
Security used to be simpler. Employees, servers and applications were on site. IT admins were the only privileged identities you had to secure, and a strong security perimeter helped to keep all the bad guys out.
Times have changed. Attackers targeting identities is not new. What’s different is the dramatic increase in the quantities and types of identities, attacks and environments. Developers, machines, in-house teams and contractors are requesting different kinds of sensitive access in hybrid and cloud environments. Cybercriminals are using AI to capitalize on the complexity and exploit the most minor oversights at scale. Threats can arise from anywhere, both inside and outside the organization. Traditional defenses are no longer enough.
At this blink-and-you-miss-it pace, 93% of organizations experienced two or more identity-related breaches last year. We’re fast approaching a world where a privileged identity could be compromised every two seconds.
If you’re like most security leaders, you don’t need another wake-up call. You’re wide awake. In this primer, we’ll show you how a modernized approach to privileged access management (PAM) with intelligent privilege controls can meet the demands of modern threats, adhere to Zero Trust principles, secure the right level of access for the right amount of time – all with minimal user friction and maximum peace of mind.
The Enterprise Isn’t Safe Until ALL Identities Are Secured
PAM forms the backbone of modern security. It’s foundational to how organizations control, monitor, secure and audit the highest-risk access across an enterprise IT environment. But PAM is not a one-size-fits-all approach.
Today, every user can be a privileged user, but not every privileged user is a human. Privileged accounts often rely on default, shared or weak passwords and privilege creep, where users accumulate far more privileges than were necessary for their job function, is common.
Organizations need a way to identify, track and control the proliferation of privileged access. From these core PAM concepts and principles, the new discipline of identity security has evolved.
Identity Security: The Paradigm Shift
Identity security proactively verifies, monitors and secures all identities an organization uses, including applications, endpoints, infrastructure and data they access. It eliminates the outdated notion of trusting devices or users based on location and assumes (correctly) that threats exist outside and inside the network. This alignment with Zero Trust principles sees every access point as a potential point of compromise. It grants every user and every device the minimum necessary access to perform their functions, significantly limiting the potential impact of a breach.
The Right Intelligent Privilege Controls
This paradigm shift toward identity security also requires embracing a new concept: intelligent privilege controls.
Intelligent privilege controls dynamically protect any identity’s access to any enterprise resource, whether operational (personal), system (built-in local admins and break-glass accounts) or machine (non-human workload) access.

Enforcement of these controls can be based on several context factors, including the user’s level of authorization, the expected user experience and the risk level of the task at hand. User experience is critical; while every user needs to be secure, not every employee needs or expects to jump through multiple hoops to do their jobs. Constraints can even hinder successful adoption, especially for cloud operations and developer teams charged with innovating their organization’s business models.
Whether through web sessions, RDP, SSH clients or command-line interfaces to modern data bases and cloud platforms like AWS, Azure or GCP, intelligent privilege controls integrate seamlessly, delivering security without disrupting the user experience.
Examples of key intelligent privilege controls include:
- Access with zero standing privileges (ZSP) in cloud and on-premises environments ensures that access is secure, dynamic and aligned with the principle of least privilege (PoLP) and Zero Trust. ZSP differs from just-in-time (JIT) access with time-bound permissions that expire after use, significantly reducing security risks. It fully removes entitlements and roles until the user requests it, and then, after the session is complete, the privileges are removed once again. It can be seamlessly integrated into workflows, delivering productivity without compromising security.
- Credential vaulting and management can securely store authentication credentials in an encrypted repository, which is essential for implementing further security measures such as access controls, rotation and isolation, reducing the risk of identity compromise. It can also automatically update passwords according to a security policy, remove hard-coded credentials and implement on demand secret fetching at runtime, which can enhance security by reducing the exposure of sensitive data.
- Session protection, isolation and monitoring safeguard privileged and high-risk sessions across all enterprise resources, including cloud services, elastic and static infrastructure and workforce SaaS applications. These controls automatically analyze audit logs and session activities to detect unauthorized or malicious actions. They also protect browser-based sessions by blocking risky actions like file downloads, clipboard access and right-clicks – and by securing the Chrome process from hijacking. This isolates the user’s connection to the target resource, preventing external and insider threats from compromising identities and their sessions.
- Endpoint identity security controls continuously verify users throughout their session (a core principle of Zero Trust). This ensures the user’s identity remains unchanged since initial access, preventing privilege abuse and session hijacking by inactive or compromised accounts. It intelligently adjusts security measures based on contextual data like location or device consistency, reducing authentication steps for low-risk situations and increasing scrutiny when anomalies occur. This allows multi-factor authentication (MFA) to be both pervasive and unobtrusive, optimizing security without hindering the user experience.
- Intelligent identity threat detection and response (ITDR) identifies and responds to identity-related threats in-session and in-environment with automated actions like continuous or step-up MFA and session termination. ITDR continuously assesses each session to ensure the security status of the user and device remains unchanged since initial access. This guarantees that only the original user can resume the session. Additionally, elevation requests are automatically handled, freeing security teams to focus on higher risks. This ensures MFA is applied effectively, without unnecessary prompts, optimizing security without annoying users.
