
Evaluating user authentication methods based on usability, security, and deployability.
A plethora of user authentication methods exists today to distinctly identify a given user (or another entity such as a system). It all started with the humble password. These days, systems like Apple’s Face ID use a cutting-edge combination of sensors and neural networks to make the experience seamless yet extremely secure for end-users. It may not match the human brain’s identification mechanism yet – a person can detect an acquaintance by face, voice, walk, etc. – but it’s getting pretty close for sure!
Every user authentication method can generally be evaluated using the following three key parameters:
- Usability: How natural and hassle-free is it for the end-user to use this authentication?
- Security: How difficult is it for a malicious actor to trick the authentication?
- Deployability: How easy is it to deploy for all users across platforms, devices, geographies, etc.? An important consideration is whether the use case is B2C or B2E, meaning whether the end-user is a consumer or an employee.
Also, there are broadly three categories of user authentication methods:
- Something You Know: A shared secret like a password or secret question. Usually these are easiest to deploy across all devices and platforms, but not very secure as they are easy targets for phishing and other hacks.
- Something You Have: Another device such as a FIDO compliant key. Usually these are very secure from phishing and other hacks, as the private key never leaves the authenticator device. They are, however, prone to physical thefts and not easy to use in B2C scenarios, as a consumer usually doesn’t own special authenticator devices.
- Something You Are: These are basically biometric methods like a fingerprint or facial recognition. These are usually the most natural to use for end-users but depend very heavily on the underlying device or platform. They are clearly the future, but only if all platforms use secure hardware and software, and can play well with each other! They also almost always need a backup mechanism (for example, what if you cut your finger?) but this presents an Achilles heel, as the backup mechanism can potentially be targeted by an attacker.
Now that we understand the broad taxonomy of user authentication methods, here is a tabular view of some of the most popular authentication methods with scores for each of the three parameters. Please note that these scores are meant to be simple relative indicators to broadly understand the relative strengths and weaknesses of each method.
|
Authentication Methods |
Category |
Usability |
Security |
Deployability |
Comments |
|
Apple Face ID |
SYA |
9 |
8 |
2 |
Secure and easy to use, but only useful on some Apple devices, not very interoperable across apps. E.g. doesn’t yet support a standard like FIDO2, isn’t even supported yet on Macbooks. |
|
Face Recognition |
SYA |
9 |
7 |
2 |
Generic face recognition – inconsistent security, heavily depends on device hardware and software. E.g. security of Android face recognition depends heavily on the device brand. |
|
Fingerprint Recognition |
