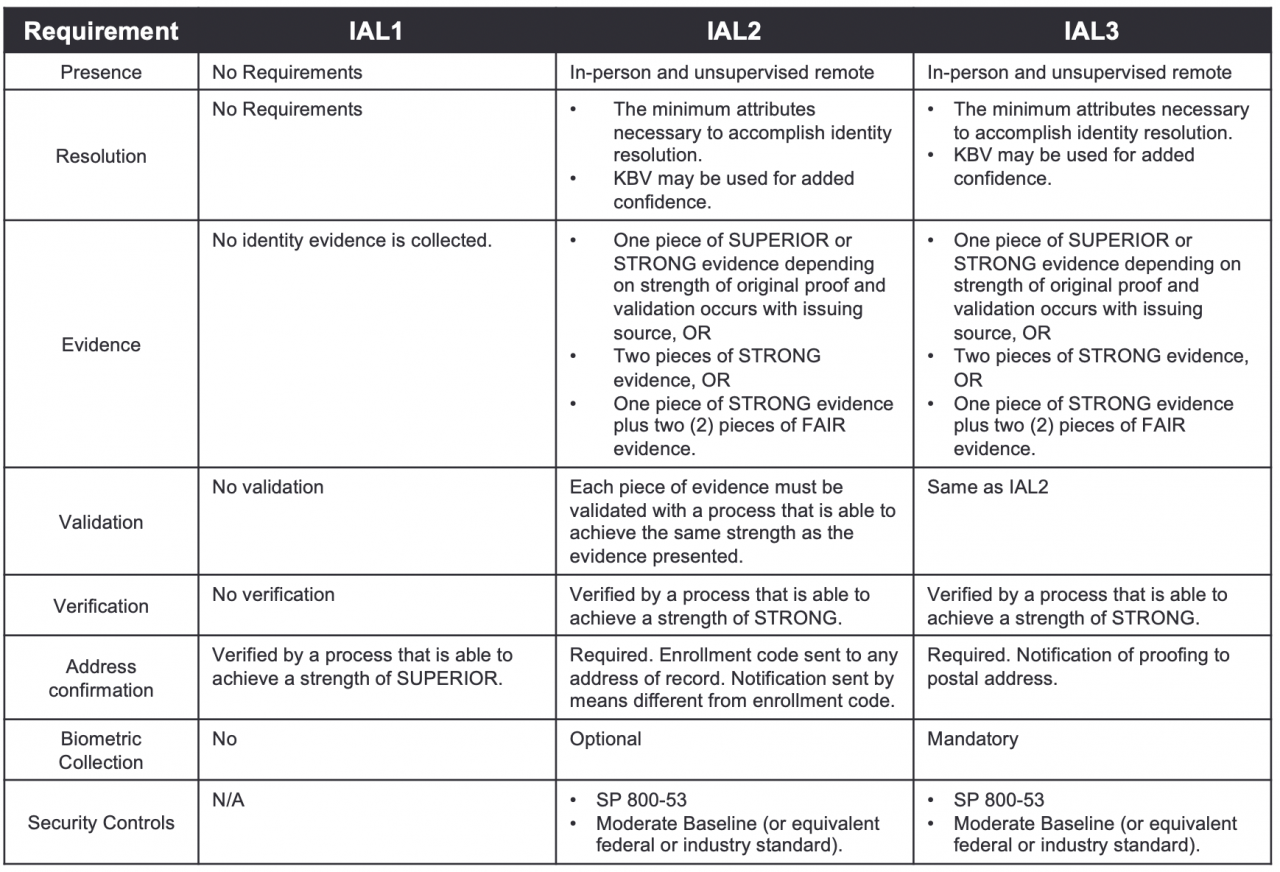
The guidelines document goes into much more detail about items such as what does “WEAK, “FAIR”, “STRONG”, “SUPERIOR”, etc. mean in the context of verification and validation of credentials.
Selecting an IAL
Selecting an IAL for your service (relying party) can be a difficult proposition, but NIST has been kind enough to include an IAL decision tree as part of the main 800-63-3 document, as shown in the image below.
