
“What’s happening?”
In the movie Office Space, it was a question to dread whenever Initech Vice President Bill Lumbergh would lean over long-suffering employee Peter Gibbon’s cubicle wall with an unreasonable request. This, of course, set off a chain of events including job dissatisfaction, hypnotism to mitigate said job dissatisfaction … oh, and an ill-advised embezzlement attempt inspired by the plot of Superman III.
As a security practitioner who needs to secure applications used by your global workforce, you’re no stranger to the question of “What’s happening?”
However, in your context, there’s no comedy — only urgency, high stakes and in many cases, a lack of visibility into real-time events that could lead to a devastating breach, attack or even an insider threat. And chances are you’re hearing this question more frequently, partly due to the rapid adoption of cloud-based apps that — while crucial for empowering your workforce — also give everyday users access to sensitive resources.
Perhaps you used to focus your energy on the high-risk privileged users like IT admins. But now, virtually everyone across your workforce has privileged-level access to something.
So it’s becoming clear that, when it comes to Identity and Access Management (IAM), organizations need to look beyond the crucial point of authentication and add layers of visibility and security to the actions people take once they’re inside the applications.
Without that, a security team loses time, loses ground and likely loses sleep.
We know that burnout is a major problem in the cybersecurity industry, exacerbated by an incomplete view into threats, despite a constant barrage of alerts and data. In fact, 83% of cybersecurity professionals said they’re struggling to cope with security alert fatigue as they try to distinguish meaningful insights from false alarms.
If you’re feeling like this and you too are struggling to respond to fire drills regularly without the insight you need into what’s causing incidents, you should know you’re not alone on this one.
CyberArk recently surveyed 900 global security leaders and decision makers to learn how they are monitoring, auditing and securing end users’ activity within high-risk applications. These cloud-based tools, such as Salesforce and workforce collaboration applications, often contain sensitive data such as financial records, customer information and intellectual property. The survey participants shared insights on their limits and pain points, as well as their aspirations for how greater visibility into user sessions could help them.
It turns out there’s a major opportunity for improvement. Here’s a snapshot of what we learned.
Today, 63% of organizations give their typical end user access to between five and 10 (or more) applications that contain or enable access to resources that attackers would deem high value.

However, with access comes risk: 80% have experienced end users misusing or abusing access to these applications in the past year. This trend comes at a time when 97% of security leaders say credential theft is on the rise, with end users who have access to sensitive resources making up the biggest increase in targets by attackers.
When potential security issues emerge, security teams typically comb though user logs — sometimes thousands of lines — in search of clues to discover what happened. But nearly half (48%) of organizations surveyed have limited ability to view these logs and audit user activity. This keeps them in the dark about potentially risky actions taken in web application sessions.
With more insight into users’ actions within sensitive business applications, security decision makers believe they’d gain a wide range of benefits. For example, 41% of those surveyed say they’d be able to identify the source of a security incident more quickly.
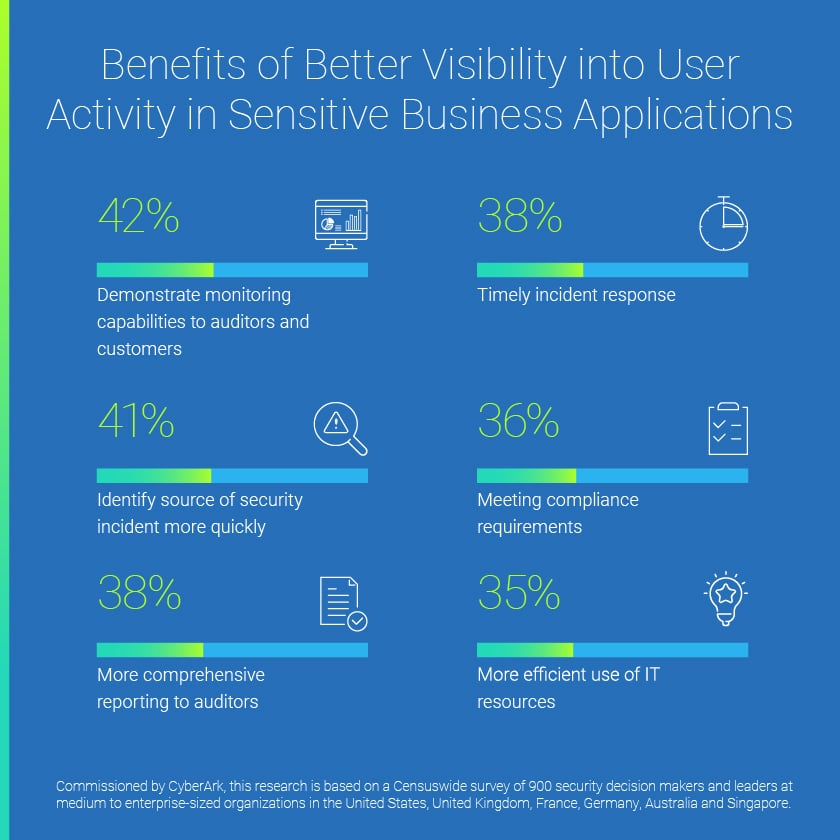
But with their current limitations, organizations may be at risk from insider actions, both from honest mistakes and malicious attacks (per the above mentioned plot of Office Space). And they may be vulnerable to external threats, such as identity compromise via phishing and credential theft.
So what can security decision makers do to improve their approach to web application security for high-risk user sessions?
It starts with asking yourself some important questions about the tools you use and the capabilities they offer. Some examples:
- Can your team easily produce a record of what goes on during specific end-user activity in a given application?
- If not, how much time do you lose to data log reviews, and how does that affect your window of opportunity for discovering what’s transpired?
- As you review user activity or behavior, how confident are you that the person who initiates a web session is actually the person using the application?
- And do you have the mechanisms in place to continuously verify a user’s identity in the event they were to walk away from their workstation?
Read our eBook The Hidden Gap in Web Application Security: User Sessions for a deep-dive look at our research findings that will help you evaluate how well — and how comprehensively — you are protecting your users’ sessions in applications that contain sensitive resources, in comparison with your peers. The eBook also provides insights to help you assess and improve your security posture.
With greater visibility, you can reframe the dreaded question “What’s happening?” into one of support, as in: “How are you doing?”
In light of the pressures today’s security practitioners are under, we could all use a lot more of that.























