How mature is your Identity Security strategy?
Discover the Identity Security market trends and key insights from global research conducted by the Enterprise Strategy Group (ESG). Learn about the four tenets that determine the maturity of your organization’s Identity Security strategy and how to level up.
A 360° Approach to Identity Security
Four tenets to help your organization build a complete Identity Security strategy
There is a goldmine of overprivileged and under-secured human and machine identities with access to critical assets and resources. A holistic, risk-based Identity Security strategy based on least privilege is a foundational part of securing the IT environment. This approach is also imperative to thwart identity-based attacks, increasing the organization’s cyber resilience.
Identity Security Tools
Identity Security tools span management, privileged controls, governance, authentication and authorization for all types of human and machine identities.
Integration
Integration of Identity Security tools across IT and security solutions is a must to secure access to all corporate assets and the entire IT estate.
Automation
Automation ensures continuous compliance with policies, industry standards and regulations, enabling rapid responses to high-volume routine and anomalous events.
Continuous Threat Detection and Response
Continuous threat detection and response provides organizations with a solid understanding of baseline identity behaviors to better react to anomalous activity.

Identify the gaps in your Identity Security strategy
Discover market insights and recommendations to level up.
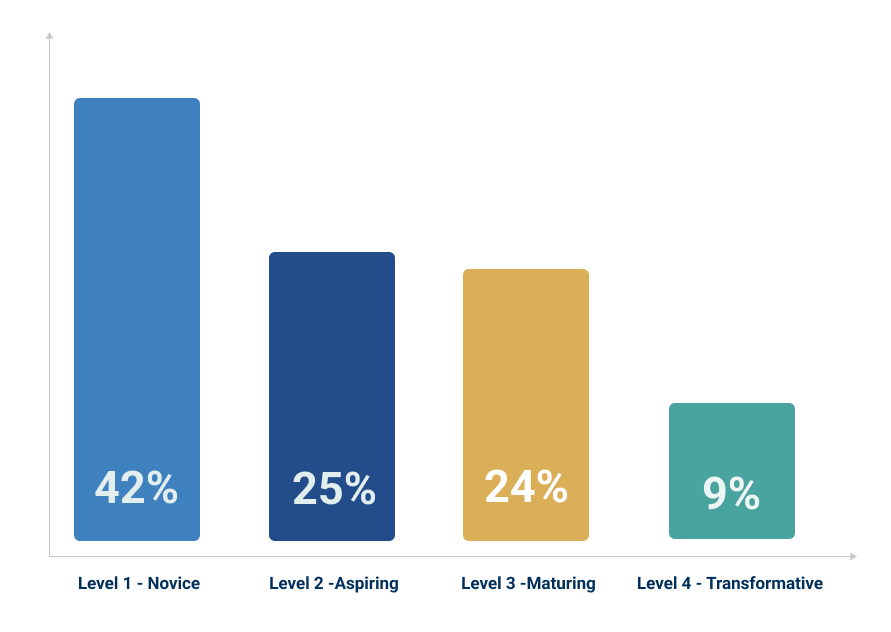
The Identity Security Maturity Levels
ESG surveyed 1,500 identity-related security experts across 16 countries to explore the business goals that drive organizational alignment and technology adoption.
What did they find? A significant correlation between the completeness of the four tenets and Identity Security maturity. Organizations on an Identity Security journey generally fall one of into four maturity levels.
Level 1 – Novice
Novice organizations invest in fewer Identity Security tools and severely lag in integration and automation them across their environment. These organizations generally lack the ability to mitigate identity-related risks in a timely manner.
A third of Novice organizations have been victims of multiple successful identity-related attacks in the last 12 months. Our research implies that nearly 40% of Novice organizations likely do not have the ability or capability to determine that they have suffered an identity-related attack.
