
Protecting endpoints is more important than ever, as existing threats like ransomware continue to damage organizations and emerging threats like AI-driven attacks add to the problem.
As attackers find new ways to exploit an organization’s vulnerabilities, IT security teams find themselves under pressure to act quickly, often searching for new tools. However, when security solutions are bolted together hastily, problems arise, such as:
- The solutions are siloed and cannot share data on potential threats and turn insights into action.
- They also cannot apply an effective control for securing one type of identity (privileged user) to another type of identity (standard user).
This is why we advocate for identity security, both as a strategic approach and as a platform, to address gaps that often appear between patchy security technologies. Identity security provides a solid foundation and fuses the once-siloed security components into an integrated platform that’s designed to be impenetrable, multi-layered and identity-first.
For this to be truly successful, it’s important to take a unified approach. You must break down those silos by contextually authenticating all identities and then dynamically authorizing the least amount of privilege required for any change or action in the environment.
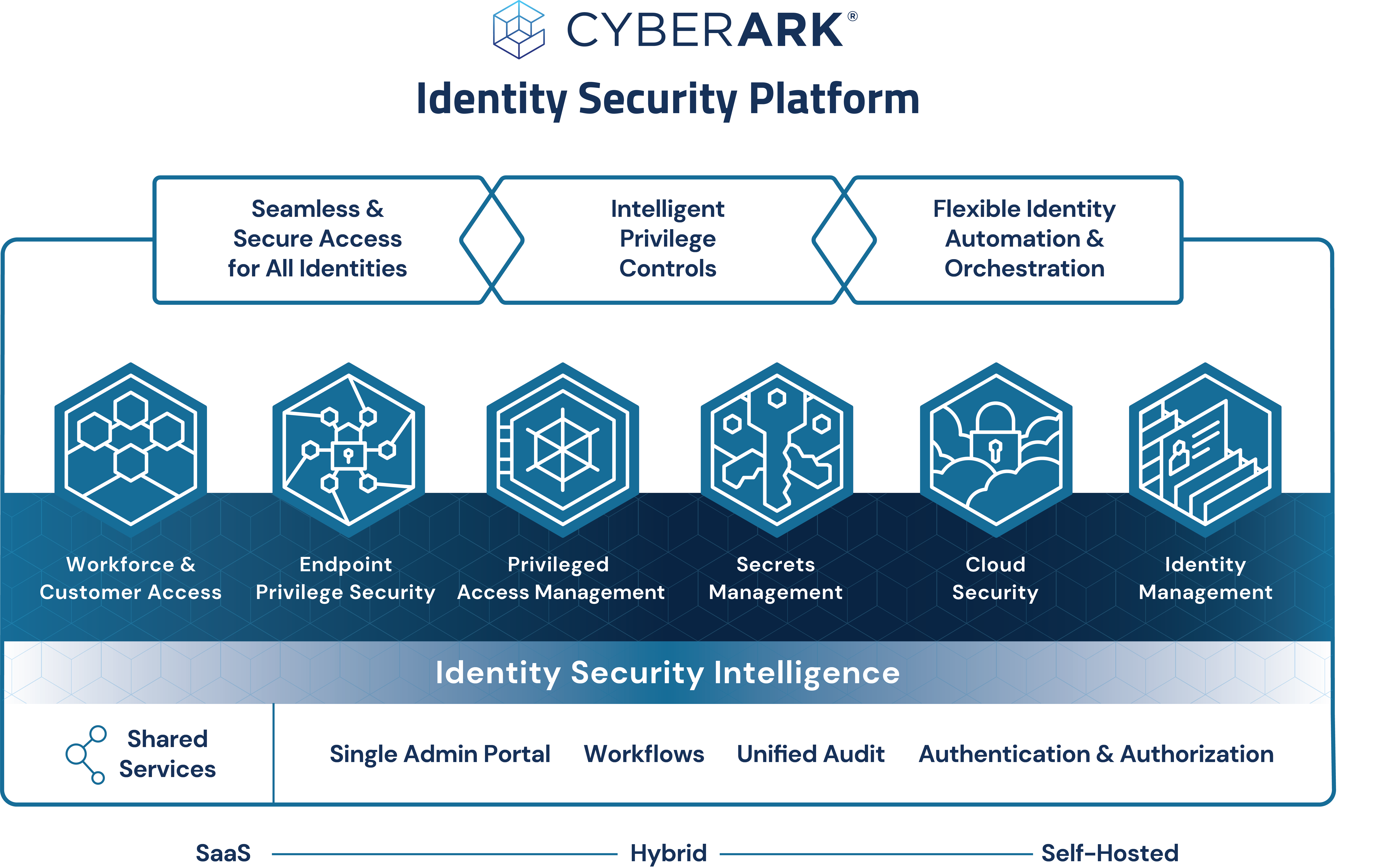
In other words, identity security controls are dynamic and adaptive in nature, so they can ensure the right level of access is granted based on risk. Looking at the following graphic, you’ll notice an integrated identity security approach spans six domains: workforce and customer access, endpoint privilege security, privileged access management, secrets management, cloud security and identity management.
