
What is my identity? I’m not having an existential moment; instead, I’m asking how others recognize me. How do they know for sure that I am who I say I am?
In the physical world, we carry proof of identification to help verify our identities, and most of us have many: a passport, driver’s license, library card and more. We keep these on our person and do our best to safeguard them.
In the digital world, we have usernames and passwords — roughly 85 combinations per person. We use them to access our “identity objects,” stored by identity providers (IdPs) so we don’t have to hold them ourselves, and access everything from personal bank accounts to work emails. For example, if you’ve ever used your Google password to log in to a retail site while shopping online, you’ve used an IdP. As the IdP, Google holds your identity data and shares it with the retail site when you authorize the action.
By using an IdP, you’ve essentially shifted the responsibility of protecting your identity data to a system that is, in fact, protected by a password. Anyone who knows it, steals it or cracks it could assume your identity. Additionally, an IdP could mistakenly leak your data or even block your access to your identity and in turn, block your access to all the sites using this IdP.
A Tide Change Brings New Expectations for Personal Data Privacy
“A convergence of consumer, government, and market forces are now giving users more control over the data they generate. Instead of serving as a resource that can be freely harvested, countries in every region of the world have begun to treat personal data as an asset owned by individuals and held in trust by firms.” – Harvard Business Review
Identity theft happens every 22 seconds. Consumers are fed up and starting to question whether any third-party system should have such broad control over their personal data, and especially, their identity data. They’re also considering what could happen if this data were ever to be modified or even erased in the future. As these questions swirl, decentralized identity (DID) has emerged as an intriguing potential alternative.
The Decentralized Identity Vision
Decentralized identity, aka self-sovereign or distributed identity, is an open framework that’s being developed to help establish unique and secure access connections between parties or systems without the need for a third-party “connection broker.”
DID is designed to mimic a digital wallet of sorts, in which users store their various identities, or claims. Individuals are solely responsible for keeping their claims safe and release only the minimum information required to forge a secure, trusted connection. No passwords exchange hands; instead, biometric authentication such as a fingerprint or facial recognition is used. Meanwhile, the underlying decentralized blockchain technology works to ensure claims are cryptographically authentic and tamper proof, significantly reducing the risk of fraud.
Here’s what this looks like in action: You request claims or “verifiable credentials” from various entities, such as a transportation department or your local coffee shop, and store them in your digital wallet. Each organization or “claims issuer” creates a unique claim that contains both personal data (to prove who you are), as well as authentication data (specifying your permissions or levels of access) about you. Different entities require differing levels of attestation to enable trusted data exchange. For instance, your Starbucks claims couldn’t help you board an international flight, but it could unlock rewards and special coupons. To make sure a claim is legitimate, a claims issuer may also assume the role of “claims verifier,” such as when a police officer asks for your license and registration at a traffic stop.