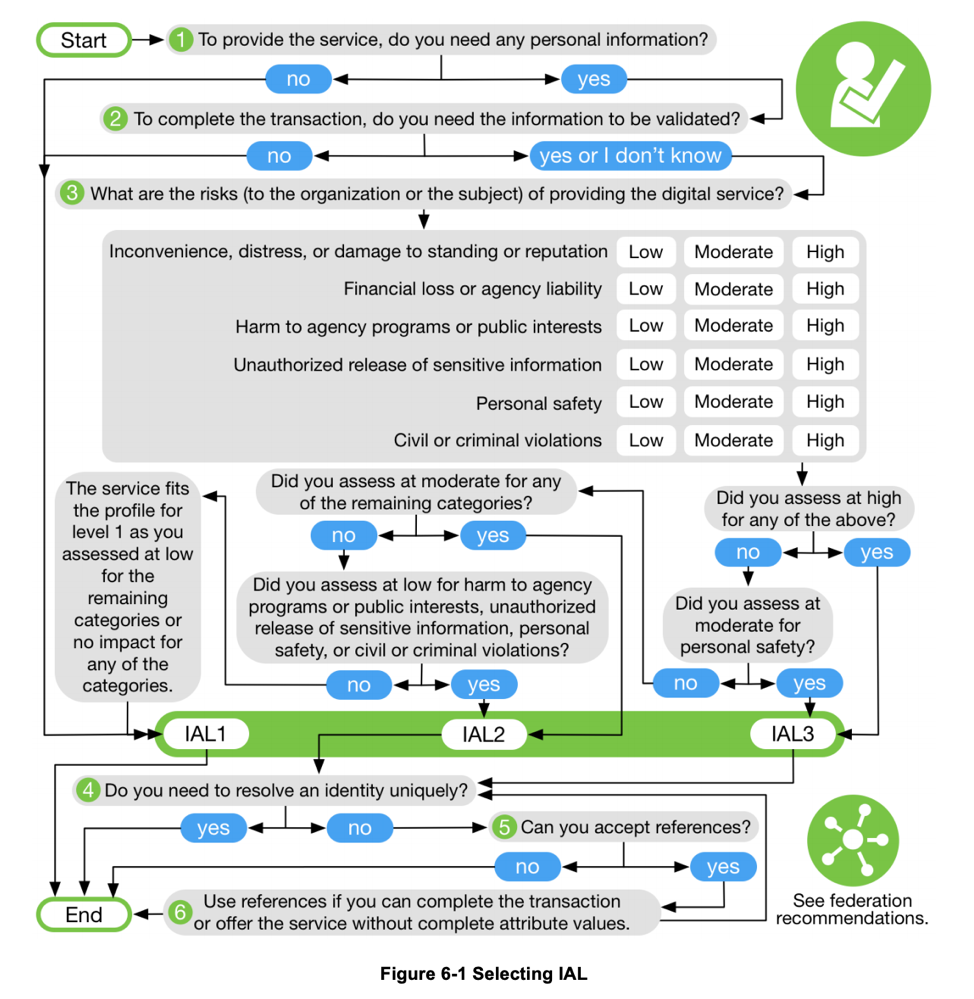
The document also goes into more details on the six decision points above.
The Road Ahead…
Enrollment and Identity Proofing is increasingly gaining in importance as we see digital transformation of organizations and business models across the board resulting in an explosion of digital services. With this explosion, we’re also starting to see more impersonation and fraud in the consumption of those digital services. New models like Forrester’s Zero Trust framework, or Gartner’s CARTA are also increasingly incorporating capabilities related to verification and validation of the user’s real-world identity along with proof of possess of authenticators into the process of authentication and authorization to digital services. Along those lines, Idaptive continues to partner with vendors in the enrollment and identity proofing space to augment our authentication and federated assurance capabilities, in our goal to secure and protect access to online services.