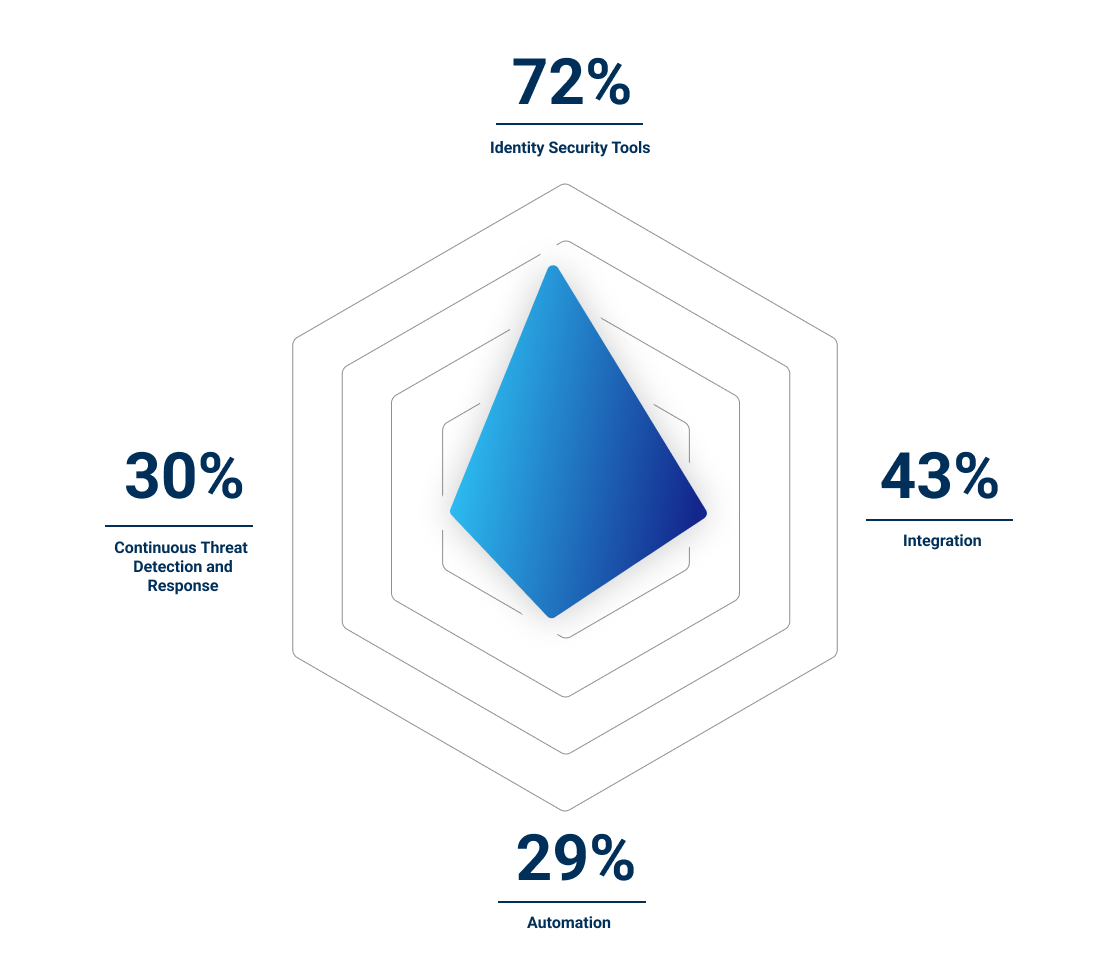
Level 2 – Aspiring
Aspiring organizations deploy and integrate a broader swath of Identity Security tools to bridge existing gaps. They are strategically focused on automating the tools and centralizing visibility and control.
In the next 12 months, Aspiring organizations are concerned about lack of real-time visibility across their enterprises and the greater possibility of cloud attacks in multi-cloud environments. They are proactively investing in cloud infrastructure entitlement management (CIEM) and multifactor authentication (MFA) capabilities.
Level 3 – Maturing
Maturing organizations have invested in nearly all required Identity Security tools, which are largely integrated and automated. These organizations prioritize improving continuous threat detection and response capabilities.
Misuse of privileged accounts and fraudulent accounts were the two main reasons that caused Maturing organizations to suffer from successful identity-related attacks. These organizations are focused on securing endpoint privileges and customer identities in the next 12 months.
