Defend against attacks
Protect against the leading cause of breaches — compromised identities and credentials.
Defend Against Attacks
Secure identities and protect what matters most
Without a true perimeter to defend, cyber breaches are inevitable. But damage isn’t. Companies that take a privilege-centric approach to securing identities are in a better position to protect themselves from wide range of attacks.
Prevent credential theft
Safeguard all privileged credentials for human and non-human identities.
Isolate threats
Adopt a Zero Trust model to prevent attackers’ lateral and vertical movement.
Enforce least privilege
Introduce just-in-time controls, granting temporary access only when needed.
Fearlessly forward
More than 50% of the Fortune 500 trust CyberArk to isolate threats and protect their most critical assets and resources.
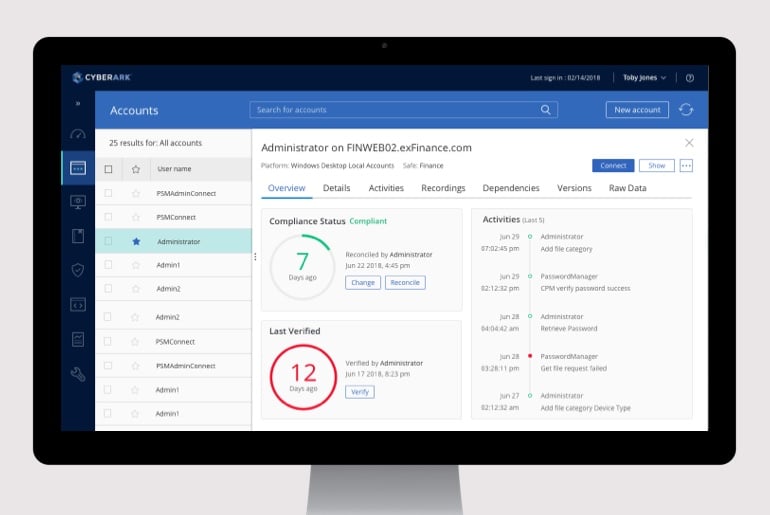
Privileged Access Manager
Isolate threats and prevent the compromise of privilege by managing accounts, credentials, and sessions and remediating risky activities.
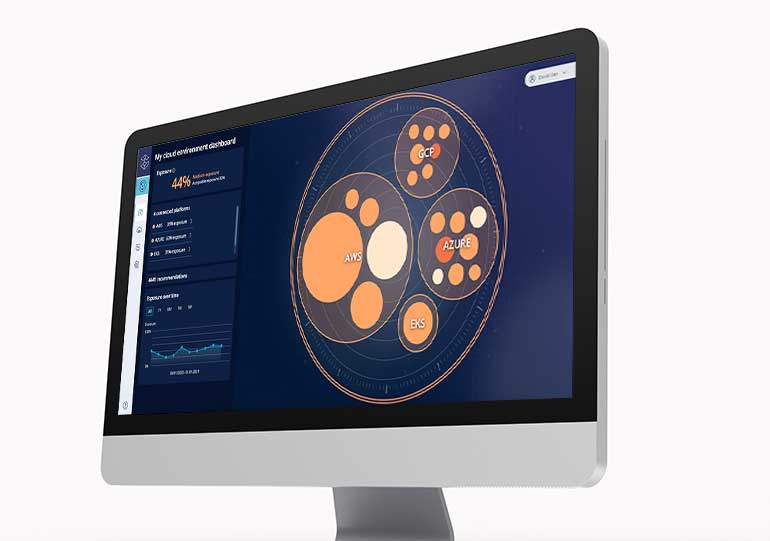
Cloud Entitlements Manager
Remediate unused and misconfigured permissions to proactively defend against internal and external threats.
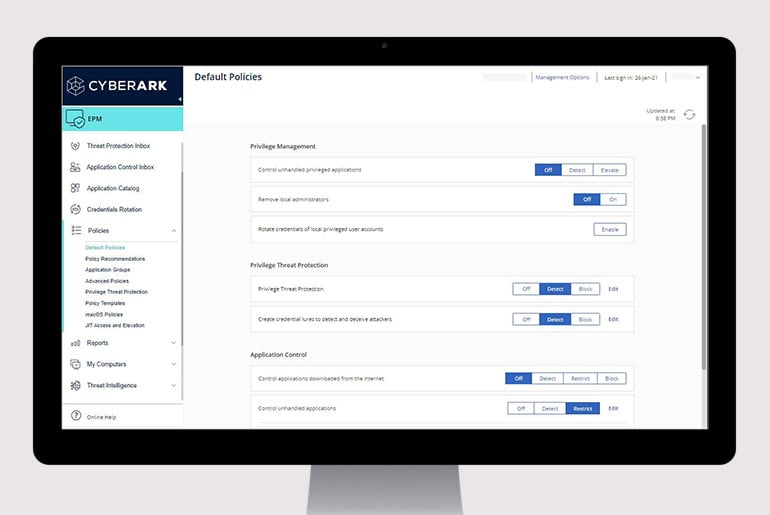
Endpoint Privilege Manager
Enforce least privilege, control applications, and prevent credential theft on Windows and Mac desktops and Windows servers to contain attacks.
Multi-Factor Authentication
Validate identities with strong AI powered, risk aware passwordless.


Vendor Privileged Access Manager
Securely connect remote vendors to your organization with cloud-based, biometric authentication via smart phones.
Identity security fundamentals

Identity Security: Why it Matters and Why Now
Put Identity Security first without putting productivity second.
Secure from all ends
Here’s just a few more ways we can help you move fearlessly forward in a digital world.
Drive operational efficiencies
Reduce complexity and burden on IT while improving protection of the business.
Enable the digital business
Secure access to business apps for human and machine identities.
Stop ransomware
Prevent lateral movement with 100% success against more than 3 million forms of ransomware.
Explore
related
resources
Request a demo
Protect against the leading cause of data breaches
Safeguard your most critical business assets
Partner with the established leader in privileged access