Get Ready for 47-Day TLS Certificate Lifecycles
TLS certificate validity is shrinking. Automate certificate lifecycle management to prevent outages, reduce risk, strengthen business resilience, and streamline operations.
TLS Certificate Lifecycles Are Shrinking:
Are You Ready for 47-Day Maximum Validity?
The CA/B Forum has approved a phased policy to shorten public TLS certificate lifespans—from 398 days today to just 47 days by March 2029. The first enforcement hits in March 2026, dropping the maximum validity to 200 days, and again in 2027 to 100 days. These changes compress renewal windows and raise the stakes for teams managing public certificates. Manual processes simply can’t scale to meet this new velocity.
“The inflection point of machine identity security is now. The shift to 47-day TLS certificate lifespans is not just a technical adjustment; it’s a test of operational maturity and leadership preparedness.”
Omer Grossman, Chief Trust Officer and Head of CYBR Unit, CyberArk
A New Era for Leadership in Machine Identity Security
The move to 47-day TLS certificate lifespans is more than a compliance shift—it’s a defining moment for security and IT leaders to demonstrate operational resilience. Organizations that embrace automation and unified certificate governance now will lead with confidence as renewal velocity accelerates.
TLS Certificate Renewal Impact Calculator
Use this TLS Certificate Renewal Impact Calculator to estimate the operational burden of the 47-day mandate. Whether your organization rotates certificates every 47 days (8x/year) or aligns to a monthly renewal cadence (closer to 12x/year as used in the calculator), the volume of renewals is set to surge. Manual processes won’t scale—this is where automation delivers measurable ROI.
–
Days until 200-day certs
(March 15, 2026)
–
Days until 100-day certs
(March 15, 2027)
–
Days until 47-day certs
(March 15, 2029)
Annual Renewals
-
Total Hours
-
FTEs
-
TLS Certificate Management Has Entered a Continuous Loop
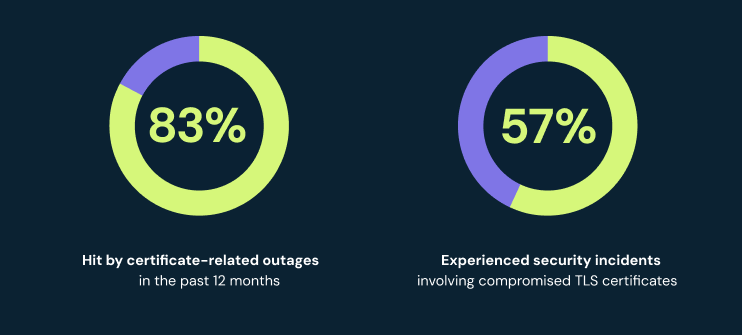
The shift to 47-day certificate lifespans is already underway—and it’s redefining operational expectations. What was a once-a-year task now recurs every few weeks, compounding risk for teams still relying on manual renewal processes. Legacy tools and manual workflows will become fundamentally unreliable and unsustainable. Without automation, most organizations will be overwhelmed long before 2029.
“All told, by the time the CA/Browser Forum’s phased timeline officially plays out, you’ll experience an eight-to-twelve-fold increase in the number of TLS certificates your teams have to manage. That means what used to be an annual checklist item is now a continuous loop.”
Kevin Bocek, SVP Innovation, CyberArk
Automate to Survive the 47-Day Certificate Transition
Automation isn’t just a future need; it’s a prerequisite for surviving each phase of the 47-day certificate transition. CyberArk Certificate Manager automates certificate lifecycle operations across hybrid, multi-cloud, and application environments to provide real-time visibility, policy enforcement, and renewal orchestration that scales. Adapt quickly, avoid fire drills, and operate securely—at every enforcement milestone—with CyberArk Certificate Manager.

“We’re massive. We’re international. And CyberArk has really helped us unify that certificate sprawl, getting it all into one system and then helping us develop solutions for automation.”
Samantha Serenko, Senior Security Engineer, Bank of America

“Through automation we’ve cut the time of the lifecycle, the time of installation, and the number of resources needed to manage those certificates”
Michael Flanders, Senior Cybersecurity Engineer, Southwest Airlines

“CyberArk has allowed my teams to focus on the security of our environment—not having to do the operational pieces. And we have peace of mind that we’re not going to experience an outage due to a certificate issue.”
Scott Barronton, CISO, Diebold Nixdorf

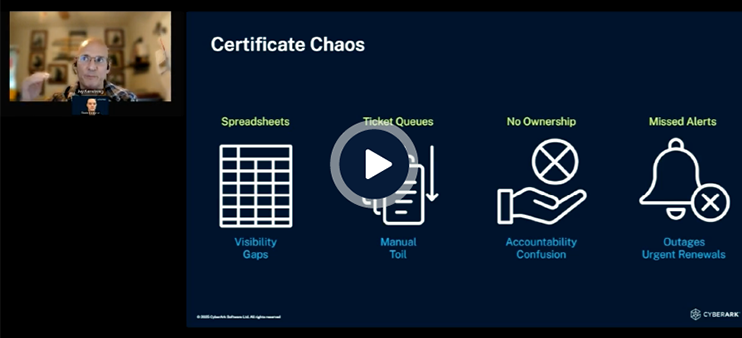
“We had a lot of problems with understanding ownership and accountability for certificates…There is no way we could do what we do today in a manual world. Without the automation that CyberArk brought to us, we couldn’t manage our identities at all.”
Alan Morton, Technical Lead for Certificate Services, BP

“We have to apply our policies to acquired companies on a regular or semi-regular basis. It [would be] a big embarrassment if a certificate expires on a public site…Our infrastructure is dynamic and inconsistent, and CyberArk has been able to handle that.”
Sherman Becraft, Information Security Advisor, Elevance Health
Discovery Scan for Public TLS Certificates
The CA/B Forum has approved a phased policy to shorten public TLS certificate lifespans—from 398 days today to just 47 days by March 2029. The first enforcement hits in March 2026, dropping the maximum validity to 200 days, and again in 2027 to 100 days. These changes compress renewal windows and raise the stakes for teams managing public certificates. This TLS certificate scan helps you get ahead—by identifying gaps in visibility and laying the groundwork for 47-day certificate lifecycles.
CyberArk’s TLS Certificate Discovery Scan quickly reveals which public-facing certificates are expired, expiring soon, misconfigured, or non-compliant—so you can take action before it disrupts your business. You’ll be able to:
- Get an inventory of your publicly trusted TLS certificates.
- Identify TLS certificates nearing expiration to prevent unplanned outages.
- Detect rogue, weak, or misconfigured TLS certificates before they trigger an outage.
- Confirm certificates are issued by approved certificate authorities and align with your security policies.
No deployment required. Just sign up with your business email (we scan the domain tied to that email) and get a detailed report powered by CyberArk Certificate Manager.
It only takes minutes to start. Results can help guide your automation and compliance strategy.