
If you’ve never celebrated the Epiphany (or Mardi Gras in Louisiana), you have likely missed out on the tradition of the King Cake. It’s a coffee cake-type pastry with a small figurine baked inside that represents good fortune to the one who finds it in their slice.
Think of an organization’s most valuable assets as the figurine baked into a modern IT infrastructure. To do their jobs, hundreds or even thousands of remote workers, customers, vendors, devices, and applications have to bite into this “cake” regularly. While they’re (usually) not after the prize for themselves, they’ve opened up holes to the coveted figurine. And unfortunately, the “winner” is often a cyber criminal who has gotten inside the cake and chewed their way to the cake’s center where the prize awaits.
Today, there’s a good chance an attacker has already taken a bite of the cake. So the question is, how do you keep the coveted trophy away from undeserving fortune seekers?
This is the second piece in a three-part series on real-world cloud attacks, illustrating how cyber criminals and malicious insiders often compromise vulnerable cloud identities and manipulate privileged access to reach into cloud infrastructure and services, and inflict costly, damaging attacks. By adopting an attacker’s mindset, organizations can take a more proactive stance and start turning the tables.
Are Your Hard-Coded Credentials Ripe for Hijacking?
The code and scripts developers write often need credentials and secrets, such as SSH keys and API tokens, to access cloud resources and interact with other apps and tools. To save time, developers often embed these secrets into code. In fact, “hard coding” is a risky habit that’s been around as long as developers have. The problem is these hard-coded credentials (also called embedded credentials) are exposed to everyone else with access to the code.
As more and more organizations build and operate applications using cloud-native architecture, the risk of hard-coded credential compromise can increase. That’s because agile development settings typically exchange a lot of code with cloud-based repositories like GitHub. Each exchange can inadvertently expose credentials, including hard-coded credentials, to potential attackers, and sometimes, the entire public. North Carolina State University researchers found that over 100,000 of GitHub’s code repositories contained exposed credentials – and that was after scanning only 13% of the service’s total public repositories.
By taking just one leaked cloud credential from one identity, an attacker can gain entry to an organization’s environment, escalate privileges and potentially gain privileged access to highly sensitive cloud resources.
Step by step, here’s what a real-world cloud attack that hijacks hard-coded or embedded credentials might look like:
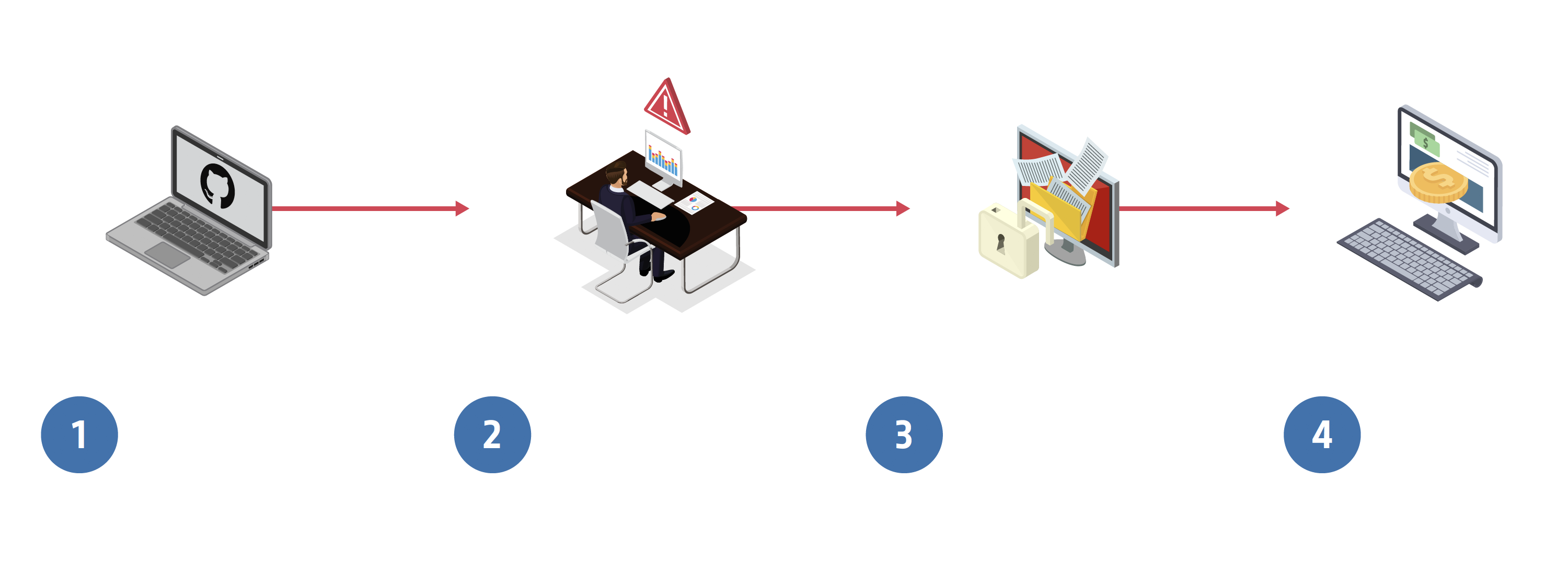
1. Gaining a foothold. A routine code exchange with GitHub contains embedded credentials. Using simple, publicly available harvesting tools, an attacker trawls the code for strings that correspond with cloud credential characteristics obtains access keys, and uses them to secure an initial foothold into the organization.
2. Escalating privilege. The attacker uses the stolen credential to escalate privileges, and with heightened access, begins to move freely with full access to a cloud database.
3. Gaining access. The attacker just hit the jackpot! That cloud database contained sensitive data on millions of customers and employees, which are stolen and leveraged for ransom.
4. The result. The organization pays tens of thousands of dollars in ransom to the attacker, as well as a hefty $1 million in regulatory fees.
Have Your Cake and Eat it Too
By removing hard-coded credentials and secrets in code, PaaS configurations, application development tools (such as orchestration platforms), and internally developed applications, following privileged access management best practices, and implementing strongly authenticated secret delivery mechanisms, organizations will be better equipped to keep their cloud secrets, secret.
Review the scenario above and start thinking about how an attacker might be able to exploit vulnerabilities in your environment. Then take action by digging deeper into foundational risk mitigation and secrets management strategies so you can bolster defenses and embrace the cloud with confidence.
Next up, we will examine one of the most highly coveted cloud targets – the cloud console – and why so many organizations don’t even know it’s exposed.