In this blog post, I want to zoom in on one of those domains: endpoint privilege security. Let’s explore the role endpoint privilege security plays in an identity security platform, how it differs from endpoint privilege management and what capabilities and controls you should look for in a solution.
What Is Endpoint Privilege Security?
Endpoint privilege security ensures that organizations take control over unmanaged privilege on the endpoints to significantly reduce the area of attack and defend from threats such as ransomware.
It builds upon the existing access control components found in operating systems — accounts, account groups, file and folder permissions and access control lists. Granted, these controls are powerful because they are built into operating systems’ kernels. But they can be hard to manage in complex environments and at scale. (Worth noting, they also come very cheap computationally as they don’t require components such as complex heuristics, pattern extraction and matching algorithms, emulators, behavioral analyzers and such.) By introducing an efficient management layer on top of these mechanisms, endpoint privilege security can deliver foundational, granular and efficient security for any endpoint, a high level of visibility and control and role-specific least privilege.
Look Beyond Labels
Before we dive into the functional breakdown of endpoint privilege security, let’s briefly talk about naming. Within the IT security community – leaders, practitioners, analysts and more – there’s some complexity and confusion around how we name, define and refer to the act of securing endpoints. To be clear, I’m not pointing any fingers! However, it’s important to get the naming right when you’re determining the strategic approaches, controls and solutions needed to defend against threats.
A traditional way of looking at privilege management on the endpoint is to consider it a part of privileged access management (PAM) that is “landed” onto an organization’s endpoints. Through this perspective, many consider managing access to applications – the ability to run them – to be the main functionality. Therefore, this category is traditionally called “privilege elevation and delegation management” (PEDM). But there’s a problem: the word “endpoint” is notably missing from the name. Perhaps this why our industry more often calls these tools “endpoint privilege management” solutions.
I, however, argue that another, even more important word is missing from the fold, and that’s “security.” If you ask me, there’s a big difference between endpoint privilege management and endpoint privilege security.
- Endpoint privilege management helps organizations align to a key security concept – say it with me: “Nobody should work under an administrator account!” – and not lose too much in the process. Here, organizations have taken an important step in reducing risk, but by following up with “management,” the focus shifts to standard users and merely helps automate some IT helpdesk tasks as support tickets begin to flow in from users who’ve lost admin rights. You’ve checked one box on the security checklist but not much more – all while creating additional operational friction and load.
- Endpoint privilege security, on the other hand, requires implementing least privilege to the extreme, while also removing operational friction as much as possible. Least privilege is enforced across the board for standard users, advanced users and administrators alike. And it is role-specific, which means instead of only having minimum restrictions that can allow just about anything to fly under the radar, we can now really push this concept and implement security tailored for each role in a company – and they will love it! Least privilege is absolutely essential to endpoint (and not only endpoint) security because it limits the attacker’s ability to reach endpoints, gain persistence, collect and exfiltrate data, rely on existing tools, tamper with other programs and operating systems, conceal their presence and wipe evidence, tamper with security and deliver impact. This is, of course, a short version – but you can read more in this blog post.