Different Roles Need Different Controls
Identity security programs are about more than standing up a cybersecurity tool. Each security practitioner must decide how much risk they’re willing to tolerate for each identity type, the type of resource they’re accessing — and how much friction that user will tolerate while doing their job. One-size-fits-all constraints frustrate users. No matter how that risk fluctuates, user experience must be consistent.
The following table provides examples of the right privilege controls correlated to the risk posed by each identity.
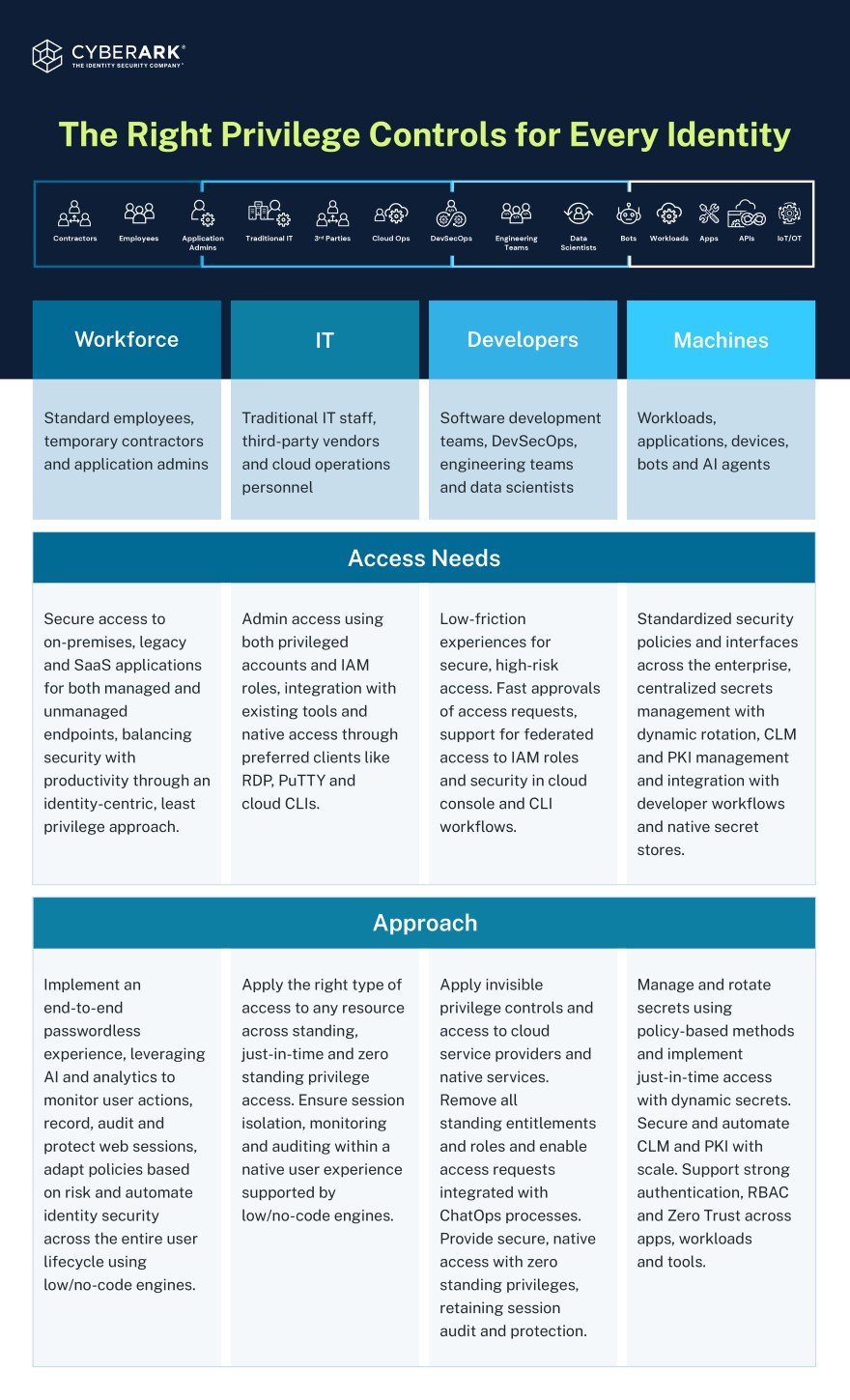
Getting Started with Intelligent Privilege Controls
The static access models of the past are no match for the triple threat of new identities, environments and attacks. With AI, attackers have the power to automate and enhance social engineering attacks, phishing schemes, voice impersonations and even video deep fakes. They are coming after businesses of every size and stripe, and until organizations act to protect themselves, they proceed on borrowed time.
From finance and HR workers to developers and countless machine identities, our world-class identity security platform can help you meet the unique needs of every single identity across your IT estate. Learn more about how intelligent privilege controls can be dynamically applied to protect a user’s access whenever it becomes high-risk and see why leading businesses depend on CyberArk to secure the identity lifecycle.
Amy Blackshaw is vice president of product marketing at CyberArk.





















