
Today’s digital workforce looks very different than it did 10 – even five – years ago. Employees, contractors and vendors are spread across multiple locations, some work remotely, and most use a variety of mobile devices to do their jobs. These increasingly distributed teams still need a way to access data and assets whether from the corporate network or the cloud. But, now they need that access to work across many different locations and devices.
With the expanding attack surface, cyber attacks on the endpoint, such as phishing and ransomware, need to be taken seriously. In the CyberArk Global Advanced Threat Landscape 2019 Report, 60% of respondents identified external attacks, such as phishing, as one of the top security risks for their organization and 59% of respondents identified ransomware as a top security risk.
What is Endpoint Security?
Coined in recent years, “endpoint security” is a term used widely by security professionals at cybersecurity events and conferences and on blogs and webinars. The actual definition of “endpoint security” varies widely depending on who you ask.
To understand the true definition of endpoint security, it’s first important to define what an endpoint actually is. An endpoint is any user device that connects to an enterprise network. This can include, but is not limited to, laptops, desktops, tablets, mobile phones and servers. Each of these endpoints provides an entry point to applications and corporate assets.
A Defense-in-Depth Strategy for Endpoint Security: Five Essential Tools
Historically, enterprises protected their laptops, desktops and servers with a firewall and perhaps an antivirus solution. But, as security threats evolve and digital transformation strategies accelerate, it has become clear that a more comprehensive, defense-in-depth approach is necessary to effectively mitigate risk. Since there is no silver bullet for endpoint protection, modern organizations must utilize a mix of advanced methodologies and tools. In this blog, I will outline the five technologies you must have in place to keep your laptops, desktops and servers secure.
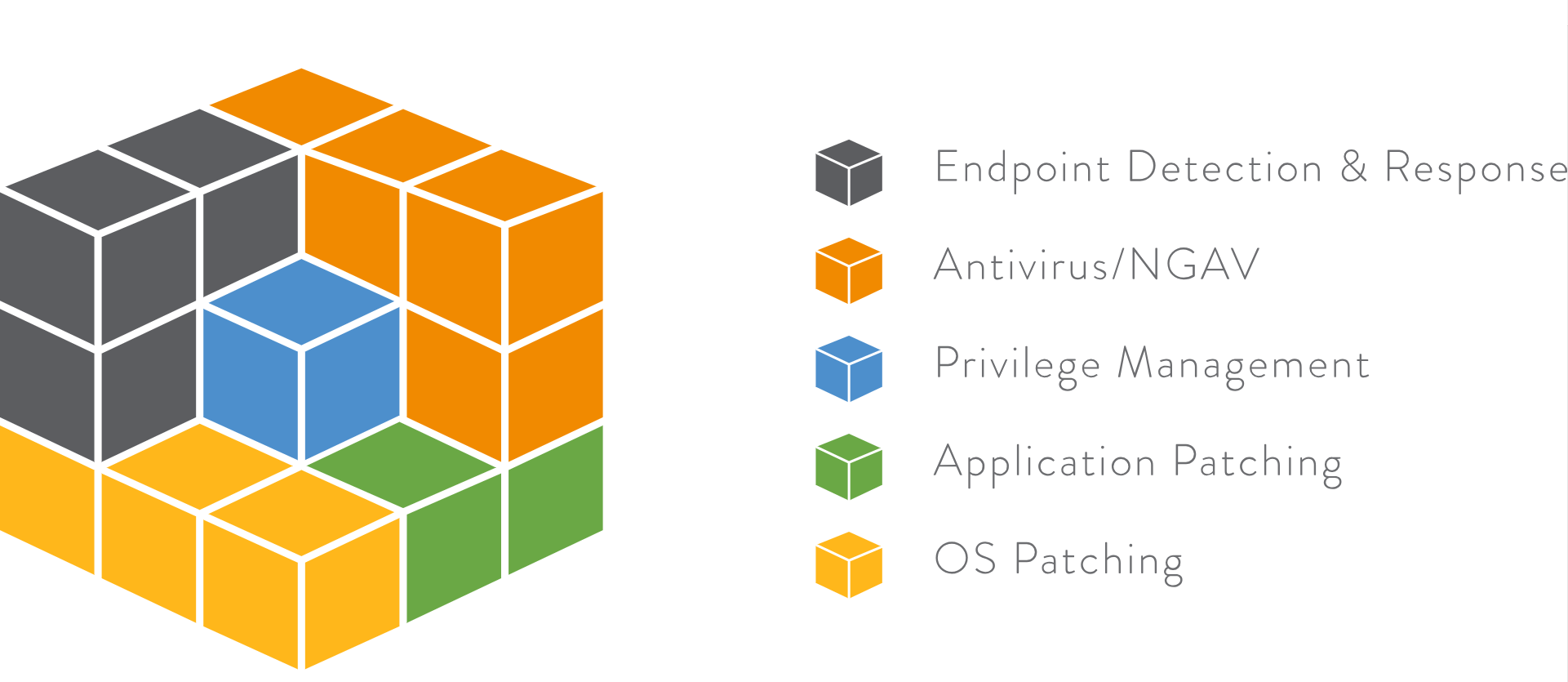
- Endpoint detection & response (EDR). Endpoint detection and response is a technology that addresses the need for continuous monitoring and response to advanced threats. Endpoint detection and response solutions collect, record and store large volumes of data from endpoint activities to provide security professionals with the comprehensive visibility they need to detect, investigate and mitigate advanced cyber threats.
