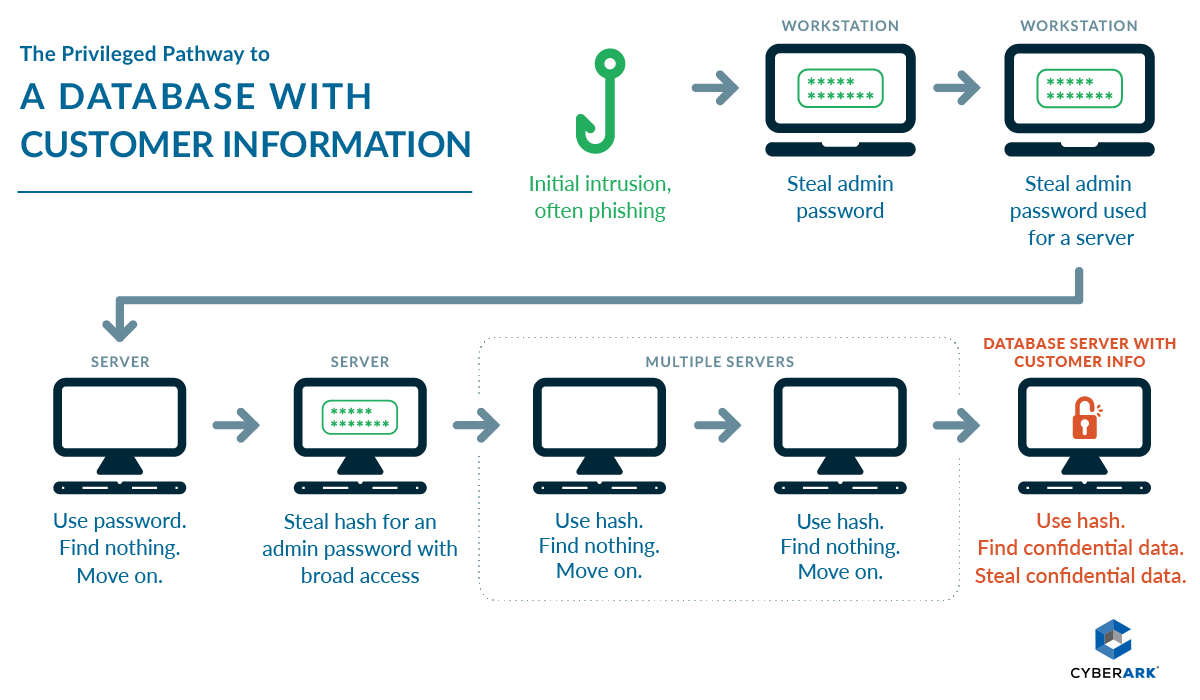
According to an article in Ars Technica, in an interview last evening, the FBI implied that the attackers who infiltrated Yahoo – including two alleged Russian FSB agents – followed a common pattern seen in many high profile cyber attacks including SWIFT and the Bangladesh Bank, the Ukraine power outage, the DNC, U.S. Office of Personnel Management (OPM) and many more. This pattern often begins with a targeted phishing attack to steal the employee’s credentials, compromise an employee’s workstation with malware, and use privileged credentials harvested from the compromised workstation to expand their attack to other assets within the enterprise.
Privileged credentials are the ultimate espionage asset – they allow attackers to quietly extend beyond their initial foothold within an organization and access its most critical data by posing as a trusted insider. If this was a spy novel, the attackers could not have done any better even if they had recruited a top-level human asset inside the organization.
In the Yahoo case, by exploiting these credentials, the attackers were able to extend their reach to compromise the Yahoo user database and use information in it to forge authentication tokens. Essentially, they were able to become ANY Yahoo user – including anyone with a Yahoo email account.
This means that the attackers could read every email, reset passwords for any website the Yahoo user may have linked to their account (such as an online banking account), or they could pose as the Yahoo user to target others with phishing emails.
According to the U.S. Department of Justice (DOJ) indictment, the attackers used this power to access the accounts of journalists, U.S. government officials, executives at prominent financial services organizations, and employees at cyber security vendors, among others. A scary reality in today’s connected world – and a major reason why information is becoming harder to trust.
This massive espionage/criminal campaign started with getting an asset inside – as in similar cases, these “assets” are privileged accounts. Many CISOs and security professionals understand that privileged accounts are the first tools adversaries seek, once within their network, to extend their reach and complete their mission. We don’t need any more reminders that shutting down the privileged account pathway must be an organizational priority.