By giving identity data control back to the people, DID is a compelling visionary concept. However, like all major technology shifts, it presents numerous challenges. The first is getting people on board with such a big change in their daily routines — it’s a mindset transformation will take time and a Herculean effort. Then there are technological constraints, such as standardization (just think of the long global journey to 5G and the different blockchains currently competing for dominance) and technology maturity. What happens if your digital wallet fails to back up properly or the “right to be forgotten” if you wish to eliminate your digital footprint? But perhaps the biggest hurdle of all is managing and securing the massive attack surface DID creates.
The Darker Side of DID: 5 Cybersecurity Risks
The decentralized identity attack surface can be categorized into five distinct areas:
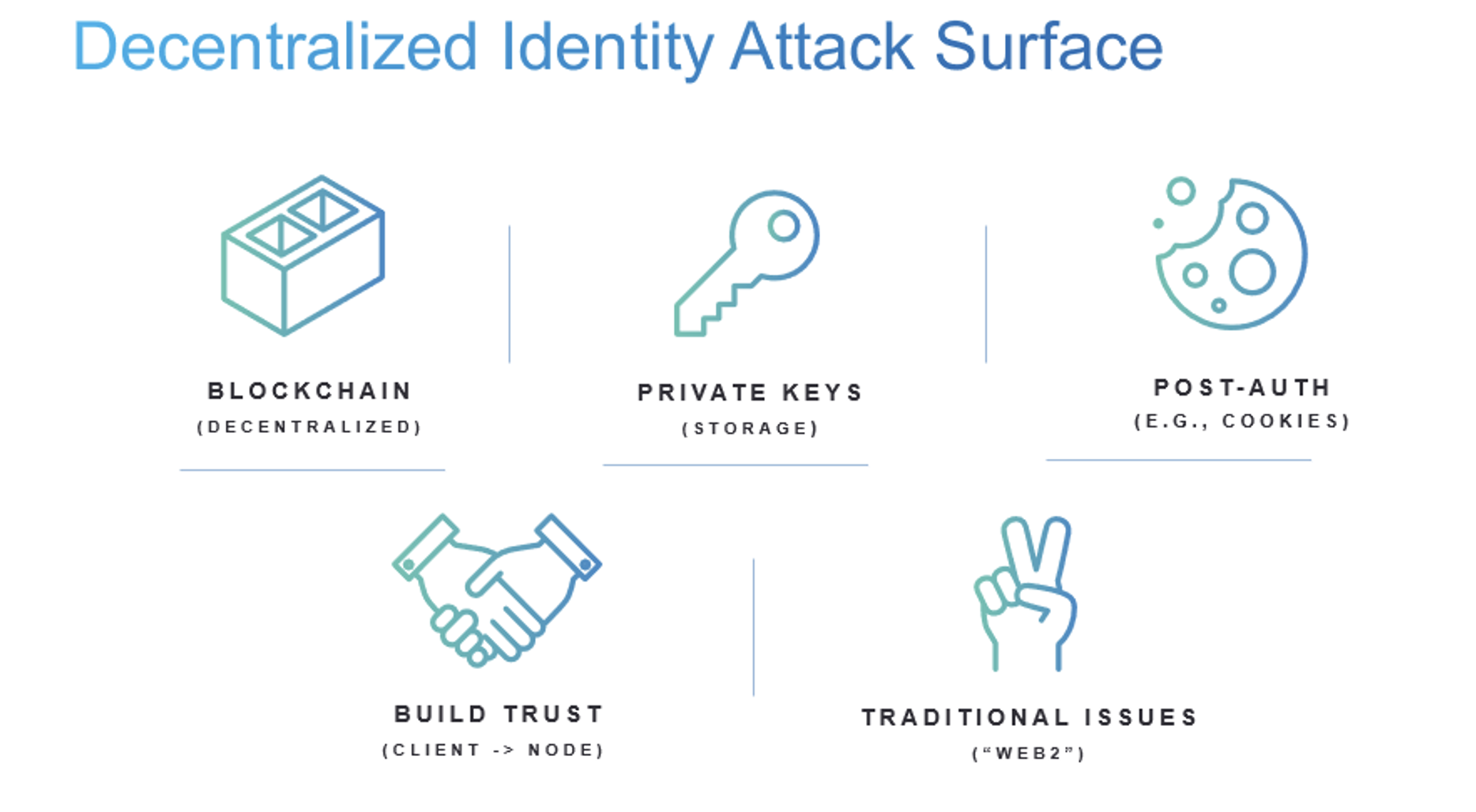
- The blockchain code itself. In decentralized systems, everything is based on a blockchain. This is what is used to store identity operations, such as creating an identity, revoking keys or restoring an identity. Every blockchain contains nodes used to validate transactions, write to it and read from it. Both the blockchain and its nodes are made up of code. As with all new software code, they are likely to contain bugs, some of which can turn out to be security issues or vulnerabilities. Every DID implementation introduces a different attack surface.
- Fallible humans hold the keys to the kingdom. At the end of the day, distributed systems are only as secure as the private keys that run them. And humans — notorious for making mistakes — are the ones storing and using those keys. In this regard, the promise of DID is a double-edged sword.
- Post-authorization cookies could be compromised. When you use a standard centralized identity, you typically get a cookie or an access token that will identify your session for the near future. Now let’s say you’ve authenticated to some service using DID. Now what? Your identity could depend on a single cookie and not on the decentralized system. If malware happens to be running on your phone or laptop, it could potentially steal that cookie or access token after the DID authentication flow is finished.
- Nodes can be used maliciously. A new security issue unique to distributed systems is the process of forging trust between a client and a node. The average person can’t read or keep track of an entire blockchain — that’s what nodes are meant to do, as well as to provide reliable data for the chain. The problem is, some nodes can be malicious, or an attacker can try to intercept someone’s communication with that node and try to modify the data. While various systems work to resolve this issue, this is an ongoing challenge across all decentralized systems, and identity systems are no exception.
- Traditional security challenges don’t disappear. Since no one lives solely in the blockchain world, every distributed system must have some degree of connection to the real world and other systems that are off the chain. These systems — from node API request handlers to bridges between ledgers and “classic” systems (i.e., relational or NoSQL databases, middleware business logic or front-end application code) — are susceptible to all the “regular” cyber threats.
Years of problematic passwords and endemic identity fraud have highlighted the need for stronger, more secure ways for people to authenticate themselves. Decentralized identity offers some exciting possibilities — but it also presents formidable cybersecurity challenges and new attack surfaces.
DID technology itself is still in its infancy stage. It will take many great minds working together to overcome significant security obstacles, but with enough time, iteration and collaboration, I’m optimistic that DID will mature into a highly effective way to prove “I am who I say I am” in the future.
This post is based on the CyberArk Impact 2022 session “Decentralized Identity: The Good, the Bad and the Ugly,” presented by Daniel Schwartzer, Chief Product Technologist, CyberArk and Shaked Reiner, Principal Security Researcher, CyberArk Labs