SYA |
7 |
7 |
4 |
Generally secure and more deployable than face recognition, getting more deployable every year. Pretty much all smartphones have a decent enough fingerprint scanner. |
|
SYH |
6 |
7 |
3 |
Only meant as a strong second factor, depends on compatible devices such as Yubikey, so widely used in B2E use cases but cannot be used in B2C. |
|
|
SYH |
6 |
8 |
3 |
Leverages biometric authenticators and is trying to make them interoperable across devices by working with all industry players, but has some time to mature in terms of support. |
|
|
SMS OTP |
SYH |
3 |
5 |
8 |
Not very secure as prone to SIM swap attack, but is heavily used as the second factor in B2C scenarios, as every user has a smartphone. |
|
SYH |
3 |
8 |
5 |
Quite secure, but needs an Authenticator app and the user needs to know how to set it up. It could be useful if the end-user is tech-savvy, usually B2E scenarios. |
|
|
Passwords |
SYK |
4 |
3 |
6 |
The most ubiquitous because of history and deployability has well known issues in security. All security professionals want it to go away as soon as possible. |
|
Secret Questions |
SYK |
5 |
2 |
7 |
Arguably worse than passwords, especially in the age of social media as lots of information of users is publicly available. |
|
Personal Info |
SYK |
6 |
0 |
8 |
Asking personal information such as DOB is a horrible method in the age of social media. It should not even be listed as an authentication method, but I have seen some services using it. |
|
Email OTP |
SYK |
4 |
5 |
7 |
A decent method for B2C scenarios like SMS and doesn’t depend on another device but relies heavily on the efficiency and security of the email service of the user. |
SYA – Something You Are; SYH – Something You Have; SYK – Something You Know
If we plot these scores on a bubble chart, with the size of the bubble representing Deployability, Security on Y-axis, and Usability on X-axis, it would look something like this:
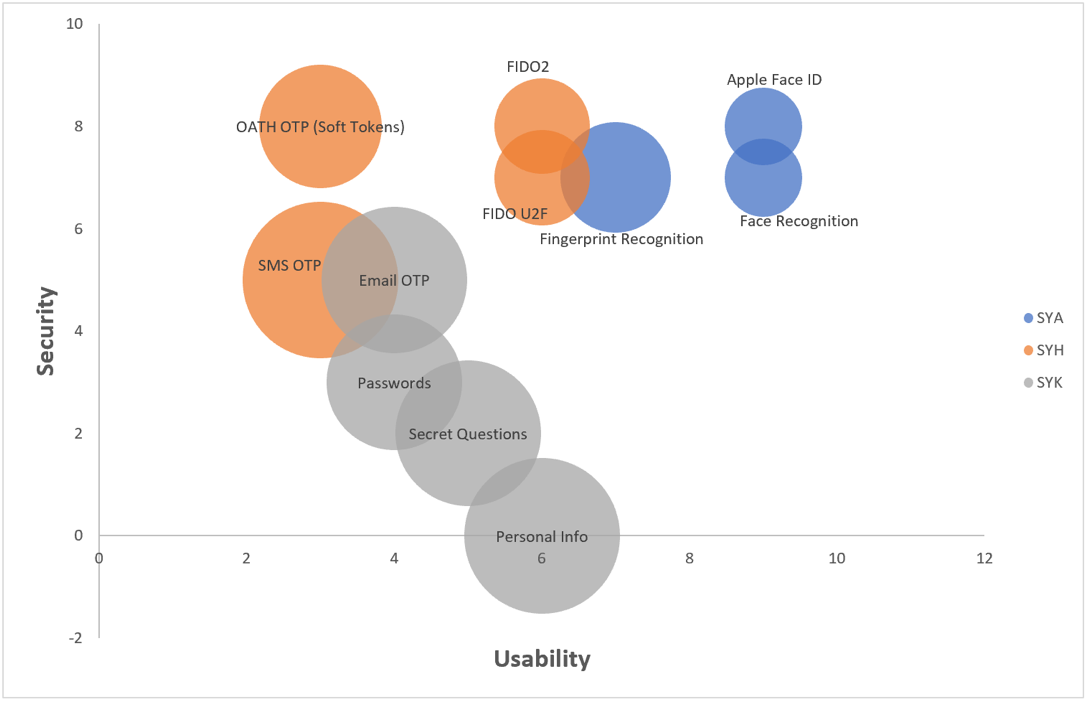
Comparison of User Authentication Methods on 3 parameters – Security, Usability, and Deployability
Size of a bubble indicates Deployability of that authentication method
Looking at this, you can easily see that in most situations a single user authentication method cannot be your silver bullet. That’s where intelligent adaptive MFA comes into the picture. It can decide when and whether to use a second factor, preferably from a different category than the first factor depending upon security policies or even patterns of usage analyzed by machine learning. This enables the security admin to cherry-pick the best combination of Security, Usability, and Deployability.
One must also consider the nature of end-users. A typical deployment for the B2E use case (end users are employees) may use certificate-based ZSO for most normal cases and add a second factor such as FIDO2 authentication. A typical deployment for B2C use case (end users are consumers) may use biometric if the device allows it, password as a fallback mechanism if the device doesn’t have it, and an SMS OTP as step-up authentication for important transactions, such as money transfer.