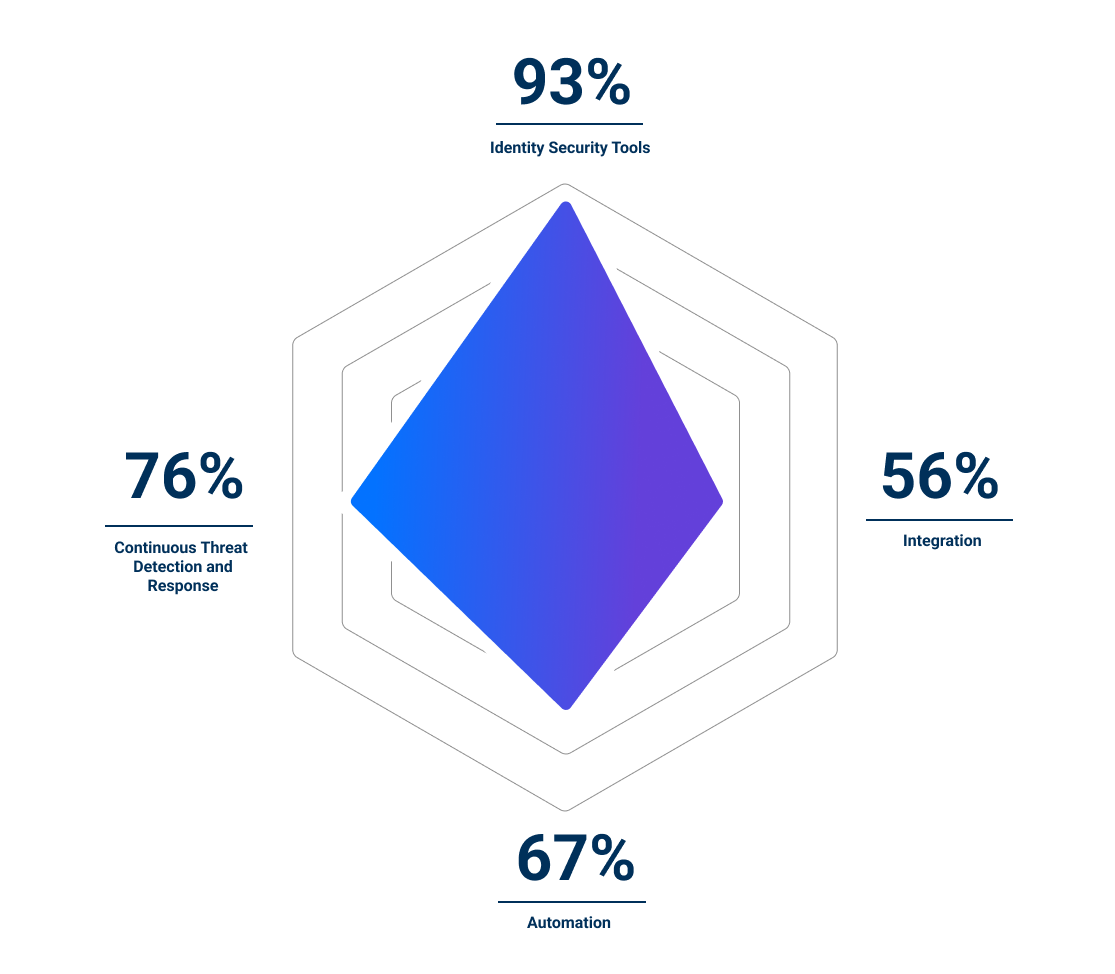
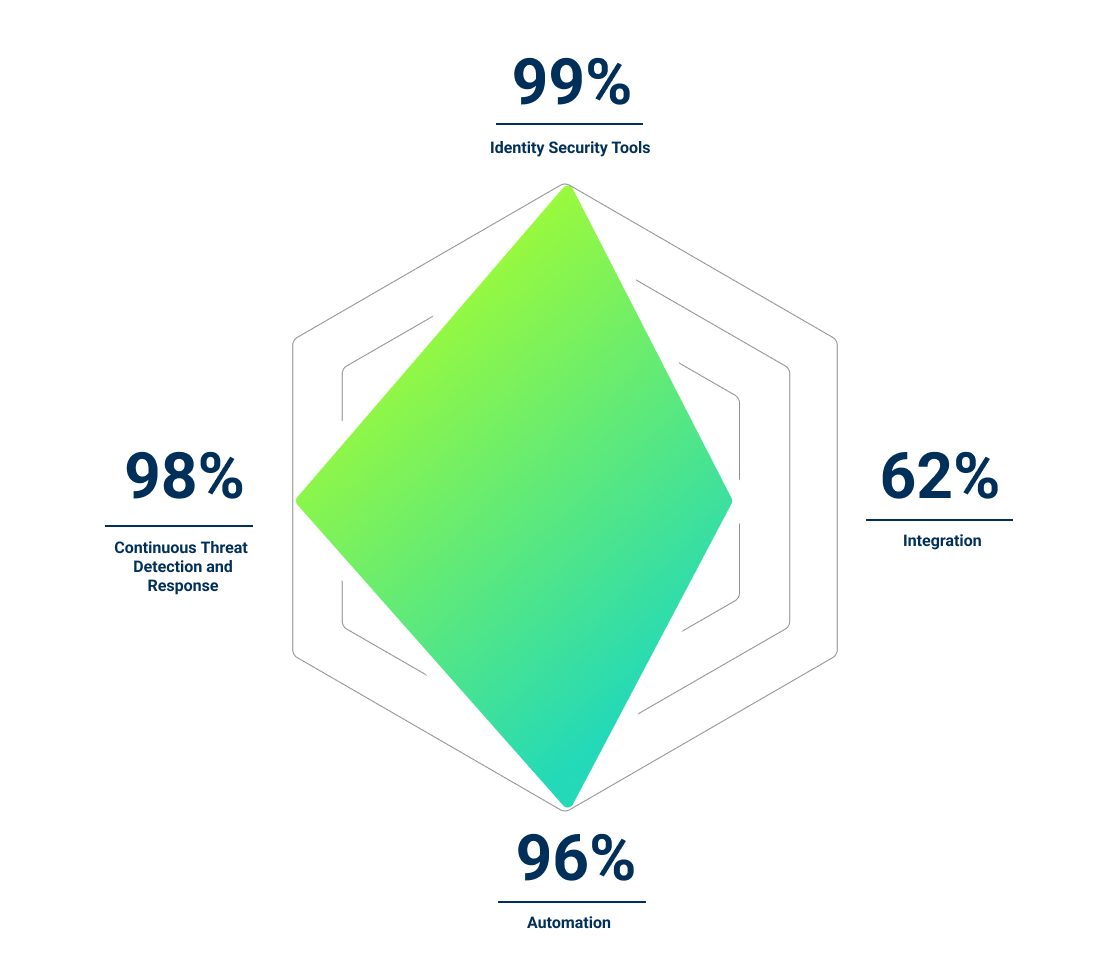
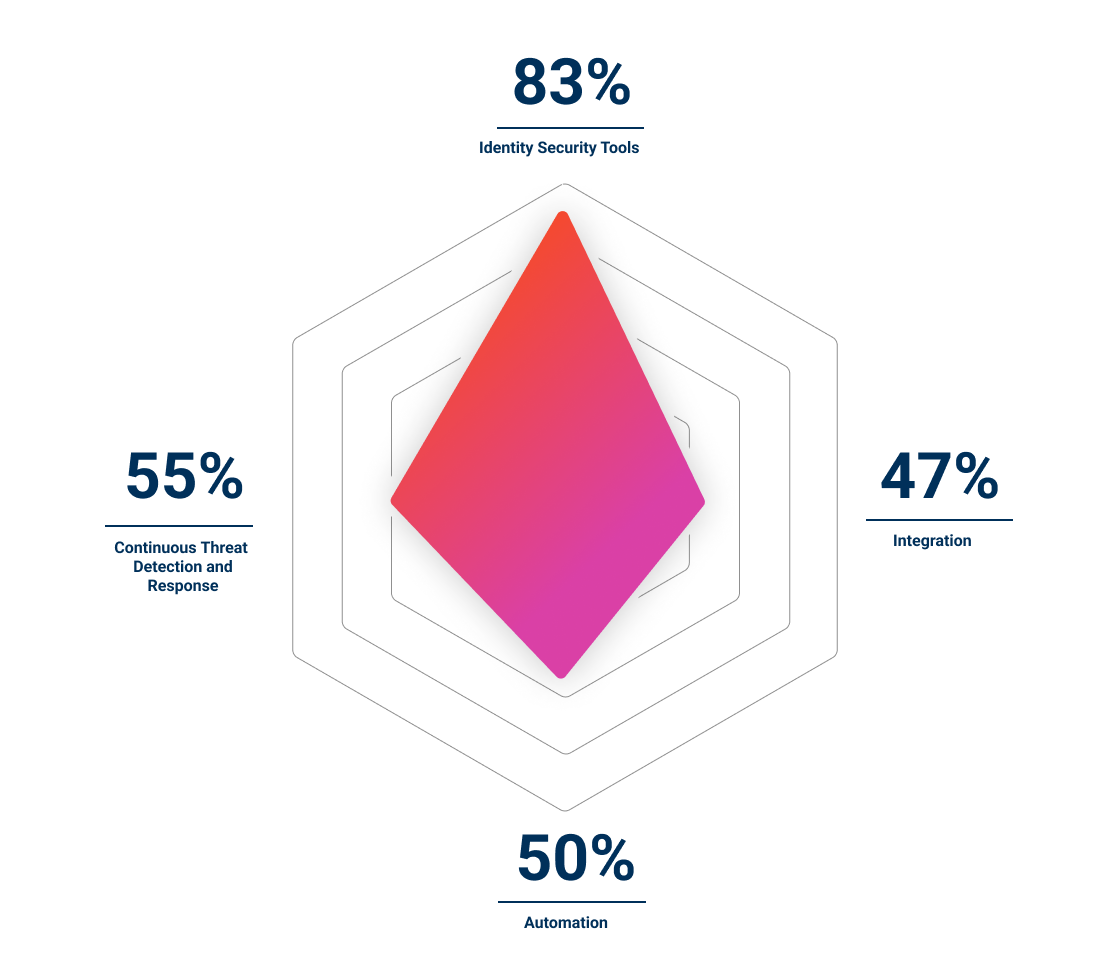
Level 4 – Transformative
Transformative organizations are strategic and purpose-driven in their investments in Identity Security. These organizations have a well-rounded focus on integrating and automating Identity Security tools and have robust continuous monitoring capabilities across their environments, enabling quick responses to cyberattacks.
Transformative organizations are nearly three times more likely to mitigate risk in a timely manner and are nearly five times more likely to respond to an audit request in less than an hour than Novice organizations.