Organizations use software robots or bots to automate a wide variety of business processes, from HR and finance to customer care and manufacturing. Software bots can automate and supplement human workflows and take on repetitive and lower-value work, helping organizations improve business agility, reduce costs and risks, and free up staff for higher value tasks. Advanced bots and automated agents can interpret language, engage in chats and conversations, and use machine learning algorithms to assist decision making — even make decisions independently based on criteria and learning.
Across the world, businesses of every size and industry are rolling out bots to automate operations, improve efficiencies and enable digital transformation. The latest robotic process automation (RPA) solutions from companies like UiPath, Automation Anywhere, Blue Prism and Pegasystems make it easier to build, deploy and manage software bots at scale. In a CyberArk survey of 1,000 IT decision makers, 78% of respondents said they are already investing or plan to invest in RPA technology.
Attended vs. Unattended Bots
Bots are typically one of two types: “attended” or “unattended.” Attended bots work alongside humans to augment processes. For example, an attended bot might assist an agent in a contact center working with customers to process loan applications. Unattended bots, on the other hand, carry out tasks without requiring human involvement. For example, an unattended bot might automatically process vendor invoices by matching the invoice to goods scanned entering distribution centers, along with the originating PO and order request, and then verify the discounts and the amount before approving and sending to the accounts payable system.
Giving Bots Secure Access to Resources
Just like people and applications, bots require privileged credentials to access corporate resources and protected information to perform administrative tasks. But as the use of bots increases within organizations, so do the credentials they need to perform their tasks. While this is manageable in a small number of robots, tracking and managing credentials across a number of bots can quickly become daunting unless these credentials are centrally managed. Additionally, many organizations embed privileged credentials into RPA automation scripts, making them easy prey for threat actors. Bad actors can exploit compromised privileged credentials to install malware, wage attacks or steal confidential data.
In addition, many organizations rely on manual processes to update and rotate privileged credentials — an inherently inefficient approach that goes against the mission of using automation, does not scale well and introduces additional security vulnerabilities. Compromised credentials can remain active indefinitely, exposing the business to ongoing risk.
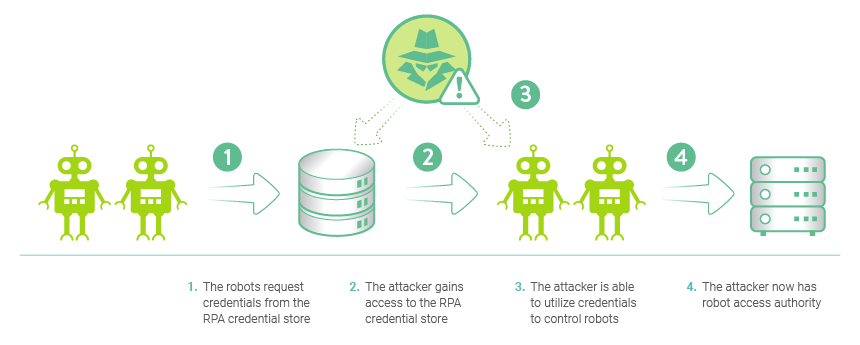
Citizen Developer Challenges
While corporate IT functions and RPA Centers of Excellence focus on developing and deploying RPA for high-value business processes, there are also many potential areas for smaller RPA deployment opportunities. RPA vendors have recognized that many smaller departments and functions can benefit from the efficiencies delivered by RPA but may not get prioritized by their organizations. To address this, RPA vendors offer no-code, drag-and-drop GUIs that make it easy for citizen developers — ordinary business users with no software development experience — to build applications. To be successful, citizen developers also need fast and easy ways to ensure their applications have secure access to high-value resources. By integrating secure access to privileged credentials directly into RPA automation workflows, organizations can simplify citizen development, while enabling security to tightly control and monitor the access provided and used by the citizen-developed bot. This helps eliminate manually intensive, time-consuming security review processes and ensures applications comply with corporate security guidelines.
Bot Security
Organizations can reduce bot security risks by removing privileged credentials from RPA scripts and using privileged access management solutions to centrally store and manage privileged credentials. By automating credential management — implementing robust privileged access security controls directly in the RPA pipeline — organizations can simplify operations, strengthen security and more efficiently scale RPA deployments. Privileged access management solutions help organizations reduce vulnerabilities and make the most of their RPA investments by making it easy for citizen developers to adhere to corporate security standards and policies.
Best-of-breed privileged assess management solutions:
- Centrally secure and manage credentials.
- Authenticate individual bots before serving up credentials to prevent impersonation, unauthorized access and malicious attacks.
- Automatically rotate credentials at regular intervals or on demand to reduce security vulnerabilities and mitigate risk.
- Encrypt privileged access credentials used by bots and safely store them in a tamper-resistant digital vault to prevent credential theft and abuse.
- Remove human intervention from the process to enable high scalability and agility and to reduce operations expense and complexity.
Additional Bot Security Best Practices
Organizations can reduce RPA security risks further by applying the principle of least privilege access to bots and by using privileged access management solutions to safeguard RPA administrative accounts.
To reduce attack surfaces and minimize risk, businesses can:
- Grant bots privileged access only to the specific applications they need to perform their tasks.
- Use a privileged access management solution to secure the RPA administrative console.
- Securely store privileged access credentials in a digital vault and rotate them automatically.
- Isolate and monitor RPA administrative sessions.