Organizations everywhere are undertaking major digital transformation initiatives. Whether moving critical resources to the cloud, or investing in greater automation capabilities, COVID-19 has dramatically accelerated these efforts to quickly enable remote work and keep businesses up and running. As this occurs, IT landscapes are growing in scale and complexity, resulting in a proliferation of privileged accounts. Related privileged credentials exist everywhere in these environments – including in tools and applications – and must be properly and consistently managed.
This sudden sprint to remote work also accelerated a shift to SaaS-based solutions that allow organizations to offload a good deal of the on-premises infrastructure and outsource ongoing maintenance and administrative work so that teams can focus more on security. This is particularly true for privileged access management (PAM) where many organizations have turned to Software as a Service (SaaS).
Source: Marketoonist.com
Implementing SaaS solutions to enable remote work is critical, but ensuring those solutions are also secure is just as important. This is particularly true for third-party vendors or contractors, who are often not a part of the company directory and require ephemeral access to sensitive systems on a day-to-day basis. For these users, as well as the remote workforce at large, many organizations have increased their reliance on VPNs, which have been linked to many high-profile breaches. In addition to the security risks, VPNs are also very difficult to set up and use for privileged access, as they do not provide the granular levels of remote access required for remote users who are at greater risk for misuse or attack if not properly secured.
A Powerful Integration That’s Quick to Deploy and Easy to Use
With a balanced security approach that brings the full benefits of SaaS, today CyberArk launched the first solution that combines all of the necessary elements for securing third-party vendor access to critical systems, without additional on-premises infrastructure. The powerful integration of CyberArk Privilege Cloud and CyberArk Remote Access provides the remote workforce with a strong mix of centralized privileged access controls, Zero Trust access, biometric multi-factor authentication (MFA) and just-in-time provisioning for third party vendors. Customers can now deploy a full SaaS-based privileged access management solution that secures remote user (employees, third-party vendors and contractors) access to critical systems managed by CyberArk. Customers can quickly secure and enable their remote workforce.
Here is how it all works.
First, as a remote user attempts to access the CyberArk web portal, they will get redirected to the Vendor Privileged Access Manager web interface. Vendor Privileged Access Manager then prompts the MFA: biometric authentication of a retina or fingerprint scan for smartphone users or a text and email combination, or voice calls for non-smartphone users. The user then completes the authentication and is redirected to the web portal where they can access the various systems they are provisioned to access.
All sessions that are initiated are routed through the privileged session management gateway to the Privilege Cloud Connector so that they are automatically isolated, recorded, and monitored. Further, the sessions are encrypted via an HTTPS tunnel between the Privilege Cloud Connector and the back end, hosted by CyberArk. The desired connection pings the vault to pull a credential but is never sent directly to the remote employee or vendor’s workstation.
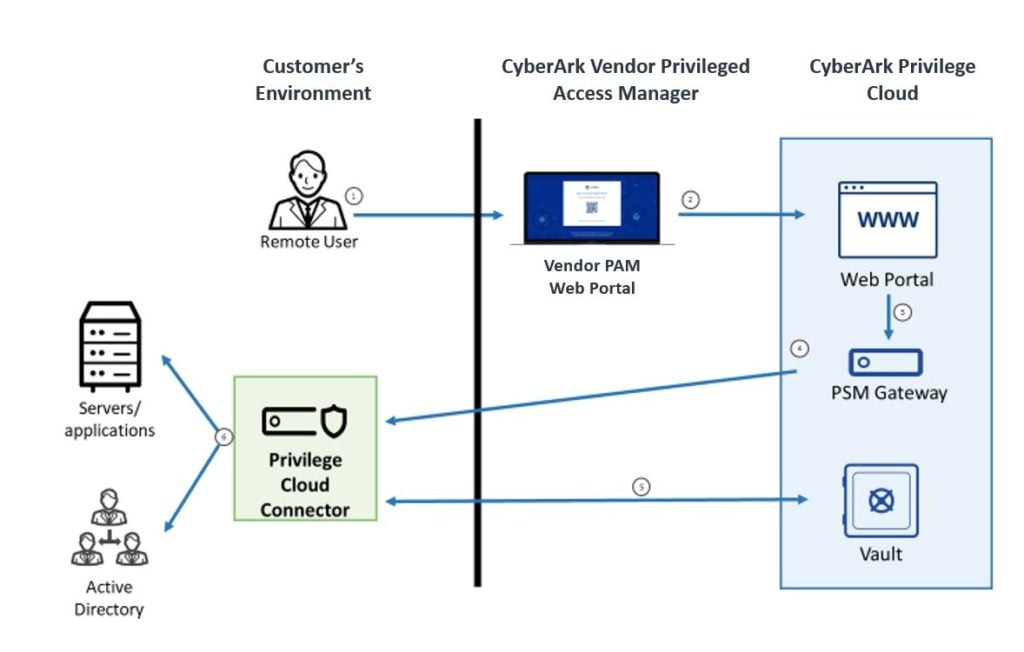
As shown above, CyberArk hosts the entire Vendor Privileged Access Manager and Privilege Cloud service in the cloud as a seamless workflow to enable remote employees and third-party vendors. The only self-hosted component of the solution for customers is the Privilege Cloud Connector, which is automatically hardened by CyberArk. CyberArk also hardens the underlying OS, helping organizations save additional time and increase confidence in the overall security of the back end.
Extending use cases is easy. Organizations can choose to rotate passwords, protect and audit cloud console administrators, manage service accounts, record and audit sessions, and secure access for users like third-party vendors and contractors, and more. Managing privileged access under one roof with one single, integrated SaaS solution provides the best of both worlds for security and operations. As remote work becomes even more deeply entrenched into how businesses operate, having a unified, end-to-end solution for securing the entire remote workforce has never been more important.
For those who would like to try CyberArk Remote Access for securing remote vendor access to CyberArk, we are now offering a 30-day free trial. Learn more about CyberArk’s leading PAM as a Service solution.