Endpoint privilege security controls not only users’ permissions but those for applications as well, including execution chain, access to specific resources, ability to access files and so on. It also ensures that most critical data can be protected from any and every application, thus securing credentials, hashes, security tokens, passwords, cookies and so on across the operating system credential stores, third-party applications and browsers.
As noted, a litmus test to help tell endpoint privilege management apart from endpoint privilege security centers on a simple question: who is the end user you’re focusing on? If it’s standard (regular) users only, you are looking at endpoint privilege management. But if you’re focusing on every user – standard users and admins alike – that’s endpoint privilege security.
File this under “Why should our industry ever make things easy?” Many solutions in the market, each with their own different functionality sets and maturity levels, have some variation of “endpoint,” “privilege” and “manager” in the name.
But since we could argue that some endpoint providers belong in the “management” category while others belong in “security,” we’ll have to look beyond names. “Security” is different from any other word, as it is not a declaration or simple matter of branding – it’s a commitment. As such, security must traverse every aspect of a solution’s design, implementation, functioning and audit capabilities.
Here are some pointers you might find useful for evaluating endpoint privilege management/security controls and capabilities, keeping in mind how certain design decisions might affect users’ experience and, maybe more importantly, your organization’s security and compliance.
Endpoint Privilege Security – Controls and Functionalities to Look For
In an integrated identity security approach, every domain – from endpoint to cloud – is strengthened by forging bonds with each other’s functionalities and controls. This sounds like a cliché, but synergies do truly emerge thanks to tight integrations between identity security components. One example is a sudden tightening of elevation policies when a user’s actions, environment and location trigger adaptive, continuous authentication, risk threshold logic. The user will be asked to re-authenticate to perform a high-risk action when they wouldn’t normally get that challenge.
This tight integration really reduces operational friction while helping secure users’ environments and locations. Here are four areas of functionality to consider when vetting endpoint privilege security providers, keeping those silo-breaking bonds in mind.
- Functionality traditionally attributed to PAM -> PEDM:
- Zero Standing Privileges – all elevations happen just in time, according to policy
- Comprehensive privilege control of child processes
- Timed administrative sessions (just-in-time)
- Application and processes discovery and control
- Conditional privilege control policy elevation
- Privileged account discovery and removal/demotion
- Support for break-glass scenarios (offline devices, rollback of system configurations, etc.)
- Policy and event audit for application events and privileged actions
- Functionality from endpoint protection platforms (EPP):
- Application execution control (can it launch?)
- Application access control (what can it interact with — access to resources, such as intranet, internet, memory?)
- Application privilege control (can it elevate?)
- Prevention of exploits that abuse the execution chain
- File threat analysis, leveraging cloud-based reputation services
- Ransomware protection
- Ability to automate detection and response actions based on threat level and auto-execution of threat response playbooks
- Functionality from cloud workload protection (CWP):
- That of EPP (outlined above)
- API-based control (API-first implementation) for extensive automation
- Cloud workload hardening
- Ability to protect virtual machines, particularly persistent and non-persistent virtual desktops
- Ability to protect Desktop as a Service (DaaS) instances
- Ability to protect instances in public cloud infrastructures
- Ability to integrate with the cloud fabric to enable automated procurement, scaling and interoperation with cloud-native services
- Functionality from identity threat detection and response (ITDR):
- Active defense of user credentials (passwords, password hashes, login-key pairs, sign-in certificates)
- Active defense of session tokens (browser cookies)
- Active defense of security and authentication tokens
- Privilege deception
- Identity-specific, context-rich event recording
Bringing It All Together: Endpoint Privilege Security
To recap, in today’s threat landscape, it’s essential to do more than manage program elevation on endpoints. Organizations must enforce role-specific least privilege and protect machines with multilayered endpoint privilege security controls centered around identity. In this post, we explored the fundamentals of this critical, but often missing, area and the integral role it plays in a modern cybersecurity program.
Learn more about how CyberArk’s endpoint privilege security solution and its role in an integrated identity security platform help organizations enforce least privilege and protect against threats such as ransomware.
Andrey Pozhogin is a senior product marketing manager at CyberArk.