- Antivirus or next-gen antivirus. For as long as endpoints have been, and will be, in existence (whether connected to the Internet or not), there has and will always be a need for antivirus solutions. There will never be a time when people – from mischievous youths seeking thrills to hardened cybercriminals looking to exploit billion-dollar companies – will stop looking to find ways to commit fraud, cause widespread damage or just experience the rush of breaking into a computer. Not every type of cyber attack can be prevented with antivirus software, but it’s an important tool to have in your cybersecurity toolset.
- Privilege management. Also known as the principle of least privilege (POLP), this is a concept and practice for limiting access rights for users and running processes only for those who absolutely require them to perform their tasks. Implementing least privilege management means enforcing the minimal level of user rights – or permissions – that allow the user to perform his or her designated role in the organization. As the endpoint attack surface continues to expand across digital enterprises, least privilege enforcement is a critical component of endpoint security, necessary for reducing the risk.
- Application patching. Software updates are important to your digital safety and overall cybersecurity. The sooner you update, the sooner your endpoint device will be more secure — that is, until the next update. With software updates, it’s all about revisions. These might include fixing newly discovered security holes or fixing or removing bugs. The challenge with patching is that it’s a never-ending job. In fact, studies show it takes enterprises an average of 38 days to patch a security flaw, also known as a software vulnerability. Hackers target these weaknesses by writing code for the software program vulnerability and packaging it into malware. Updating your software is an important step for keeping hackers out.
- Operating Systems (OS) patching. Similar to application patching, operating systems also need patching from time to time. OS patches can include critical updates, which, as the name implies, are widely released updates that apply a critical patch to a non-security-related bug. A security patch, on the other hand, is a widely released update that applies a patch to a security-related vulnerability. For instance, each Microsoft patch is accompanied by a Knowledge Base (KB) article identifier. Contained in a repository of over 200,000 articles, these KBs provide in-depth explanations about what was patched, how, the impact and any additional information that the end-user may find useful or necessary, such as Common Vulnerability and Exposures (CVE) identifiers that the update addresses. Apple releases its own equivalent of these OS patches. For security patching, they use “security updates cumulative” and operating system upgrades occur on supported hardware. To be truly effective, OS patching must be continuous, not just relegated to specific “patching periods.”
On Beyond Antivirus
Endpoint detection and response, antivirus software, privilege management, application patching and OS patching are each, individually, major contributors to the security of your endpoints. However, to be sure that your laptops, desktops and servers are as protected as possible, you need all five of the essential tools working together.
Many organizations depend upon antivirus software alone to keep their endpoints secure, but that isn’t enough. Privilege management is a key part of the successful security strategy. Establishing a policy of least privilege is essential for this. If you establish access control to ensure that no person has access to more than they need at any given time, it makes it much harder for attackers to escalate privileges and take aim at vital assets. CyberArk is the global leader in privileged access management and CyberArk Endpoint Manager can help your organization institute a policy of least privilege and get started on your journey to defense in depth.
Thinking about taking the next step to reduce your endpoint attack surface and strengthen your overall cybersecurity? Think least privilege. To discover more benefits of CyberArk Endpoint Privilege Manager, visit here.























